Buying external network penetration testing is completely broken for the MSP channel. You're either stuck paying a fortune to massive firms with month-long wait times or gambling with cheap vendors who just run a scanner and call it a day. Both options leave you holding the bag with a frustrated client. The industry has a problem with inflated prices, bad testing methodology, and long lead times. We're the solution for manual pentesting. And also the soltuion for AI and Automated pentesting.
Why Traditional Pentesting Fails MSPs
MSPs and vCISOs have been forced to choose between automated pentests with false positives and over priced manual pentests. The traditional pentesting market wasn't built for a reseller model; it was designed for direct-to-enterprise sales, leaving MSPs like you to deal with the fallout. This mismatch creates serious friction that hurts your business and your client relationships.
The whole process is usually a black box. You hand off the project, cross your fingers, and hope for the best, only to get a generic report you have even to photoshop your logo on. Right away, you look like a middleman instead of the expert security advisor your client trusts.
The Channel Conflict Problem
Even worse is that constant, nagging fear your pentesting vendor will poach your client. You bring them in for one project, and suddenly they're pitching their own managed services directly to your customer. This kind of channel conflict is a deal-breaker, turning a potential partnership into a direct threat to your revenue. You need a partner who plays for your team, not against it.
This broken model forces you to deal with:
- Inflated Prices: Enterprise-level pricing that makes zero sense for your clients or your margins.
- Long Lead Times: Waiting weeks or even months just to get started, which is useless when a client has a compliance deadline for SOC 2 or HIPAA.
- Generic Reporting: Getting reports that are impossible to white label, completely undermining your brand and authority.
- Client Poaching: The ever-present risk of a vendor stealing the relationship you worked so hard to build.
The core issue is simple: most pentesting companies see you as a lead source, not a partner. They don't get the MSP or vCISO business model and aren't invested in your success. We are a channel-only partner and we never compete with you.
Comparing Traditional vs Channel-Focused Pentesting
It's easy to see the difference when you put the two models side-by-side. The frustrations MSPs feel with traditional vendors stem from a fundamental misalignment of business goals. A true channel partner, on the other hand, is built from the ground up to support your business, not compete with it.
The contrast is stark. One model uses you, while the other empowers you.
This is exactly why a channel-only approach is the only one that actually works. You need affordable, manual pentesting from a team that is 100% committed to the reseller model. A true partner works in the background to make you look like the hero—they never, ever compete with you. It’s all about enabling you to deliver high-quality security services under your own brand, with complete confidence that your partner has your back.
What Is External Network Penetration Testing?

Alright, let's cut through the noise. What is an external network penetration test, really? Forget the confusing acronyms and overly technical fluff for a second.
Think of your client's network as a fortress. It has walls, gates, and watchtowers—all the defenses designed to keep bad actors out. An external network pentest is basically a sanctioned, real-world attack simulation targeting those public-facing walls. We're talking about anything and everything exposed to the wild west of the internet.
This isn't just about running an automated scanner that spits out a list of potential problems. That's a vulnerability scan, and frankly, it's lazy. A real pentest is a manual pentesting effort where human experts think, act, and attack just like a real hacker would. The goal is to not just find the holes, but to actually exploit them to see how far an attacker could get.
The Human Element in Pentesting
So, why is the manual, human-led approach so critical? Because automated tools are predictable. They can find the low-hanging fruit—an unpatched server or a misconfigured firewall rule—but they completely miss the bigger picture.
Hackers don't follow a script. They're creative, persistent, and they exploit business logic flaws that a scanner would never even recognize. That's why compliance frameworks like SOC 2 and HIPAA often require or strongly prefer manual pentesting. They know that a machine can't replicate the ingenuity of a human attacker trying to chain together multiple minor weaknesses into a major breach.
An automated scan asks, "Are any windows unlocked?" A manual pentest picks the lock, climbs through the window, and maps out exactly what an intruder could steal. That’s the difference your clients need to understand.
This distinction is crucial when you're positioning security services. As a trusted MSP or vCISO, you need to articulate why a cheap scan isn't enough to satisfy auditors or provide genuine security assurance. It’s the difference between checking a box and actually reducing risk.
Defining the Battlefield
A successful external network penetration testing engagement starts with a clearly defined scope. You can't protect what you don't know exists. This has become a core principle in modern cybersecurity, especially with today’s sprawling attack surfaces.
