You've heard clients use "vulnerability scan" and "penetration test" interchangeably. Big mistake. One is a checklist, the other is a simulated heist. Knowing the difference isn't just a technicality it's what makes you the security expert they trust.
When a client needs to prove they're secure for SOC 2 or PCI DSS compliance, pushing a simple automated scan is a fast way to lose credibility. They're not asking for a list of potential problems; they need to know if someone can actually break in and do damage.
For MSPs, vCISOs, and GRC companies, this is where you step up. You need to guide them to the right test for the right reason. One finds unlocked doors; the other proves a thief can walk through them, steal the crown jewels, and walk out.
Vulnerability Scans vs. Pentests: What Do Your Clients Actually Need?
The difference is breadth vs. depth.
A vulnerability assessment is all about breadth. It's an automated scanner sweeping across a client's network or apps. The tool flags known vulnerabilities, catches missing patches, and points out common misconfigurations. It's fast, relatively cheap, and spits out a big list of potential issues, usually prioritized by a generic CVSS score.
A penetration test, on the other hand, is all about depth. This is a targeted, manual pentesting effort where a real ethical hacker simulates an attack. They use creativity and critical thinking to chain vulnerabilities together, bypass security controls, and demonstrate actual business impact. This is what auditors and regulators want to see.
A vulnerability scan tells you a door is unlocked. A penetration test shows you someone walking through that door, stealing sensitive data, and leaving a backdoor for later.
A Quick Breakdown
This comparison chart gives you a clear look at the key differences in testing depth, the time required, and what you can expect to invest.
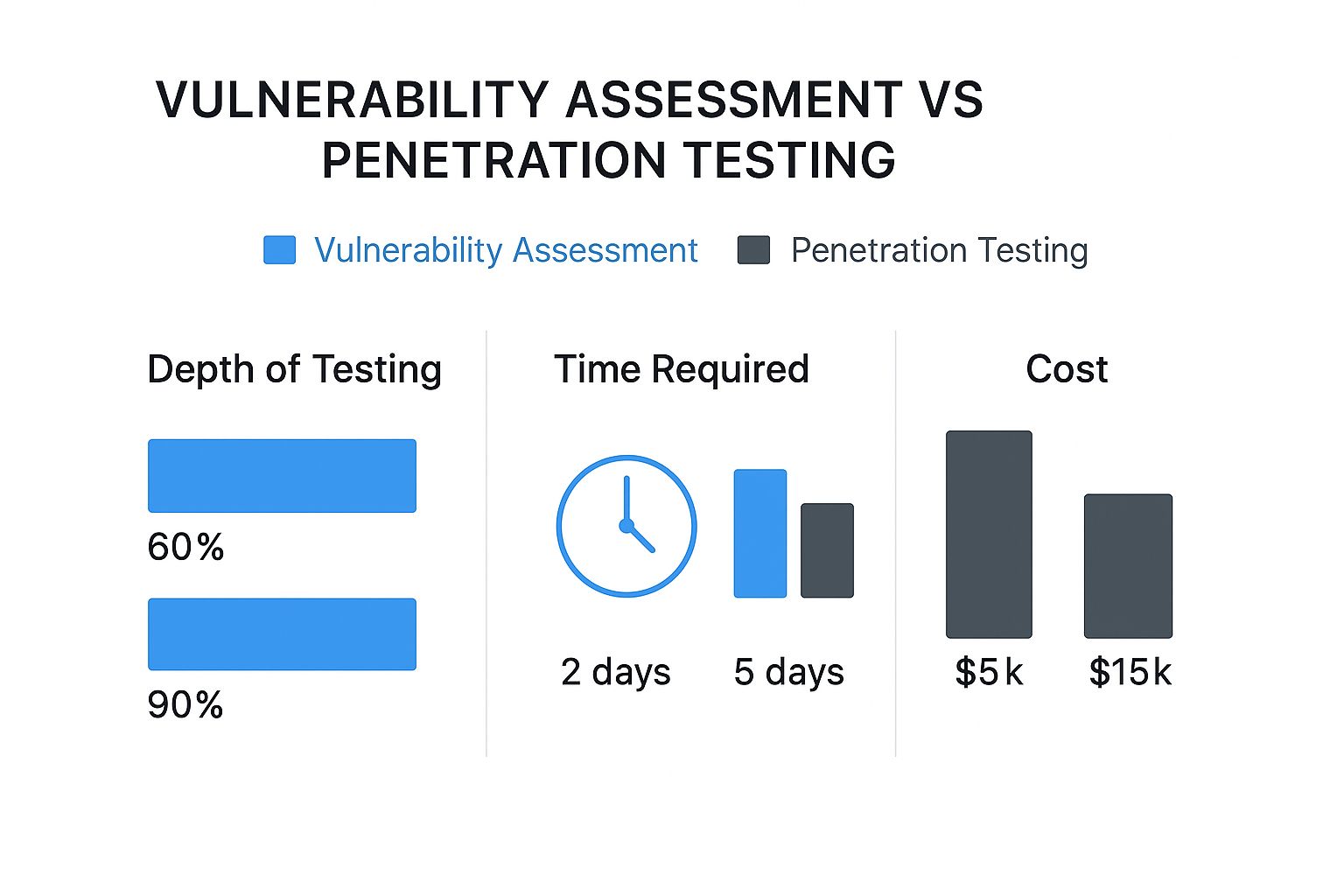
While a vulnerability assessment provides a valuable baseline, a pentest delivers a much deeper, more impactful analysis that easily justifies the investment for compliance-driven clients.
