Thinking about penetration testing? Let's imagine you're explaining it to someone new. This guide is for MSPs, vCISOs, and GRC companies who need top-notch security tests without the shocking prices and long waits common in the industry.
We'll walk through a clear, simple process for manual pentesting. This is the kind of testing that finds the real-world vulnerabilities attackers love to exploit.
Understanding the Penetration Testing Process Today
This process isn't just about finding security holes. It's about helping your clients meet tough compliance standards like SOC 2, HIPAA, and PCI DSS. This guide will help you offer a service that makes you a key partner. We provide the expert testing with certified pentesters behind the scenes, so you can focus on building trust with your clients.
Penetration testing, or pentesting, is like a fire drill for your digital security. It simulates a real cyberattack to find weak spots before criminals do. It's so important that the global market, valued at around USD 2.45 billion, is projected to hit USD 6.25 billion by 2033. This service is no longer optional; it's essential.
For any reseller, understanding the process is key to selling it. This infographic breaks down the basic steps of a typical pentest in a straightforward way.
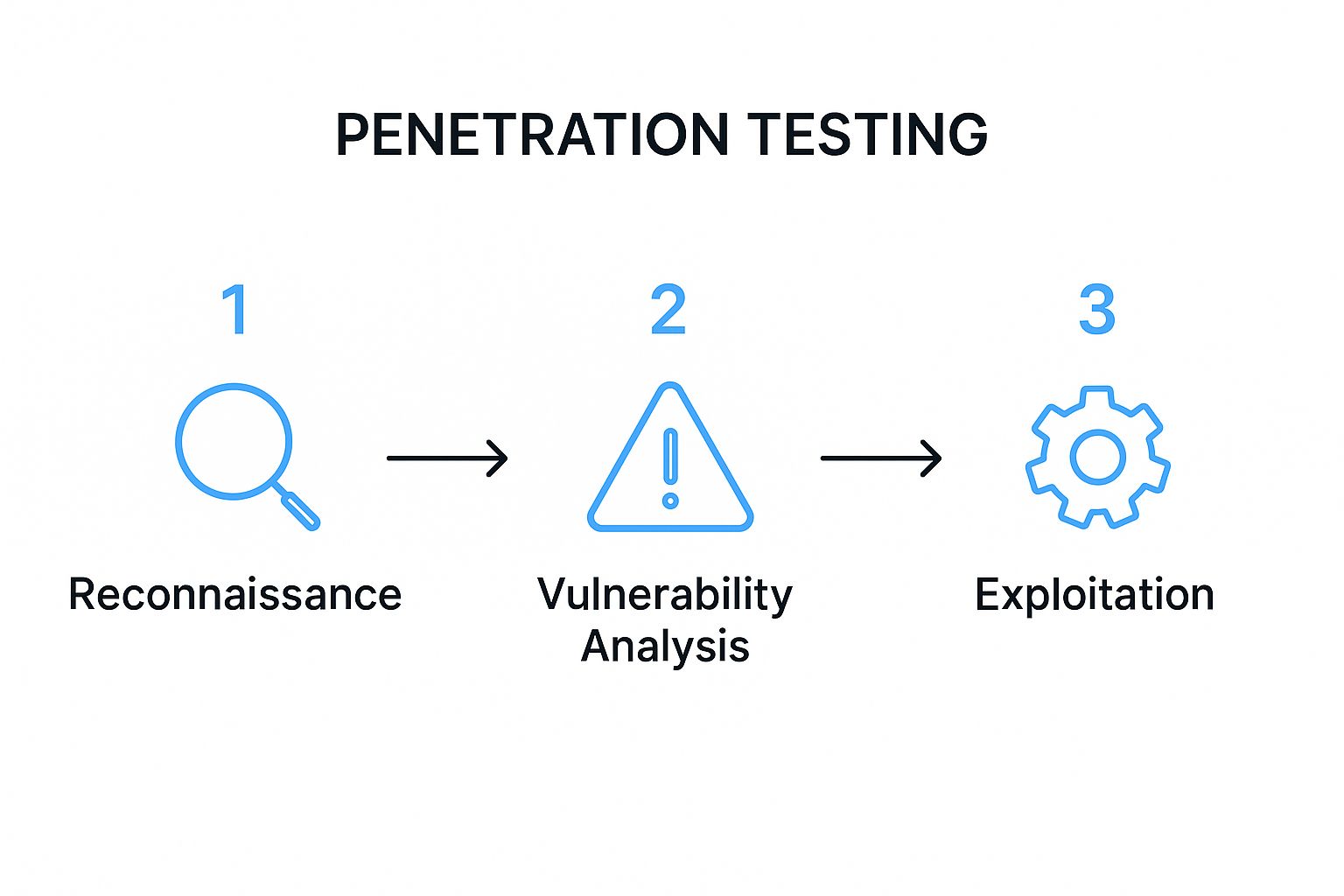
As you can see, a real test moves from gathering information to actively trying to exploit vulnerabilities. This hands-on, manual pentesting process is what makes a real pentest different from a cheap, automated scan that just gives you a list of possible problems. A thorough risk assessment requires a human touch.