Best practices now demand that organizations meticulously plan their tests, defining scopes that include all recognized IPv4 and IPv6 addresses, subdomains, cloud services, and remote access portals. Think VPNs and SSH gateways. You can check out a detailed overview of the process to get a deeper understanding of modern pentesting checklists.
This initial reconnaissance phase typically includes mapping out:
- Web Servers: The front door to many applications and company data.
- Email Servers: A prime target for phishing and data exfiltration.
- VPN Endpoints: The gateway for remote employees and a common attack vector.
- Firewalls and Routers: The primary gatekeepers of the network perimeter.
By simulating a real attack against these assets, we provide you, the reseller, with a powerful deliverable. You get a white label pentesting report that doesn't just list vulnerabilities; it tells a story about your client's actual risk exposure. This allows you to have strategic conversations about security, moving beyond a simple grudge purchase and into the realm of a trusted security advisor. The ultimate goal is to demystify this critical service and equip you to sell its value with confidence.
Our Playbook for External Network Penetration Testing
Every solid pentest starts with a battle-tested playbook. You can't just fire up a scanner and call it a day—that's amateur hour. A real external network penetration testing engagement needs a methodical, multi-phase approach that mimics how actual attackers operate.
It’s part art, part science.
Our process is designed to be thorough and transparent for you and your clients. We've refined it over time to find the critical vulnerabilities that automated tools always miss, giving you a clear picture of the real-world risks your clients face. Think of it less like a checklist and more like a strategic campaign.
Phase 1: Reconnaissance and Footprinting
You can't attack what you can't see. The first step is always reconnaissance, where we map out the target's entire public-facing digital footprint. We’re looking for every server, every subdomain, and every IP address exposed to the internet.
This is the intelligence-gathering phase. Our team uses a mix of passive and active techniques to build a complete map of the attack surface, including:
- DNS Enumeration: Finding all associated domains and subdomains.
- WHOIS Lookups: Identifying registered IP blocks and contact info.
- Public Record Searches: Scouring the web for any leaked information or forgotten assets.
The goal here is to leave no stone unturned. An old, forgotten development server can often be the weakest link in the chain.
Phase 2: Scanning and Enumeration
Once we have our map, it's time to start probing the defenses. In the scanning and enumeration phase, we actively scan the targets to see what services are running and what ports are open. It’s like walking around a fortress and checking every door and window to see which ones are unlocked.
We identify active services like web servers, email servers, and VPN endpoints. More importantly, we figure out the exact software versions they're running. An outdated version of a common application is often a flashing neon sign for an attacker, pointing to a known, exploitable vulnerability.
