If you're an MSP, your cybersecurity strategy can't just be about protecting clients. It's about protecting your entire business from becoming a single point of catastrophic failure. Hackers are actively targeting you. Why? Because compromising one MSP gives them the keys to dozens, sometimes hundreds, of downstream clients.
This guide is your playbook for turning that high-stakes risk into a rock-solid defense and a massive revenue stream.
Why MSPs Are a Hacker's Favorite Target
MSPs are a goldmine for attackers. Your position as the central IT hub for multiple clients makes you an incredibly valuable target.
Think about it from a hacker's perspective: Why spend weeks trying to breach ten individual companies when they can hit one MSP and get access to all of them at once? This isn't fear-mongering; it's a strategic reality check.
This exact tactic is known as a supply chain attack, and it’s crippling the industry. A single breach at an MSP can cascade into a complete disaster for your entire client base, causing massive financial and reputational damage. The stakes have never been higher.
The Growing Threat Landscape
Attackers aren't just focused on huge enterprises anymore. They’ve figured out that MSPs, vCISOs, and other IT resellers hold the administrative credentials and remote access tools for a whole portfolio of businesses. Compromising your remote monitoring and management (RMM) tool is the ultimate prize—it gives them god-mode access across every client network you manage.
The US cybersecurity market hit $77.2 billion in 2024 and is projected to nearly triple to $236.04 billion by 2034. That explosion is fueled by relentless ransomware and data breaches, with attackers zeroing in on service providers as the most efficient way in. You can read more about the cybersecurity market growth and what it means for the channel.
This isn't just a technical problem; it's a business model vulnerability. Your greatest asset—centralized management of many clients—is also your biggest liability if not properly secured.
Evolving Beyond Basic Security
Your old-school security stack—antivirus and firewalls—just isn't enough anymore. The threats have evolved, and your defense has to evolve with them. That means getting out of a reactive, checkbox security mindset and adopting a truly proactive posture.
Here’s what that looks like in the real world:
- Proactive Threat Hunting: You're actively searching for threats inside your network and your clients' networks instead of waiting for an alert to pop up.
- Rigorous Testing: You're bringing in services like manual pentesting to simulate what a real attacker would do and find the vulnerabilities that automated scanners always miss.
- Compliance Readiness: You're actively helping clients meet tough frameworks like SOC 2 and HIPAA, which demand validated security controls that you can prove are working.
This guide will serve as your playbook for turning that huge vulnerability into your greatest strength. We'll show you how to build a cybersecurity for MSPs strategy that not only protects you but also drives serious business growth.
Building a Security Stack That Actually Protects Clients

Throwing a random collection of security tools at a client’s network isn't a strategy. Too many MSPs fall into the trap of selling products instead of solutions, leaving dangerous gaps between their firewall, antivirus, and backup systems. This disjointed approach creates a false sense of security that skilled attackers are happy to exploit.
A modern security stack isn't just a list of software licenses; it's a cohesive, multi-layered system where every piece works together. It’s about building genuine defense-in-depth and shifting your entire security posture from reactive firefighting to proactive threat hunting.
If you're still leading with just antivirus and a firewall, you're already years behind.
The Modern Essentials Beyond Antivirus
The game has changed. Attackers aren't just deploying basic malware anymore; they're using sophisticated techniques to slip past traditional defenses. That means your stack has to evolve, too.
Here are the non-negotiable components of a modern security stack:
- Endpoint Detection and Response (EDR): Think of this as antivirus on steroids. While old-school AV looks for known virus signatures, EDR watches for suspicious behavior. It can spot an attacker using legitimate tools for malicious purposes—something a legacy AV would completely miss.
- Security Information and Event Management (SIEM): A SIEM is your central command center. It pulls in logs from every device on the network—firewalls, servers, endpoints—and connects the dots to spot the faint signals of an attack that would otherwise be invisible.
- Proactive Vulnerability Management: You can't just wait for things to break. Regular vulnerability scanning is essential for finding and patching weaknesses before they can be exploited. This proactive stance is a core part of a mature cybersecurity for MSPs offering.