To make it even clearer, here's how these phases work in practice. This table shows what happens at each stage of a professional pentest.
Planning Your Successful Penetration Test Strategy
A good penetration testing project starts with a conversation, not a scan. This first planning phase is where you and your client agree on goals, rules, and what's included in the test. For an MSP or vCISO, this is your chance to show your expertise by asking the right questions.
Are they worried about their external network, a specific web app, or internal systems? What are their biggest security fears? Are they preparing for a SOC 2 audit or getting ready for HIPAA compliance? Getting these answers right from the start sets clear expectations and prevents problems later.
This teamwork does more than just define the test; it builds trust. It shows you're a strategic partner, not just another vendor.
The goal is to set up clear communication and get all permissions before any testing begins. A well-defined scope means our certified pentesters—who hold certifications like OSCP, CEH, and CREST—can focus their efforts where it matters most. This is how we deliver affordable, high-impact results quickly.
Properly managing this first step is a key part of any good vulnerability management program. For a deeper look, check out our guide on threat and vulnerability management.
How We Execute Your Manual Pentest

This is where the action happens, and where our expert-led approach makes a huge difference. Forget about noisy, automated scanners that produce generic reports. Our method is all about manual pentesting, where our certified experts think like real attackers to find what automated tools always miss.
Our OSCP and CREST certified pentesters start by gathering information to map out your client's digital footprint. Then, we look for weaknesses in their systems and applications.
The most important part is exploitation. We safely use these vulnerabilities to show real business risk. This manual process helps us find complex flaws that automated scanners are blind to.
For you, as an MSP or vCISO, this careful approach sets you apart. It changes your service from a simple compliance checkbox to a true risk assessment that helps your clients. Our internal processes follow the industry's penetration testing best practices to ensure you get quality results every time.
While our focus is on manual work, we also use technology to be efficient. We know AI is changing the game. Nearly 80% of organizations use automated tools for compliance, and AI can speed up testing by up to 30%. You can read more about the evolving penetration testing market on straitsresearch.com. We blend smart automation for speed with deep manual expertise for accuracy.
Delivering Actionable Pentest Reports for MSPs
Even the best penetration testing is useless if the final report is just a confusing document. A great report translates technical findings into clear business risks that an executive can understand. This is the final, and most important, part of any real risk assessment.
A valuable report prioritizes findings based on their real-world impact and the chance of being exploited. It needs to provide simple, step-by-step instructions on how to fix the problems. For any MSP or vCISO, this is where you prove your value, turning a one-time test into a long-term security partnership.
The goal is to provide a clear roadmap for improvement. You explain the "so what" behind each vulnerability, helping clients understand the risks to their business, whether for SOC 2 or HIPAA compliance.
As our channel partner, you get a full white label pentesting report that you can put your brand on. This lets you confidently walk your client through the results, positioning yourself as the expert. To help you with this, we've created a guide on what makes a solid report. You can find more details in our post on creating a penetration testing report template.