We don't just find open doors; we figure out what kind of lock is on them and whether we already have the key. This detailed enumeration sets the stage for a much more effective attack.
This process blends automated efficiency with human oversight to build a full picture of potential entry points. The workflow below shows how we move from high-level scanning to a concrete findings report.
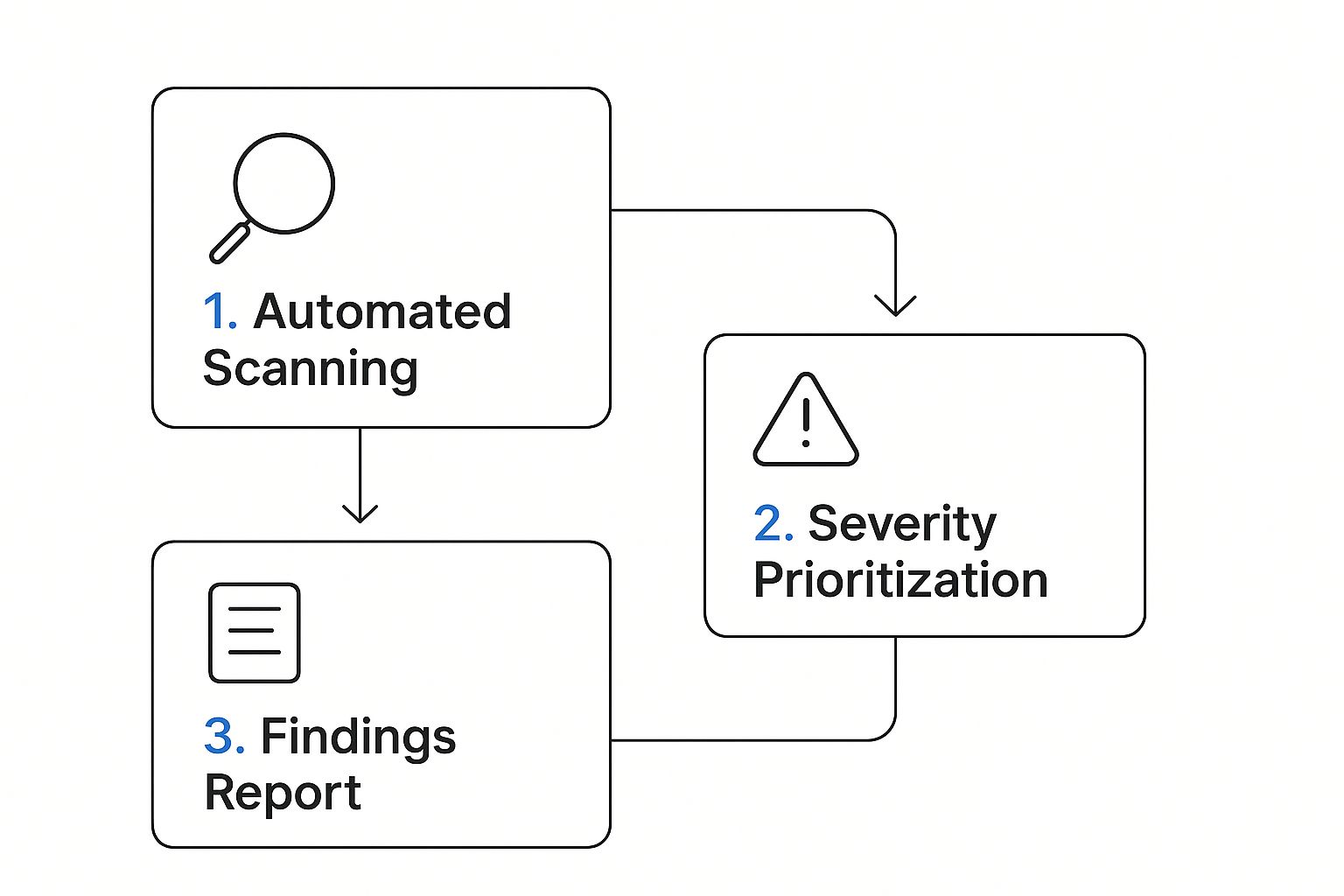
This structured flow ensures we focus our manual efforts where they matter most—on the vulnerabilities that pose a genuine threat.
Phase 3: Vulnerability Analysis
This is where our human experts really shine. With a list of potential weaknesses from the scanning phase, we move into vulnerability analysis. Our team manually investigates each potential flaw to determine if it's a false positive or a legitimate, exploitable vulnerability.
An automated scanner might flag a service as "outdated," but it takes a human pentester to understand the context. Can that vulnerability actually be triggered? Does it lead to a real business impact? This manual verification step is what separates a noisy, useless list of "potential" issues from a focused report on actual risks.
Phase 4: Exploitation and Post-Exploitation
Here's where the rubber meets the road. During the exploitation phase, our ethical hackers actively try to exploit the confirmed vulnerabilities. This is the core of manual pentesting. We don't just report the flaw; we demonstrate its impact by gaining unauthorized access, always within the agreed-upon rules of engagement.
This is what truly separates a real pentest from a simple vulnerability scan. By actually exploiting a weakness, we prove the risk and show your client exactly what an attacker could achieve.
- Business Logic Flaws: We uncover complex flaws in how an application works that scanners are completely blind to.
- Chained Exploits: We combine multiple low-risk vulnerabilities to create a high-impact breach.
We also use modern tools to make this process more effective. You can learn more about how we integrate techniques from AI pentesting to enhance our manual approach. After gaining a foothold, we may perform post-exploitation actions to determine the extent of a potential breach, mapping out lateral movement paths and identifying sensitive data at risk. This provides a complete picture of your client's security posture, giving you everything needed to drive meaningful improvements.
Selling Pentesting for Client Compliance Demands

For your clients in healthcare, finance, or SaaS, compliance isn't a suggestion—it's a core requirement for doing business. When an auditor comes knocking and asks for proof of security testing, a flimsy vulnerability scan report just isn't going to fly.
This is your moment to step in as their trusted MSP or vCISO and offer a real solution.
Positioning an external network penetration test is about changing the conversation. It’s not a grudge purchase or just another line item on an invoice. It's the key that helps them land bigger contracts, sail through critical audits, and prove to their own customers they mean business when it comes to security.