A strong security stack operates like a team. EDR is your guard on the ground, SIEM is the eye in the sky coordinating the response, and vulnerability management is the engineer reinforcing the walls before the battle even begins.
Integrating Tools for Real Defense-in-Depth
Having these tools is one thing; making them work together is what separates the pros from the amateurs. True defense-in-depth means that if one layer fails, another is right there to catch the threat.
For example, your EDR might detect a suspicious process trying to run on a server. That alert should automatically feed into your SIEM, which then correlates it with firewall logs showing weird outbound traffic from that same server.
This context instantly turns a low-level alert into a critical incident, letting your team respond immediately instead of chasing ghosts. This integration is what turns noisy data into actionable intelligence.
Augmenting Your Team with AI and Pentesting
Building and managing this kind of stack takes serious expertise, but you don't have to go it alone. AI pentesting and other AI-driven security tools can act as a force multiplier for your team, spotting anomalies and patterns a human analyst might miss. This lets you scale your security operations without massively increasing headcount.
The final piece of the puzzle is validation. How do you know your expensive, integrated stack actually works?
That’s where manual pentesting comes in. A pentesting engagement simulates a real-world attack, pushing past your defenses to find the exploitable gaps that automated scanners always miss. It’s the ultimate stress test for your stack and a critical service for any client who's serious about their security. To see how it all connects, check out our guide on threat and vulnerability management.
Turning Compliance Frameworks Into Recurring Revenue
Your clients hear "compliance" and immediately think of a massive, expensive headache. Frameworks like SOC 2, HIPAA, CMMC, and PCI DSS are seen as necessary evils then a bunch of checkboxes they have to tick to avoid fines or keep a big customer happy. This is where most MSPs stop, but it's exactly where you can start crushing it.
Stop viewing compliance as a cost center. For a smart MSP or vCISO, these frameworks are massive, untapped revenue opportunities just waiting to be claimed. Reframe the entire conversation. You're not just the IT guy; you're the strategic partner who can guide clients through the regulatory maze and turn their biggest annoyance into a competitive advantage.
This isn't about just checking boxes. It’s about building a security program that actually works and satisfies audit controls as a byproduct. The difference is huge. One approach is a flimsy house of cards; the other is a fortress that wins deals.
