When you hear people talk about vulnerability testing vs penetration testing, it really comes down to one simple idea. Think of vulnerability testing like an automated checklist that scans for known problems. On the other hand, penetration testing is a hands-on, manual attack simulation where a real person tries to break in.
Imagine a vulnerability scan gives you a list of all the unlocked doors and windows in a building. A penetration test is when a security expert actually tries to sneak through those openings, map out the inside, and see what they can steal. It shows you the real-world damage an attacker could cause.
Understanding Core Security Testing Differences
For an MSP or vCISO, explaining this difference to clients is crucial. Vulnerability testing offers breadth. It uses automated tools to quickly scan systems for thousands of known issues, which is great for regular security health checks.
But manual pentesting delivers depth. This is where our certified experts think like actual hackers, finding complex risks that automated tools always miss.
As a channel-only partner, we’re built to give you affordable, fast pentesting that you can resell under your own brand. You get the expertise of our OSCP, CEH, and CREST certified pentesters without any of the overhead. We never compete for your clients—we’re here to help you grow.
Key Differences Between Security Testing
For a quick reference, here’s a table that highlights the key distinctions between these two critical security practices.
AttributeVulnerability TestingPenetration TestingMethodAutomated scansManual, human-led attacksGoalIdentify known weaknessesExploit weaknesses to assess real-world business impactFocusBreadth (finds many potential issues)Depth (simulates a genuine breach scenario)FrequencyFrequent (e.g., monthly, quarterly)Less frequent (e.g., annually, after major changes)OutputA list of potential vulnerabilitiesDefinitive proof of exploitable risk and impact
Ultimately, vulnerability scanning tells you what might be wrong, while a penetration test shows you what an attacker can actually do with it. Both are important, but they solve very different problems.
What is Vulnerability Testing for MSPs
Think of vulnerability testing as your first line of defense in cybersecurity. It’s an automated scan that quickly checks your client's systems for known security issues, almost like running a digital checklist.
This process looks for common problems like unpatched software, weak passwords, or basic misconfigurations. It’s a fast, affordable way to get a broad overview of potential weaknesses across a network.
This kind of scan is essential for routine security hygiene and helps clients meet baseline requirements for compliance frameworks like SOC 2 and HIPAA. However, because it's automated, it often generates a lot of noise and false positives. It's great at creating a list of potential problems, but it can't tell you which ones are truly dangerous. For a deeper dive, our guide on security vulnerability scanning offers more detail.
What is Manual Penetration Testing
Automated tools are great, but they miss one critical element: human creativity. Manual penetration testing is where our certified pentesters (OSCP, CEH, CREST) step in. They don’t just follow a script; they think like real-world attackers.
Their goal isn't just to find vulnerabilities. It’s to actively exploit them and see just how much damage could be done.
This is where the real value is. A skilled pentester can chain together multiple low-risk issues to create a major breach—something an automated scanner would never catch. They also uncover complex business logic flaws unique to an application. This gives you concrete proof of risk, showing a client exactly how a small gap could lead to a data breach.
For MSPs and vCISOs, our affordable and fast manual pentesting delivers the deep insights needed to protect clients from modern cyber threats and validate their security controls. The demand for this kind of deep-dive analysis is only growing.
Our approach gives you the detailed, actionable information needed to prioritize what needs fixing and demonstrate true risk to your clients. To get a better feel for the process, check out our guide on how to perform penetration testing.
When to Use Each Security Service
Knowing which service to recommend transforms you from a vendor into a strategic advisor. Making the right call is all about focusing on your client’s immediate needs. The key is understanding the difference between routine maintenance and responding to a critical event.
This decision tree gives you a clear visual on when to deploy a vulnerability scan versus when a full penetration test is the answer.