You’re not just selling a service. You’re selling them peace of mind and the ability to grow.
Connecting Pentesting to Compliance Frameworks
Auditors for frameworks like SOC 2, HIPAA, CMMC, and PCI DSS know exactly what they're looking for. They can spot the difference between a real pentest and a cheap scan a mile away.
Why? Because these frameworks are built to manage actual risk, not just to check a box. They require evidence of an independent, manual assessment that mimics what a real-world attacker would do.
A simple automated scan will miss complex business logic flaws or the kind of chained exploits that a human-led manual pentesting engagement is designed to uncover. This is your core talking point. When a client pushes back on the need for a manual test, you can tie it directly to their compliance mandate.
- SOC 2: The Security Trust Service Criterion (CC7.1) demands that organizations manage security vulnerabilities. A manual pentest is the gold standard for proving this control works.
- HIPAA: The Security Rule requires a thorough risk analysis. An external pentest is a crucial piece of that puzzle, identifying threats to electronic Protected Health Information (ePHI).
- PCI DSS: Requirement 11.3 couldn't be clearer—it explicitly mandates both internal and external penetration testing at least once a year and after any big changes.
For businesses in these industries, skipping a proper pentest is a non-starter. In fact, adoption of penetration testing in sectors like finance and healthcare has already shot past 70%. The stakes are just too high.
Don’t let your client get caught flat-footed in an audit. Frame the pentest as a non-negotiable part of their compliance roadmap. It’s the proof they need to show they’re not just talking about security—they’re actively testing it.
From Grudge Purchase to Strategic Advantage
The best way to sell pentesting is to stop talking about vulnerabilities and start talking about business outcomes. Your client doesn't just want a list of problems. They want to know how this service helps them make more money, lower their risk, and build trust.
When you offer white label pentesting, you control the narrative. You’re not just a reseller; you are the security expert guiding them. This solidifies your relationship and makes you an indispensable part of their team.
You can also use compliance as a powerful sales driver. For example, getting SOC 2 certified can be a game-changer for a SaaS company. Our guide on SOC 2 readiness for MSPs gives you a great playbook for these conversations. An affordable pentest is a tiny investment to land a six-figure enterprise deal that requires that certification.
Ultimately, you're helping them turn a security requirement into a competitive edge. By providing fast, reliable, and expertly handled external network penetration tests, you become the partner that helps them pass audits, close bigger deals, and secure their future.
The White Label Advantage for Your MSP
Let's cut to the chase. You shouldn't have to choose between trying to do a pentest in-house or sending your client to a third party who might just steal them. That's a broken model.
The real power move is offering expert external network penetration testing under your own brand. This is exactly where white label pentesting changes the game for MSPs and compliance-focused firms.
Think of us as your elite, behind-the-scenes security squad. We do all the heavy lifting—the reconnaissance, the manual exploits, the detailed analysis—while you stay as the single point of contact. You deliver a polished, professional report with your logo on it, cementing your status as their go-to security authority.
This isn’t about just slapping your logo on our work. It’s about taking complete ownership of the client relationship and, just as importantly, your revenue.
Full Control Over Your Client Relationships
The biggest fear for any MSP or vCISO is bringing in an outside vendor who ends up poaching the client. We get it. We built our entire business to prevent that from ever happening.
We are a 100% channel-only partner. That means we will never, ever compete with you. Period.
Our promise is simple:
- We never contact your clients directly. All communication goes through you.
- You own the entire relationship. You present the findings, you build the remediation plan, and you get all the credit.
- Your brand is the hero. Our reports are designed from the ground up to be fully white-labeled, making you look like the expert you are.
This model completely eliminates channel conflict and lets you get back to what you do best—serving your clients.
Set Your Own Profit Margins
Another major headache with traditional vendors? Their rigid, enterprise-level pricing. It crushes your margins and often prices out the very clients who need the service for compliance frameworks like SOC 2 or HIPAA.
White-labeling puts you back in the driver's seat. We offer affordable, reseller-friendly pricing, giving you the flexibility to bundle our services and set margins that actually make sense for your business.
You're no longer a middleman just passing along a cost. You become a value-added reseller providing a critical security service profitably. This transforms a one-off pentest project into a lucrative and repeatable revenue stream for your MSP.
You can find out more about how our manual white-labeled pentesting empowers you to grow your security practice.
Become the Go-To Security Authority
Ultimately, offering manual pentesting under your own brand elevates your entire business. You're no longer just the "IT guys"; you're strategic security advisors guiding clients through complex challenges like external network penetration testing.