The data below shows the massive gap between what a breach costs and what most companies spend on security. It’s a gap you can fill.
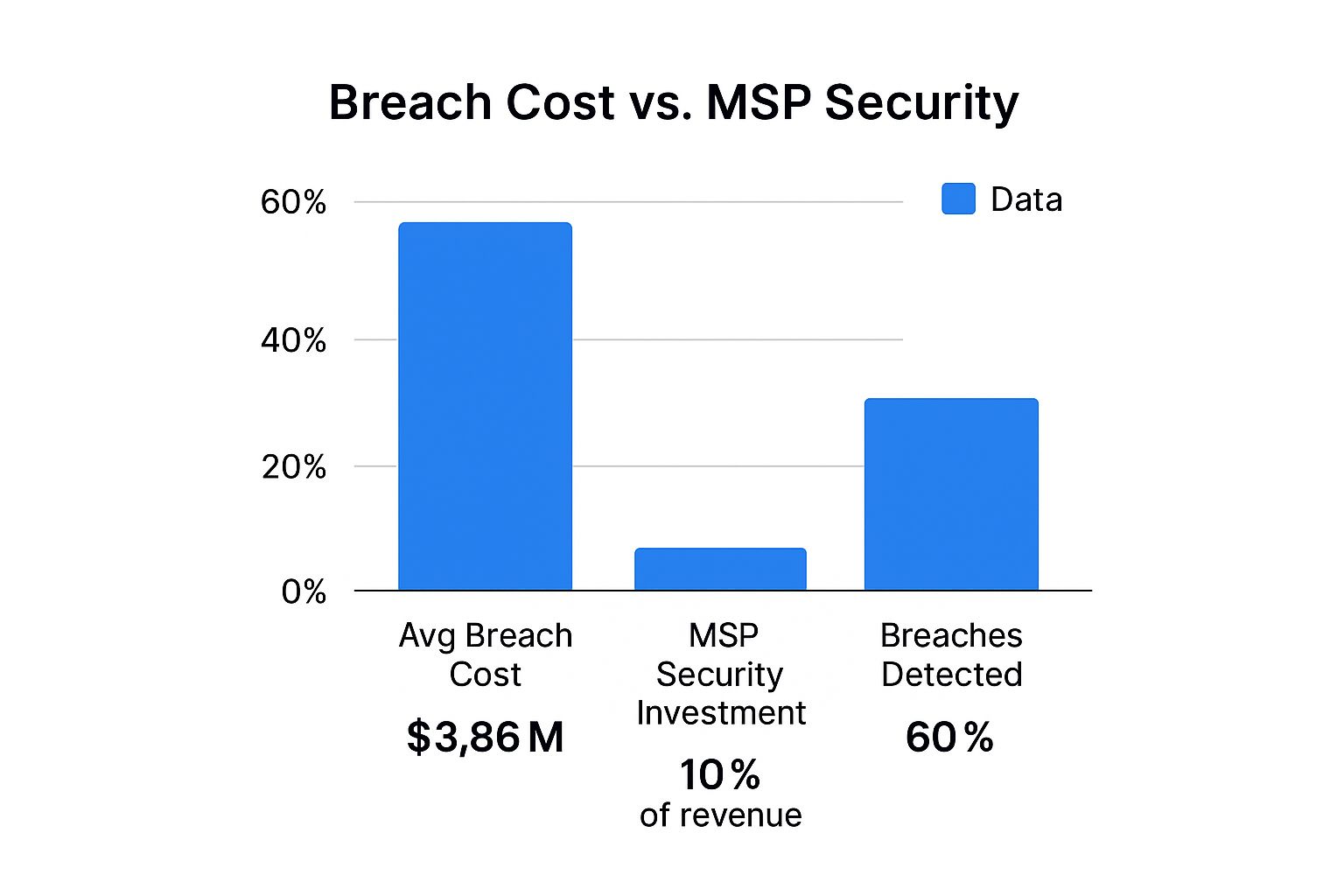
That disconnect is a critical opportunity. It's the "why" behind every security conversation you should be having, and it's where you provide immense value.
From Client Headache to Strategic Advantage
Your clients don't want to become compliance experts—they want to run their business. By stepping in as their guide, you transform your relationship from a simple service provider to an essential advisor. This deepens client loyalty and unlocks new streams of monthly recurring revenue (MRR).
Instead of just reacting to their compliance needs, you can proactively build a security roadmap that aligns with their business goals. This is how you move up the value chain and become indispensable.
Compliance isn't the goal; it's the outcome of a good security program. When you build security the right way, compliance often takes care of itself. This is the mindset shift that separates top-tier MSPs from the rest of the pack.
You’re no longer just selling them a firewall; you’re selling them peace of mind and the ability to land bigger contracts. That’s a conversation worth having.
Connecting Compliance to High-Value Services
Almost every major compliance framework requires some form of security testing and validation. This creates a natural, logical pathway for you to introduce high-value services that clients now understand they need.
We've broken down how some of the most common frameworks directly create a need for services like pentesting.
Compliance Frameworks and Required Security Services
Compliance FrameworkPrimary GoalCommonly Required Security ServicesSOC 2Prove that a service organization has effective controls over security, availability, processing integrity, confidentiality, and privacy of customer data.Vulnerability Assessments, Penetration Testing, Risk Assessments.HIPAAProtect the privacy and security of individuals' health information (ePHI).Security Risk Analysis (SRA), Penetration Testing, Vulnerability Scanning.PCI DSSSecure cardholder data to reduce credit card fraud.Regular Vulnerability Scanning (Req. 11.2), Annual Penetration Testing (Req. 11.3).CMMCSecure the defense industrial base (DIB) supply chain; required for DoD contractors.Security Assessments, Penetration Testing (at higher maturity levels), Continuous Monitoring.
This isn't a hard sell; it's a logical next step. You're simply connecting the dots for your clients.
Think about it:
- SOC 2: Auditors want to see that you're not just saying you have controls, but that you've actually tested them. This often includes vulnerability assessments and penetration testing.