Vulnerability assessments are great for covering a lot of ground quickly with automated tools. In contrast, pentesting focuses on depth, combining expert manual analysis with specialized tools to simulate real-world attacks, validate exploits, and show their true business impact. For a closer look at the scanning process itself, check out our guide on security vulnerability scanning.
Comparing Pentesting Methodologies: Manual vs. Automated

Let's get into the weeds of how these two tests actually work. The difference in methodology is what creates the massive gap in value between a basic scan and a real manual pentesting engagement. One relies on a machine, the other on a human mind.
A vulnerability assessment is pure automation. It’s a tool—think Nessus, Qualys, or OpenVAS—throwing everything it knows at a target to see what sticks. The scanner just runs down a checklist, comparing your client's systems against a huge database of known Common Vulnerabilities and Exposures (CVEs).
It’s programmed to spot the easy stuff:
- Outdated software with well-known exploits.
- Common server and firewall misconfigurations.
- Missing security patches that leave a door wide open.
The result? A long, noisy report prioritized by a generic CVSS score. It’s a decent starting point for basic patch management, but it’s completely devoid of actual risk context. It finds theoretical weaknesses, not a proven, exploitable path an attacker could actually take.
The Human Element in Pentesting
This is where penetration testing completely changes the game. A pentester might kick things off with a scan, but that’s just the recon. The real work is manual, driven by an adversarial mindset that no tool can replicate. A pentester isn't just looking for a list of CVEs; they're looking for a way in.
Instead of just flagging a weak password policy, a pentester will actively try to brute-force accounts. They don’t just find an outdated server component; they’ll try to build an exploit for it, breach the server, and then see where they can pivot to next inside the network. This hands-on approach is the only way to find business logic flaws that automated tools are completely blind to.
A vulnerability scan gives you a map of all the unlocked doors and windows in a building. A penetration test proves a burglar can get through a specific window, bypass the alarm, and steal the most valuable assets without anyone noticing.
The outcome of a penetration test is fundamentally different. You don't get a giant list of "maybes." You get a concise, actionable report detailing the exact steps the tester took to compromise the system. It demonstrates real-world business risk—what an attacker could actually do. For a deep dive into the phases of this process, see our complete guide on what penetration testing is.
From Automated Noise to Actionable Intelligence
This distinction is critical for GRC firms and vCISOs. A scan report is often overwhelming, packed with false positives that create busywork. A pentest report, on the other hand, tells a clear story of an attack, making it easy to justify remediation efforts to stakeholders and auditors for SOC 2 or ISO 27001.
Considering the average time to even detect a data breach is reportedly over 200 days, you can see why running frequent scans is important. But a penetration test cuts through that noise. It actively exploits those gaps to show exactly what's at stake, offering undeniable proof that an attack path is viable.
As an MSP, presenting that kind of clear-cut evidence to a client is far more powerful than just handing them a 100-page scan result and walking away.
Choosing the Right Test: When to Recommend a Scan vs a Pentest

Knowing when to pitch a scan versus a manual pentesting engagement is what separates the strategic partners from the everyday vendors. It’s all about matching the right tool to the right job. For your clients, the stakes are high, and this is exactly where you, as an MSP or vCISO, prove your worth.