Meeting Compliance Needs with Penetration Testing
For many of your clients, penetration testing is not just a good idea—it's required. If they need to meet major compliance frameworks like SOC 2, HIPAA, PCI DSS, or ISO 27001, a proper pentest is one of the most direct ways to succeed. It makes a stressful audit much simpler.

Auditors want proof, not promises. Nothing shows you're serious about security like a detailed, manual pentesting report from certified professionals. Take PCI DSS, for example. It requires regular network and application testing to protect cardholder data. The same is true for a SOC 2 audit, which often depends on showing you're actively finding and fixing security gaps.
A detailed pentest report gives concrete evidence that a client is meeting their compliance duties. Here's a quick look at how pentesting helps with some of the biggest frameworks.
Pentesting's Role in Major Compliance Frameworks
Compliance StandardRelevant RequirementHow Penetration Testing HelpsPCI DSSRequirement 11.3: "Implement a methodology for penetration testing."Directly meets this requirement by simulating real-world attacks to find vulnerabilities.SOC 2CC7.1: "To meet its objectives, the entity uses detection and monitoring procedures..."Confirms that security controls are effective and finds weaknesses before an attacker can.HIPAA§164.308(a)(1)(ii)(A): "Conduct an accurate and thorough assessment of the potential risks..."Finds vulnerabilities in systems that handle electronic Protected Health Information (ePHI).ISO 27001A.12.6.1: "Information about technical vulnerabilities... shall be obtained in a timely fashion."Provides a deep analysis of vulnerabilities that automated scanners often miss.
These frameworks all require a proactive approach to security, and pentesting is the best way to deliver that.
Different industries test at different rates. Financial institutions are ahead, with about 40% now doing quarterly or continuous pentesting. In contrast, only 13% of smaller firms test that often. You can discover more insights about pentesting frequency on cybersecurityventures.com to learn more.
As their MSP or vCISO, you guide them. By partnering with us, you can offer an affordable white label pentesting service from pros with OSCP, CEH, and CREST certifications. This helps your clients meet their obligations and strengthens your role in their GRC strategy.
Partnering with Us for White Label Pentesting
You know how to do penetration testing, but the real question is how to offer it without breaking the bank. The security industry has a problem: inflated prices, long lead times, and vendors who compete with the MSPs and vCISOs who bring them business. We saw this broken model and created a better solution.
We are a channel-only partner. This is our entire business model. We never sell directly to clients and never compete with our MSP and vCISO partners. Our job is to be your expert team, making it easy for you to offer affordable, fast, and high-quality white label pentesting.
This means you can add a high-demand security service and increase your revenue without the huge cost of hiring an in-house pentesting team.
Our process is simple. Our team of certified pros—with credentials like OSCP, CEH, and CREST—performs a thorough manual pentest.
When we're done, you get a detailed report with your logo on it. It’s ready to give to your client, helping them meet compliance needs for frameworks like SOC 2 or HIPAA and making you the hero.
Ready to start selling top-tier manual penetration testing and grow your business?
Contact us today to learn more about our reseller program.
Answering Your Top Penetration Testing Questions

We often get these questions from MSPs looking to add pentesting to their services. Here are some quick answers.
How Long Does a Typical Penetration Test Take?
It really depends on the scope. A simple external network test might take one to two weeks. A more complex web application assessment will take longer.
Our focus is always on speed and delivering results quickly. We provide your white label pentesting report just a few days after finishing the active testing.
What Is a Vulnerability Scan vs. a Pentest?
This is a key difference. A vulnerability scan is an automated tool that finds potential problems. It can be noisy and often has false positives.
A manual pentesting engagement is where one of our certified ethical hackers tries to exploit those potential problems. We find the real-world risks that automated scanners always miss.
How Often Should My Clients Get a Pentest?
Best practice is to have a pentest at least once a year. You should also get one after any major changes to their network or applications.
Remember, some compliance frameworks like PCI DSS often require more frequent testing.
Ready to offer fast, affordable, and expert-led manual pentesting to your clients? Partner with us and let our certified team be your security experts. We make it easy for you to win deals and protect your clients.


.avif)
.png)
.png)
.png)