- HIPAA: The Security Rule requires covered entities to conduct a risk analysis. A thorough pentesting engagement is one of the most effective ways to identify and assess risks to electronic protected health information (ePHI).
- PCI DSS: Requirement 11 is explicit—it mandates regular vulnerability scans and penetration tests. There’s no ambiguity here; if your client handles cardholder data, they need this service.
This is your golden ticket. You're not just pushing another service; you're providing a required solution to a pressing business problem. It’s the perfect opportunity to introduce manual pentesting as a non-negotiable part of their security strategy. We've actually written a full guide on how pentesting fits into various audits that breaks this down further.
As a reseller, offering white label pentesting means you can provide these essential services under your own brand. You control the client relationship and the pricing, all without the insane overhead of building an in-house testing team. You get to be the hero who solves their compliance nightmare, and we handle the heavy lifting in the background. It's a win-win that turns a client's regulatory burden into your most profitable service line.
Manual Pentesting vs. Automated Scans: What’s the Difference?

Automated vulnerability scans are table stakes. They’re a necessary baseline, but they will not stop a determined attacker. This is where you, as an MSP or vCISO, have a huge opportunity to educate your clients and seriously separate your services from the competition.
Too many clients see a clean vulnerability scan report and think their network is fortress-strong. It's a dangerous misconception. The global cybersecurity market hit roughly $245.62 billion in 2024 and it’s climbing fast. That growth isn’t just about new software; it's driven by attackers who know exactly how to exploit the gaps that automated tools can't see. You can dig into the numbers yourself in this cybersecurity market report.
Basic security isn't cutting it anymore. You need to explain the real difference between a simple scan and a manual pentest in a way that clicks for your clients.
The Thief Analogy: A Scan vs. A Heist
Here’s the simplest way to frame it.
An automated vulnerability scan is like a low-skilled thief walking down a street, rattling every single doorknob. They're just hoping to find one that's unlocked. It’s noisy, clumsy, and only finds the most obvious, easy-to-spot weaknesses. It’s a useful check, but it’s not a real security test.
A manual pentest, on the other hand, is like a professional thief casing the joint for a week.
This expert doesn't just rattle the doorknobs. They’re noticing the slightly loose window frame on the second floor. They see the overgrown bush that provides perfect cover next to the side door and the fact that the security camera has a massive blind spot. They chain together a series of small, seemingly unrelated oversights to get inside and walk out with the valuables.
An automated scanner finds known vulnerabilities. A human pentester finds unknown risks by thinking like an attacker. One is a checklist; the other is a creative, adaptive assault.
This is the core of your value proposition. You’re not just selling another scan; you’re offering to simulate a heist to see if their fortress can actually withstand a real, thinking attacker.
What Automated Tools Always Miss
Automated scanners are good at identifying known CVEs (Common Vulnerabilities and Exposures) and common misconfigurations. They’ll flag missing patches, default passwords, and open ports. But their limitations are massive, and this is where you can demonstrate your expertise.
Automated tools consistently fail to identify:
- Business Logic Flaws: These are vulnerabilities in the process of an application, not just its code. A scanner can't tell if a user can manipulate a shopping cart's pricing by applying multiple discounts in a specific order to get a product for free. A human sees that immediately.
- Chained Exploits: This is the hallmark of a skilled attacker. They might use a low-level information disclosure flaw to get an employee's name, then use that name in a social engineering attack to get credentials, then use those credentials to access a misconfigured cloud bucket. No scanner on earth can connect those dots.
- Privilege Escalation Paths: A scanner might find a "low-risk" flaw on one machine, but a manual pentester can show how that tiny flaw allows them to pivot to a more critical system and eventually gain domain admin rights.
- Contextual Weaknesses: An automated tool lacks business context. It can’t tell the difference between a public-facing web server and the critical internal database holding all the company's financial records. A human knows exactly what to target first.
These are the exact kinds of vulnerabilities that lead to the big, headline-grabbing breaches. Helping your clients understand this distinction is absolutely critical. For a deeper dive into what scanners do and don't cover, check out our article on security vulnerability scanning.
