Let's be real: most penetration testing reports are unsecure. Seriously. They’re either unreadable walls of tech jargon clients toss aside, or flimsy checklists that barely justify the fee you charged. A penetration testing report template isn't just a document; it's what separates a one-off scan from a high-value partnership. And for an MSP or vCISO, it's your #1 sales tool.
The industry is full of overpriced, slow, and frankly, lazy pentesting. Inflated prices, bad methodologies, and insane lead times are the norm. We're here to fix that with affordable, fast, manual pentesting that you can deliver under your own brand.
Why Your Current Pentesting Report Template Probably Sucks
Think about it—the final report is the only tangible thing your client gets from a pentest. If that report is weak, they assume your entire service is weak, no matter how sharp your manual pentesting skills are. The industry is flooded with reports that completely miss the point, and it’s costing MSPs and vCISOs credibility and clients.
Too many pentesters just dump raw vulnerability data and call it a day. That's a massive missed opportunity. Your client, especially anyone in the C-suite, doesn’t give a damn about a CVE score. They care about what that vulnerability actually means for their business. This is where you, the reseller, come in.

The Credibility Killers in Bad Reports
The difference between an MSP who gets repeat business and one who’s constantly chasing leads often comes down to the quality of their deliverable. A weak report signals a weak service. Here's where most go wrong:
- No Business Context: A finding like "Cross-Site Scripting (XSS) on login page" is useless to a CEO. A much better report frames it like this: "We found a flaw that lets attackers steal employee credentials, which could lead to a full network compromise." Now that gets attention.
- Generic, Copied-and-Pasted Fixes: Recommending "patch your systems" is just lazy. It screams that you didn't take the time to understand their environment. Actionable advice has to be specific and tailored.
- Focusing on Volume Over Impact: A 100-page report filled with low-risk "informational" findings is just noise. It buries the critical issues that actually need to be fixed and makes your client's security team hate you for wasting their time.
The goal of a great penetration testing report isn't to show how many things you found; it's to provide a clear, prioritized roadmap that crushes real-world business risk. Anything less is a disservice.
A strategic report is your best sales tool. It proves your value, justifies your price, and cements you as the expert who connects tech gaps to business outcomes. This is non-negotiable for clients needing to satisfy SOC 2 or HIPAA compliance. They don't just need to check a box; they need a partner who gets risk.
As your channel-only partner, our entire white label pentesting model is built on giving you the ammo to be that indispensable advisor. For a deeper look into how the industry is shifting, our guide on what changed in pentesting in 2025 offers more context.
The Anatomy Of A High-Impact Pentest Report
Let's cut to the chase. A penetration testing report is more than a document; it’s a strategic weapon. Done right, it closes deals, drives action, and positions you as the indispensable security partner your clients need. Done wrong, it’s a glorified doorstop. We’re here to make sure you’re crafting the first kind.
The point of the report is to tell the story of a simulated attack. It needs a beginning (scope), a middle (findings), and an end (remediation roadmap). Every section has a job, and they all have to work together to deliver a clear, compelling message. Forget just listing vulnerabilities; we’re building a narrative that connects every technical finding back to real-world business impact.

This isn’t about filling in blanks on a generic template. It's about understanding the why behind each component so you can deliver a report that resonates with everyone, from the C-suite to the sysadmin in the trenches.
To do that, you need a structure that speaks to both technical and non-technical audiences. A winning report is designed to satisfy the execs who approve the budget and the engineers who have to implement the fixes.
Key Sections for a Winning Pentesting Report Template
This table breaks down the essential components your penetration testing report template must include to be effective for both technical and executive audiences.
Report SectionPrimary AudienceCore Purpose & Key InformationExecutive SummaryC-Suite, Decision-MakersPlain-English overview of the overall risk posture and potential business impact. This is your 30-second elevator pitch.Methodology & ScopeTechnical Team, ManagementClearly defines what was tested, how it was tested (e.g., manual pentesting, AI, social engineering), and what was out of scope. Manages expectations and ensures transparency.Findings & VulnerabilitiesTechnical TeamThe core of the report. Detailed, evidence-backed breakdown of every flaw, with proof and steps to reproduce.Risk Analysis & Business ImpactC-Suite, ManagementTranslates technical jargon into business terms (dollars and downtime). Connects vulnerabilities to tangible business risks.Remediation RecommendationsTechnical Team, ManagementAn actionable, prioritized roadmap. Spells out exactly what to fix, in what order, and how to do it.