Think of a vulnerability assessment as a routine health check-up. It's proactive, ongoing work that’s just good security hygiene. You should be recommending these to clients on a regular schedule—think monthly or quarterly.
These frequent scans are perfect for:
- Continuous Monitoring: Catching new vulnerabilities as they pop up.
- Patch Verification: Making sure your remediation work actually stuck.
- Basic Security Posture: Giving you a security baseline to measure against over time.
A regular scan is the foundation. It’s affordable, automated, and gives you that wide-angle view of potential issues before they spiral. But it’s only one piece of the puzzle.
High-Stakes Scenarios Demand a Manual Pentest
A penetration test is the specialist you call in when things get serious. This isn't a routine check-up; this is a full-blown stress test designed to answer one critical question: can a determined attacker break in and cause real damage?
You recommend a pentest when the client absolutely cannot afford a security failure. It’s for when they need to go beyond a simple checklist and run a real-world fire drill on their defenses.
A vulnerability scan finds the ingredients for a fire—like faulty wiring or flammable materials. A penetration test is the controlled burn that shows you exactly how a fire would spread and what it would destroy.
For GRC firms and security-focused resellers, nailing down these trigger points is key to having high-value conversations and closing bigger, more meaningful deals.
Key Triggers for a Penetration Test
Here are the specific scenarios where a penetration test is non-negotiable. If a client brings up any of these, it’s your cue to start talking about manual pentesting.
- Meeting Compliance Mandates: This is the big one. Frameworks like SOC 2, PCI DSS, HIPAA, and ISO 27001 don’t just want a list of vulnerabilities. They demand proof that your client's security controls hold up against a real-world attack. Auditors are looking for the depth only a pentest provides.
- Major Infrastructure Changes: Did the client just migrate to a new cloud environment? Deploy a new firewall? Roll out a major application update? Any significant change introduces new variables and potential security gaps. A pentest validates that the new architecture is actually secure.
- Annual Security Validation: At a minimum, every mature organization should be conducting a penetration test annually. Threats evolve, attacker tactics change, and systems degrade. An annual test is best practice for making sure defenses can withstand modern attack techniques.
- Pre-Product Launch: Before a new application or service goes live, a pentest should be the final quality gate. The last thing a client wants is a Day One breach that torches their reputation.
By positioning the right test for the right situation, you cement your firm as an indispensable security advisor. It shows you understand not just the tech, but the business and compliance drivers behind it all. Our guide to threat and vulnerability management offers more context on building a complete security program. This is how you go from being just another reseller to a true partner.
Matching Security Services to Compliance Frameworks
Compliance isn't just a box to check—it's a massive budget driver. If your clients operate in finance, healthcare, or tech, they’re already being told they need security testing. The problem is, they often don’t know which kind.
For clients dealing with PCI DSS, requirement 11.3 is crystal clear: they need quarterly vulnerability assessments and an annual penetration test. It’s not an either/or situation.
Then you have SOC 2. Auditors look at criteria CC4.1 (vulnerability management) and CC7.1 (incident response), and they expect to see evidence from both routine scans and hands-on exploit validation. And for HIPAA? The Security Rule requires a detailed risk assessment, but any seasoned auditor will tell you they want to see proof of a pentest to be sure technical safeguards actually work.
Even ISO 27001 gets in on the action with Annex A.12.6.1, which demands that technical vulnerabilities are actively managed. For an MSP or vCISO offering white label pentesting, this is your sweet spot. You can help clients satisfy all these requirements without them having to build an in-house team.
Knowing how to align the right test with the right compliance rule cuts through audit confusion. It makes the sales conversation easier and positions you as the security strategist they can't afford to lose.
The Lowdown on Compliance Requirements
Every framework has its own lingo for testing mandates. Your job as an MSP is to translate that into a clear service offering.
With PCI DSS, it's not just about running a scan. Requirement 11.3 calls for a whole suite of tests—external, internal, and authenticated scans, plus a manual pentest to see if a real attacker could chain vulnerabilities together.
SOC 2 is all about documented proof. The trust services criteria require evidence that you’re on top of vulnerabilities. Scans show you’re doing the day-to-day maintenance, while a pentest proves your defenses can withstand a real attack.