By positioning white label pentesting as a premium, necessary service, you move beyond being a basic IT provider and become a true security advisor. You're offering an invaluable service that addresses the sophisticated threats your clients are actually facing—threats a simple scan will never, ever find. It's an affordable way to provide immense value and prove their security investments are actually working.
Why a Channel-Only Partner Is Your Best Bet
If you’re an MSP or a vCISO, you’ve probably been burned before. You bring in a vendor for a specialized service, and the next thing you know, they’re going behind your back trying to sell directly to your client. It's the ultimate betrayal, and it happens way too often.
The traditional vendor-partner model is broken. A true channel-only partner operates on a simple, powerful principle: we never compete with you. Ever. Our success is tied directly to yours, which means our entire business is built around making you look good, protecting your client relationships, and helping you grow.
When you work with a channel-only partner, you're not just outsourcing a task. You're getting a dedicated team that acts as an extension of your own, with all the expertise and none of the conflict.
The Problem With the Old Pentesting Model
The traditional penetration testing industry is a mess for the channel. It’s built on problems that make it nearly impossible for an MSP to build a profitable, scalable service around it. You've likely run into these issues yourself.
The old model is plagued by:
- Inflated Prices: Most pentesting firms are geared toward massive enterprises, and their pricing shows it. This makes their services completely unaffordable for the small and mid-sized businesses that are your bread and butter.
- Insane Lead Times: It’s not uncommon to wait four to six weeks just to get a pentest on the calendar. In a world where new threats pop up daily, that’s an eternity. Your clients need answers now, not next month.
- Useless Reports: Many firms deliver a phonebook-sized PDF filled with technical jargon and zero actionable advice. It’s a data dump that impresses no one and helps no one, leaving you to translate the mess for your client.
This broken system forces MSPs into a terrible spot: recommend a service clients can't afford, wait forever for a test that might be irrelevant by the time it happens, or skip it altogether and leave everyone exposed.
A Better Model Built for Resellers
A channel-only approach flips that entire script. We built our model from the ground up to solve these exact problems for our partners. We're not just another vendor; we're your dedicated security arm, working in the background to make you the hero.
This is what a real partnership looks like. We focus exclusively on being the best at one thing: manual pentesting delivered through the channel. We don't have a direct sales team, we don't market to end-users, and we'll never even know your client's name unless you want us to.
This structure allows us to offer a radically different experience.
White Label Pentesting That Puts You in Control
Our white label pentesting service is the perfect solution for any reseller looking to expand their security offerings. It lets you sell high-end, expert-led security testing under your own brand, without the massive overhead of building an in-house team of certified pentesters.
Here’s how our model directly fixes the industry's biggest headaches:
The Old Way (Traditional Vendors)The Channel-Only SolutionOutrageously Expensive: Enterprise-level pricing locks out most SMBs.Affordable: Our model makes manual pentesting accessible and profitable for you to resell.Month-Long Waits: Slow scheduling kills momentum and leaves clients vulnerable.Fast Turnaround: We get tests scoped and started quickly, so you can deliver results while they still matter.Confusing Reports: Technical data dumps that create more work for you.Actionable Intelligence: We deliver clear, white-labeled reports that you can proudly put your logo on.Channel Conflict: They sell to you today and poach your client tomorrow.100% Channel-Only: We are your partner, not your competitor. Your client relationship is sacred.
This isn't just a better service; it's a better business model. By partnering with a channel-only provider, you can confidently sell critical security services like pentesting for SOC 2 or HIPAA compliance. You control the pricing, you own the client relationship, and you deliver a premium service that sets you apart. We just handle the heavy lifting behind the scenes.
How to Actually Sell Pentesting and Grow Your MSP
Adding pentesting to your service stack is the single best way to pump up your margins and make your clients stickier. But you can't just slap it on a quote and hope for the best. You have to sell it, and that means framing it as the ultimate health check for their business—one they can't afford to skip.
The cybersecurity market is exploding. It's on track to hit a massive $351.92 billion by 2030 because businesses are finally waking up to how much a breach actually costs. This isn't just an enterprise-level game anymore. The clients you already serve in healthcare, finance, and manufacturing are driving this demand. If you want to see the full breakdown, MarketsandMarkets has the data. This is your perfect opening to position pentesting as a non-negotiable investment, not a nice-to-have expense.