This builds incredible trust and loyalty. When your clients need to satisfy an auditor or land a major new contract, they'll turn to you—not some random firm they found online.
By partnering with us, you instantly expand your service catalog with a high-demand offering, all without the massive overhead of building your own pentesting team. It's the smartest way to scale your security services and solidify your position in the market.
The Smart Choice for MSP Pentesting Partners

So, why should you partner with us for your clients' external network penetration testing? It really boils down to three things. We built our entire model for the channel, not to compete with it.
First off, speed. Traditional firms love to drag their feet, getting caught up in bureaucracy that leaves you waiting months for a report. We don’t do that. We deliver detailed, actionable reports in weeks, not months. This means you can hit those tight compliance deadlines for SOC 2 or HIPAA and keep your clients moving forward.
Affordable Expertise Built for the Channel
Next up is affordability. Our channel-only model means we’ve cut out the bloat and ridiculous overhead you see with legacy pentesting firms. You get top-tier manual pentesting at a price that actually protects your margins, allowing you as a reseller to build a security practice that’s actually profitable.
The global penetration testing market is absolutely booming, growing at a CAGR of over 15%, thanks to non-stop cyber threats and increasing regulatory pressure. We make it easy for you to grab a piece of that action. You can learn more about the growth of the pentesting market and see the opportunity for yourself.
But the most important part of our model is our promise to you. We are 100% channel-only. We exist to make our partners successful, and we will never, ever compete with you for your clients. Period.
This isn’t just another vendor relationship where you’re a number. It’s a real partnership with a company built from the ground up to help you win more deals, lock down your clients' networks, and become their trusted security expert. Our success is your success.
Ready to see how white label pentesting can beef up your security offerings? Let's talk about how we can help you and your clients win.
Frequently Asked Questions
You've got questions, we've got answers. Let's get straight to the point and tackle what MSPs and vCISOs are really asking about external network penetration testing.
What Is The Difference Between A Pentest And A Vulnerability Scan?
Think of it this way: a vulnerability scan is like an automated security guard walking around a building, jiggling every doorknob. It’s fast and finds the easy, unlocked doors.
A manual pentesting engagement is completely different. It’s a professional thief who finds a weak window latch (a vulnerability), picks the lock, climbs inside, and maps out exactly what they can steal. A real pentest doesn't just find the weakness; it exploits it to show you the actual business damage. Auditors for frameworks like SOC 2 and HIPAA know this difference, and they demand the real deal.
How Long Does An External Network Pentest Take?
This is a huge frustration in the industry. Big, old-school firms will quote you six to eight weeks, no problem. That timeline is a killer when your client has a pressing compliance deadline breathing down their neck.
We've built our process for speed without cutting any corners. For a typical external network test, you'll have a comprehensive, white label report in your hands in about two to three weeks. We move fast because we know the channel can't afford to wait.
Can I Put My Own Branding On The Final Report?
Absolutely. We wouldn't have it any other way. We're a 100% channel-only company, meaning our success is entirely tied to yours.
Every report we deliver is built to be fully white-labeled. You put your logo on it. You present it to the client. You get all the credit for being the security expert who brought them the solution. We stay completely in the background to make you look good.
This is the foundation of our reseller model. We will never go behind your back or try to poach your client relationship. That's a promise.
Why Is Manual Pentesting Better Than Just Using AI Tools?
Look, AI tools are great for speeding up the initial grunt work of discovery and scanning. We use them ourselves to make our process more efficient. But they are no substitute for the creative, and frankly, devious mind of a human attacker.
AI is good at finding known, textbook vulnerabilities. It completely misses the mark when it comes to:
- Spotting business logic flaws: Exploiting how an application is supposed to work, but in ways the developers never intended.
- Chaining low-risk vulnerabilities: An expert can link several "minor" issues together to create one massive, critical breach.
- Thinking on its feet: A seasoned pentester adapts and pivots their attack strategy in real-time—something an automated tool just can't do.
A legitimate external network penetration testing engagement requires a human expert to validate every finding and show the real-world impact. It's the only way to give your client a true picture of their security posture.
Ready to give your clients the fast, affordable, and expert pentesting they need, all under your own brand? Partner with MSP Pentesting and stop letting vendors dictate your margins and own your client relationships. Learn more about our channel-only partnership today.


.avif)
.png)
.png)
.png)