Mixing both services is the only way to keep auditors happy. When you can map your services directly to their compliance framework, pricing conversations become a whole lot simpler.
Scans vs. Pentests in the Real World
So, how do you decide what to recommend? It all comes down to the client’s risk assessment and their audit deadlines. You need to align the testing frequency with their reporting cycles and any go-live dates for new applications or infrastructure.
Scans catch the low-hanging fruit. Pentests simulate an attacker’s mindset to find the critical breach paths that could bring a business down.
A good rule of thumb is to use continuous vulnerability assessments for general security hygiene. Think of it as preventative maintenance. Then, schedule a manual pentesting engagement before each major compliance audit or any significant system change. This two-pronged approach gives you both breadth and depth.
How to Position White Label Services
As a channel-only partner, we never compete with our MSP and vCISO clients. You get access to affordable manual pentesting, quick turnarounds, and branded reports that you can deliver as your own. This model lets you instantly expand your security offerings with zero overhead.
When the vulnerability assessment vs. penetration testing conversation comes up, a white-label partner is your ace in the hole. You can clearly explain what each service does, align it directly to audit requirements, and get your clients exactly what they need to pass.
MSP Compliance Testing Cheat Sheet
Navigating the alphabet soup of compliance frameworks can be a headache. We put together this quick cheat sheet to help you guide client conversations.
When you can confidently match security services to compliance frameworks, you stop being just another vendor and become an indispensable advisor.
Best Practices for Nailing Compliance Testing
- Run automated scans at least monthly. This maintains a solid security baseline.
- Schedule manual pentests annually or after major system changes. This is for validating the controls that protect critical business assets.
- Don't forget the human element. Auditors are increasingly looking for social engineering and phishing tests.
- Mix it up. Integrating AI pentesting with manual tests can speed up discovery, while adding social engineering uncovers risks that scanners will always miss.
Why the Pentesting Market Is Broken for the Channel

The traditional pentesting market is a nightmare for the channel. As an MSP or vCISO, you’re on the front lines scrambling to get clients what they need for compliance, but you keep hitting roadblocks thrown up by legacy security firms.
These old-school providers are slow, overpriced, and often hand over reports that are barely better than what an automated scanner spits out. It’s a broken system that causes friction instead of fixing problems.
The Big Three Problems with Legacy Pentesters
The frustration boils down to three core issues. First, the pricing is out of control. Legacy firms charge rates that make it impossible for you to offer affordable testing, squeezing your margins and making it a tough sell.
Second, the lead times are a joke. A six to eight-week wait just to start a test is unacceptable when your client has a SOC 2 or PCI DSS audit deadline breathing down their neck. That kind of delay puts your client relationships on the line.
And finally, the quality is often suspect. After all that waiting and paying, you might get a report that’s just a glorified vulnerability scan—packed with noise, false positives, and zero actionable business context. It completely misses the point of a real manual pentesting engagement.
The old guard of pentesting isn't built for the channel. They see MSPs as competitors or one-off sales, not partners. Their business model is designed to keep you out of the loop and maximize their own profits.
A Model Built for You, the Reseller
We saw this mess and built something better from the ground up, exclusively for the channel. We are a channel-only partner. That means one simple thing: we never compete with you. Period. Our success is tied directly to yours.
We took the old model and flipped it on its head to solve the pain points that hold MSPs back.
- Affordable, Transparent Pricing: We give you clear, reseller-friendly pricing. This protects your margins so you can build a profitable security practice. No smoke and mirrors, just straightforward costs.
- Rapid Turnaround Times: Forget waiting for months. We deliver fast, high-quality manual pentesting that fits your clients' tight deadlines. You can close deals and meet compliance requirements without the stress.
- True White Label Pentesting: Our reports are your reports. We deliver comprehensive, high-quality documentation that you can brand as your own, cementing your role as the go-to security expert for your clients.
This approach changes penetration testing from a high-friction, low-margin service into a powerful tool for your business. It lets you confidently navigate the vulnerability assessment vs penetration testing conversation, meet any GRC requirement, and build deeper trust with your clients. You get the expertise of a dedicated testing team without any of the overhead or channel conflict.
Frequently Asked Questions
You've got questions, we've got answers. Here’s a quick rundown of the most common things we hear from MSPs and vCISOs about security testing. Use this to guide your client conversations.
Can a Vulnerability Scan Replace a Penetration Test for Compliance?