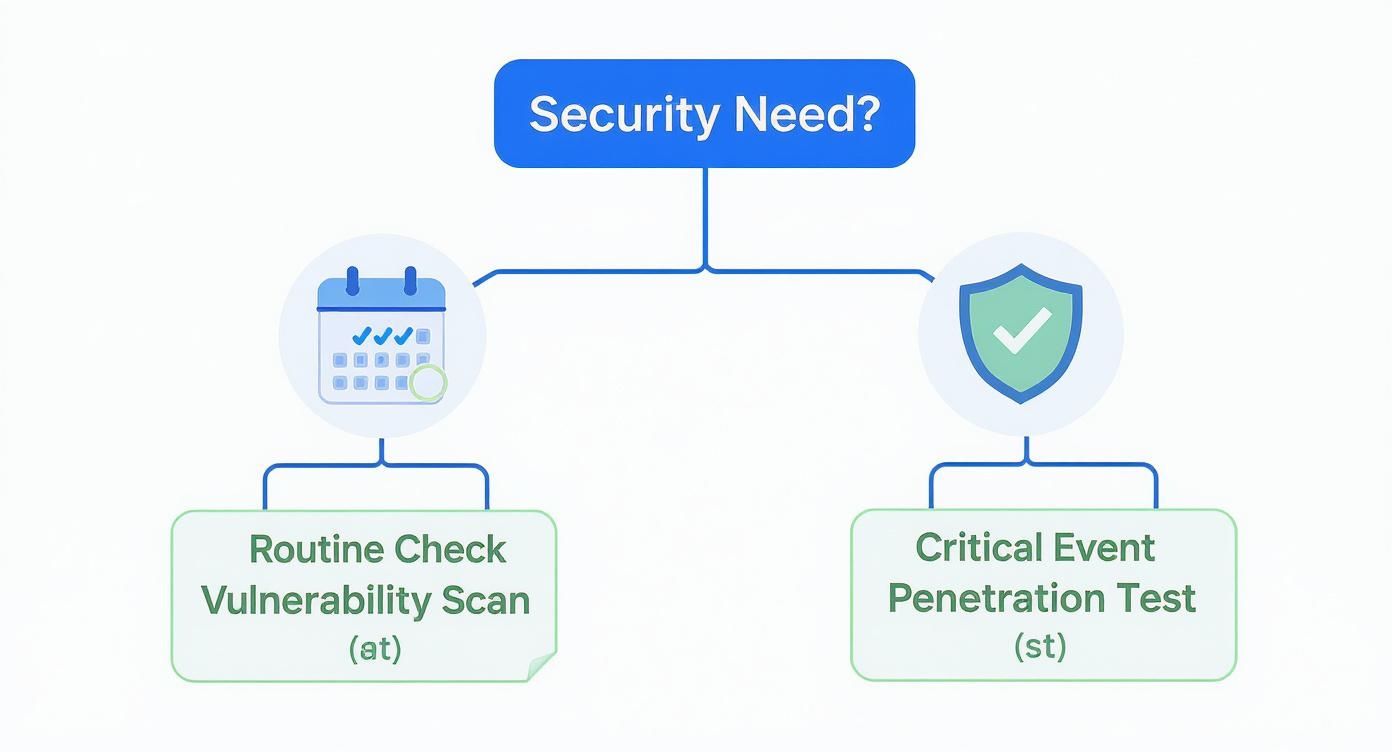
As you can see, the choice boils down to the situation’s urgency and how much assurance the client actually needs.
Choosing The Right Test for Compliance
For regular, ongoing security monitoring, a vulnerability scan is your go-to. Think of it as a monthly or quarterly check-up to maintain good security hygiene, especially after minor system updates. It's a quick, affordable way to spot common issues before they become bigger problems.
However, when things get serious, a manual penetration test is the only way forward. You’ll need this for annual compliance mandates like PCI DSS, SOC 2, or ISO 27001. It’s also a must-have before launching a major application or after significant changes to the network. Cybersecurity research backs this up, showing that the two services address totally different risk priorities. Scanning is for frequent identification, while pentesting delivers deep exploitation analysis. You can dig into how organizations pair these methods by checking out recent findings.
