The rise of AI-based and automated penetration testing tools has made it easier than ever to check a box for SOC 2 pentest control. Platforms spin up scans in minutes, deliver a report instantly, and call it a pentest.
The reality? For MSPs, vCISOs, and SOC 2 advisory firms, these tools often fall short where it matters most: the report itself.
If you're selling managed services or security consulting, the report is what your client sees, trusts, and uses to drive remediation. A bad report means extra work, unclear next steps, and miscommunication between technical teams and auditors. That’s why understanding the real gap between automated and manual pentesting especially in the reporting layer is critical to protecting clients and building lasting partnerships.
Manual Reports Have Screenshots. AI Reports Rarely Do.
This might sound minor until you're the MSP responsible for remediation.
Manual penetration testing reports include annotated screenshots showing exactly where and how a vulnerability was found. These screenshots are more than just proof they serve as a roadmap for IT teams and auditors trying to reproduce the issue.
By contrast, many automated pentesting tools output long tables of “possible” vulnerabilities pulled from scanners like Nessus or OpenVAS. They rarely show the attack in action. Worse, they often label issues as “critical” without validating exploitability in context.
Here’s a side-by-side example from a sample engagement:
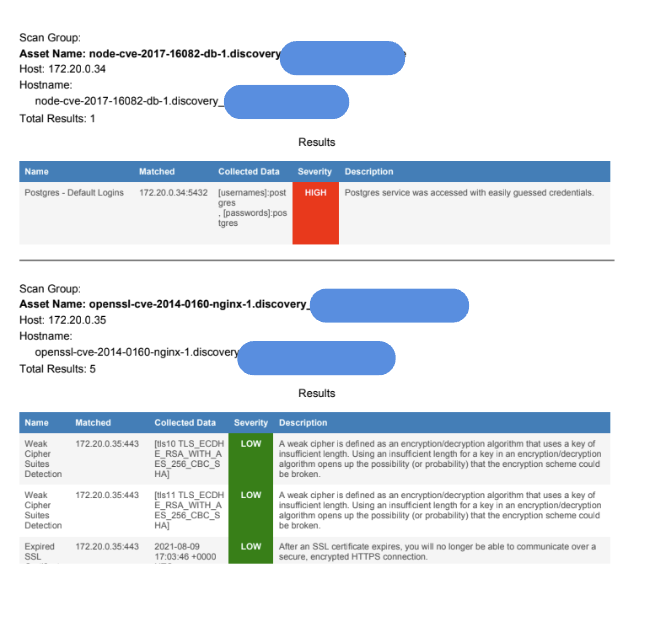
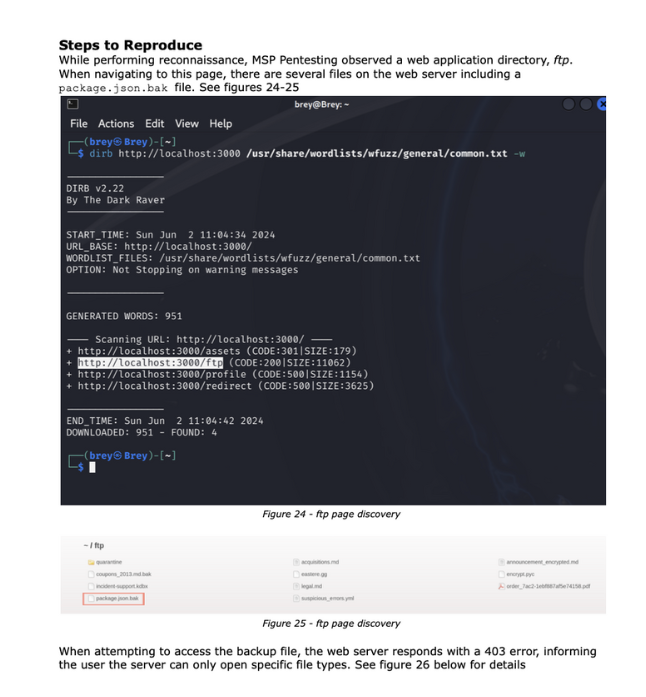
Without visuals, your team is stuck reverse-engineering what the scanner meant. That’s wasted time and risk your client can’t afford during an audit cycle.
Step-by-Step Remediation vs “Generic Guidance”
Manual pentesting reports provide clear, step-by-step remediation advice specific to your stack, tools, and environment. They explain not just what to fix, but why it matters, how the tester exploited it, and what business impact it could’ve caused.
AI-generated reports? They often paste in vendor documentation or generic advice like “apply latest patch” or “enable MFA” which is only helpful if you already know where and how to do it.
This matters especially for MSPs who need to pass findings and instructions directly to junior sysadmins or client-side developers. It’s also important for vCISOs who need executive summaries and audit documentation that map directly to trust services criteria or control frameworks.
AI Has Its Place. But It Isn’t a Replacement.
We’re not against automation. In fact, we use AI-enhanced testing as part of our own internal toolkit. For many small businesses that can’t afford full-scale manual pentesting, an automated scan is a helpful start—especially when paired with vCISO services or quarterly vulnerability management.
But if Nessus finds more issues than your “AI pentest” report... that’s not a pentest. That’s a scan with lipstick on.
True pentesting involves human decision-making, chaining findings together, lateral movement, and proving real-world impact. Without that, your report doesn’t hold up in front of auditors or clients.
Whether you're an MSP managing dozens of clients or a vCISO guiding security investments, seeing both styles side-by-side will show you exactly where your current vendor stands.
And if you're stuck translating vague reports into actual remediation plans we can help.


.avif)
.png)
.png)
.png)