Absolutely not. This is probably the biggest myth in security. While vulnerability scans are a piece of the compliance puzzle—like the quarterly scans required by PCI DSS they don’t come close to meeting the requirement for a real penetration test.
Frameworks like SOC 2, PCI DSS, and auditor expectations for HIPAA and ISO 27001 demand pentesting for one reason: they need proof. They want to see a simulated, real-world attack to confirm that security controls actually hold up under pressure.
An automated scan spits out a list of potential issues. A penetration test proves those issues can be exploited to cause real damage. That's the proof auditors are looking for.
How Often Should My Clients Get a Penetration Test?
The gold standard is at least once a year. Think of it as an annual security physical. Threats evolve, attacker tactics shift, and your clients' environments are never static.
Beyond the annual check-up, a few key events should immediately trigger a pentest:
- Major Infrastructure Changes: Moving to a new cloud provider, rolling out new firewalls, or a big network redesign all create new, untested attack surfaces.
- A New Product Launch: The last thing a client wants is for their shiny new app to get breached on day one.
- Specific Compliance Mandates: Some contracts or regulations might require more frequent testing.
As their trusted reseller or advisor, it's your job to flag these high-stakes moments and recommend a test.
What Is the Main Benefit of Manual Pentesting Over an Automated One?
One word: brains. The human element is the game-changer. An automated tool is just a machine running down a checklist. It can only spot known vulnerabilities based on signatures it already has. It’s predictable and can’t think creatively.
A manual pentesting expert, on the other hand, thinks like a real attacker. They bring intuition, creativity, and an adversarial mindset to the job.
An automated tool will tell you a window is unlocked. A manual pentester will not only climb through that window but also figure out how to chain that access with a weak internal password to get to the CEO's laptop. That’s the difference.
A human tester can:
- Spot complex business logic flaws that scanners are completely blind to.
- Chain together multiple low-risk vulnerabilities to create a critical exploit path.
- Adapt their attack on the fly based on what they discover about the target's defenses.
This is why manual pentesting is the only way to get a true picture of an organization's risk assessment.
How Does White Label Pentesting Help My MSP Business?
White label pentesting is a massive force multiplier for your business. It lets you sell high-demand, high-margin security services under your own brand without the insane cost of building an in-house team of certified ethical hackers.
For any MSP, vCISO, or GRC firm, it's a no-brainer.
First, it instantly elevates your status to a comprehensive security partner. You’re not just managing their IT; you're handling advanced security validation for critical needs like SOC 2 and HIPAA compliance.
Second, it opens up a powerful new recurring revenue stream. You can package our affordable pentests into your existing service bundles, making your clients stickier and boosting your bottom line.
And finally, it lets you meet client compliance needs without sending them to another company who might try to poach them. You keep control of the entire relationship.
Are Pentesting and Red Teaming the Same Thing?
Nope, different tools for different jobs. A penetration test has a clearly defined scope—like a specific web app or network—and a set timeline. The goal is to find and exploit as many vulnerabilities as possible within those boundaries.
A red team engagement is a much broader, objective-driven simulation. The goal isn't just to find vulnerabilities; it's to test the organization's entire detection and response capability (the blue team). It’s a full-on simulated war, often lasting weeks or months, with only a handful of people in the client's organization even knowing it's happening.
For most commercial and compliance-driven needs, a penetration test is what your clients are actually asking for.
What Should I Look for in a Pentesting Partner?
Finding the right partner is everything. The market is full of firms that talk a big game but fall short. As a channel-focused business, you need a partner who gets your model and is built to help you succeed, not compete with you.
Here’s what to look for:
- Channel-Only Focus: This is non-negotiable. You need a partner who will never go after your clients.
- A Focus on Manual Pentesting: Make sure they aren’t just rebranding automated scan reports. Ask for proof of their manual methodology.
- Fast, Reliable Turnaround: You can’t afford to wait six weeks for a report when your client's audit is next month.
- High-Quality, White-Labeled Reports: The final report should be something you're proud to put your logo on—clear, actionable, and professional.
Choosing the right partner turns pentesting from a potential headache into a profitable, strategic part of your service offering.
Ready to stop dealing with broken pentesting models and partner with a firm that was built for the channel? MSP Pentesting offers affordable, manual, and white label pentesting with fast turnarounds.


.avif)
.png)
.png)
.png)