Choosing Your Pricing Model
You need a few ways to sell this. Not every client is ready to sign up for a recurring pentest, so having a few plays in your book lets you meet them where they are and build from there.
Here are the three models that work:
- The One-Shot Project: This is your foot in the door. Scope a one-time manual pentesting project, usually because they need it for something specific like a SOC 2 or HIPAA audit. It’s a low-friction way to show them the value without asking for a long-term commitment.
- The Recurring Check-Up: For your more mature clients, pitch this as an annual or semi-annual security physical. This gives you predictable revenue and makes sure they never drift out of compliance. It’s a win-win.
- The All-In-One Bundle: This is the endgame. Wrap white label pentesting into your premium managed security offering. Bundle it with your EDR, SIEM, and vulnerability management to create a high-margin security beast that nobody else can touch.
Turning the Report Into a Sales Roadmap
The real magic isn't the pentest itself it's what you do with the report afterward. A good pentest report doesn't just list vulnerabilities; it becomes your sales playbook from the findings. Stop seeing it as a deliverable and start seeing it as a strategy document.
A pentest report is the most powerful sales tool you'll ever have. It's an objective, third-party validation of every security recommendation you're about to make.
When you walk into a meeting with that report, you're not a vendor anymore. You're a trusted advisor with hard proof. The report gives you a natural, evidence-based reason to have the next conversation. Did the test uncover a weak firewall rule? That’s your cue to sell them a next-gen firewall. Did it find proof of successful phishing clicks? That's the perfect time to pitch security awareness training.
This is how you turn pentesting from a one-off project into the engine that drives your entire security practice. It fuels your sales pipeline with real, actionable needs and cements your role as the only security partner your client will ever need.
Frequently Asked Questions
You've got questions, we've got answers. Here are the no-nonsense responses to the things we hear most from MSPs, vCISOs, and their clients about cybersecurity, compliance, and pentesting.
How Often Should My Clients Get a Pentest?
Best practice is to get a pentest done at least once a year. But and this is a big but you absolutely need one after any major change to their network, applications, or infrastructure. Think about a big cloud migration, rolling out a new server, or a major software update.
Plus, compliance frameworks like PCI DSS, SOC2 and others have their own timelines that are often more frequent. We help you build a testing schedule that makes sense for each client, turning it from a one-off project into a predictable, profitable service you offer year after year.
What Is White Label Pentesting?
White label pentesting is your secret weapon. It’s how you sell our expert security testing services under your own brand, instantly making you look like a full-service security powerhouse.
You keep the client relationship, you set the price, and you deliver a comprehensive report with your logo front and center. We do all the heavy lifting in the background, making you the hero without the massive cost and headache of hiring an in-house team. It's the smartest way for any reseller to scale their security practice, period.
Is Manual Pentesting Actually Affordable for Small Businesses?
Yes. The old way of doing things was built for massive enterprise contracts with six-figure price tags. That world is dead. Our channel-only focus and efficient process make high-quality manual pentesting completely accessible and affordable for SMBs.
The cost of a data breach is always exponentially higher than the cost of a proactive test. When you frame it like that, pentesting becomes an easy-to-justify, high-ROI security investment for any client.
How Does Pentesting Help With SOC 2 or HIPAA?
It’s simple: many compliance frameworks, especially SOC 2 and HIPAA, either flat-out require or strongly recommend regular pentesting to prove your security controls actually work. It’s the difference between just saying you're secure and proving it.
A pentest report is the third-party validation that shows an auditor your client's security isn't just theory. It's real-world proof that their defenses hold up. This takes your clients from being "compliant on paper" to being truly secure in practice, which is what auditors are really looking for. It's a non-negotiable for any serious compliance effort.
Ready to stop competing with your vendors and start growing your security revenue? MSP Pentesting is your 100% channel-only partner for affordable, manual, and white-labeled pentesting. Contact us today to learn how we can help you win.


.avif)
.png)
.png)
.png)