This approach empowers you, as an MSP or vCISO, to offer the right level of risk assessment exactly when your client needs it.
How Both Services Create Stronger Defense
The real question isn't vulnerability testing vs. penetration testing—it's how you use them together. Think of it as a one-two punch for your client's security. Vulnerability scanning is your early warning system, giving you broad, continuous monitoring for known issues.
Penetration testing is the deep, periodic gut-check that proves those defenses actually hold up against a thinking attacker. This layered strategy is how you build a complete security offering. You can provide ongoing vulnerability management and then seamlessly upsell our white label pentesting to deliver a solution that actually works.
Building A Comprehensive Security Offering
An integrated approach does more than just find holes; it builds a resilient security posture that clients will pay for. You start with the wide net of automated scanning and finish with the focused, manual expertise of a manual pentesting expert.
By combining both, you can cast a wide net to find potential risks with scanning, then use our targeted pentesting to confirm which ones are truly dangerous and exploitable.
This approach turns you from a service provider into a strategic security partner. You get to grow your revenue by offering a complete solution—from routine checks to in-depth, compliance-driven risk assessments—all while giving your clients real protection and peace of mind.
Why MSPs Choose White Label Pentesting
The traditional penetration testing industry has a problem. It's known for inflated prices, long wait times, and inconsistent results. We built our entire service to fix these issues for our channel partners. We deliver affordable, fast, and high-quality manual pentesting exclusively through resellers like you—MSPs, vCISOs, and GRC firms.

Our white label pentesting reports are designed so you can put your own logo on them and present our expert findings as your own. This reinforces your value and keeps you central to the client relationship. We are 100% channel-only, which means we will never compete for your customers.
Partnering with us helps you increase profitability, build client trust, and deliver top-tier security services without the overhead of building an in-house team. Our OSCP, CEH, and CREST certified pentesters become your team.
When you work with us, you can confidently meet your clients' needs for major compliance frameworks like SOC 2, HIPAA, and PCI DSS. You’re not just getting a vendor; you're gaining a dedicated resource committed to helping you grow.
Learn more about our approach to manual, white-labeled pentesting and see how we can help you expand your security offerings today.
Frequently Asked Pentesting Questions Answered
Here are a few straight answers to the questions we hear most from our MSP and vCISO partners. We want to make sure you have everything you need to make the right call for your clients.
How Often Should Penetration Testing Be Done
For compliance frameworks like SOC 2 or HIPAA, you're looking at an annual penetration testing engagement as the bare minimum. That’s the industry standard.
But here’s our take: you should absolutely get a new test done after any major changes to your applications or network. A simple update can accidentally open a door for an attacker, and you need to find it before they do.
Do You Offer Vulnerability Scanning Services
We don't offer vulnerability scanning as a standalone service because our focus is on manual pentesting—the critical next step after a scan. We strongly advise our partners to keep a routine scanning program in place.
Our job is to come in after your scanner flags potential issues. We validate those automated findings, confirm which risks are actually exploitable, and dig for the deeper threats that scanners are completely blind to.
Automated tools are great for finding known, low-hanging fruit, but they can't think like a person. Our OSCP, CEH, and CREST certified experts simulate how real attackers operate, finding complex business logic flaws and chaining vulnerabilities together in ways a scanner could never imagine. This gives you a true risk assessment, not just a noisy list of maybes.
How Does White Label Pentesting Work
We designed our process to be as simple as possible for you. You’re the reseller, so you’re in control.
Here’s the breakdown:
- You sell the pentest to your client under your own brand.
- Our team performs a thorough manual penetration test behind the scenes.
- We hand you a detailed report, fully branded with your logo.
- You deliver the final report to your client as their trusted security expert.
It's a straightforward way for any MSP or GRC firm to add a high-value, affordable security service to their lineup without the massive overhead of building an in-house team.
Ready to give your clients the affordable, expert-led penetration testing they need? As a channel-only partner, we are here to help you grow your security practice.
Contact us today to learn more about our white label pentesting program.


.avif)
.png)