Getting this structure right is non-negotiable. It ensures clarity and drives the right conversations. The global penetration testing market is booming, expected to hit USD 6.25 billion by 2033, because regulations like HIPAA and SOC 2 demand this level of rigor. A solid report isn't just good practice; it's a critical tool for meeting compliance and proving your value.
Diving Deeper Into Key Report Sections
Let's break down the most critical parts of the report. Get these right, and you're golden.
Vulnerability Details That Actually Help
For each vulnerability, you need more than a CVE number. Your client's tech team needs a playbook.
Every finding should include:
- A Clear Title and Risk Score: Something like "Critical Risk: Remote Code Execution on Web Server" immediately sets the priority. No ambiguity.
- Detailed Description: Explain what the vulnerability is and how an attacker could exploit it in their specific environment. Context is king.
- Proof of Concept (PoC): Show your work. Include sanitized screenshots, code snippets, or video recordings that demonstrate the exploit. This is irrefutable proof.
- Steps to Reproduce: Give their team a clear, step-by-step guide so they can validate the finding and test the eventual fix.
A finding without a PoC is just an opinion. A finding with a PoC is a fact. Your job is to deliver facts.
Risk Analysis That Resonates
This is where you, the MSP or vCISO, truly shine. You take a tech issue and put it in context. Don’t just state the CVSS score. Explain what that score means for them.
A "medium" vulnerability on a public e-commerce server is far more critical than a "high" vulnerability on an isolated dev box. You need to factor in asset criticality, data sensitivity, and potential operational downtime. A risk matrix that visually plots likelihood vs. impact is a powerful tool here.
Remediation That Drives Action
Generic advice like "update software" is useless. Your recommendations have to be specific and actionable.
- Immediate Fixes: What are the quick wins? Focus on the most critical vulnerabilities that can be patched easily to reduce risk now.
- Strategic Improvements: What are the underlying issues? Maybe they need better network segmentation or a secure coding lifecycle. This is where you recommend long-term fixes.
- Resource Links: Provide direct links to vendor patches, security advisories, or technical guides. Make it as easy as possible for their team to get started.
As a reseller, this section is your goldmine. It's where you identify opportunities for new projects and managed services. Our white label pentesting service is designed to tee you up for exactly this. We handle the deep-dive testing; you own the high-value remediation relationship.
Check out our guide on how our white labeling for MSPs works to see how we empower our partners.
How to Craft an Executive Summary That Gets Read
Let's be blunt: the Executive Summary is everything. It's the one part of the report that gets read by the people who sign checks. If you screw this up, the rest of your hard work is irrelevant.
Too many security reports dive straight into the weeds, throwing around CVE numbers and tech jargon that instantly makes an executive's eyes glaze over. This is your one chance to show the real value of your pentesting service. Make it count.
This summary isn’t for the IT team; it’s for the C-suite. They don’t care how you found the vulnerability. They care what it means for the business. Your job is to translate complex findings into clear, undeniable business risk. If you can't, you've already failed, no matter how good your manual pentesting was.
From Tech-Speak To Business Impact
A weak executive summary is just a lazy rehash of technical details. A powerful one tells a compelling story about risk. It directly connects a technical flaw to real-world consequences like financial loss, brand damage, and operational chaos.
Let’s look at a quick before-and-after to see the difference.
Before (The Weak, Tech-Focused Approach):
"During the assessment, we identified a critical SQL Injection vulnerability (CVE-2023-XXXXX) in the main web application's customer login portal, which received a CVSS score of 9.8. We recommend the development team apply the latest patches to mitigate this finding."
This is technically correct but useless for an executive. It’s dense, confusing, and creates zero urgency.
After (The Strong, Business-Driven Approach):
"Our team discovered a critical flaw in your customer login portal that allows an attacker to steal your entire customer database with minimal effort. This is a major data breach waiting to happen, exposing you to significant regulatory fines under HIPAA and causing irreparable damage to your brand. We’ve flagged this as your number one priority."
See what happened there? The second version is direct and hits where it hurts. It talks about things leadership actually cares about: customer data, money, and reputation.
Essentials For A Killer Executive Summary
Your summary needs to be short, sharp, and to the point. Ditch anything that isn't essential for a decision-maker.
Here are the non-negotiable pieces you must include:
- Overall Risk Score: Give them a high-level score right at the top. Use a simple scale like Critical, High, Medium, Low, or a color-coded chart. It provides an instant gut check on their security posture.
- Summary of Critical Findings: Don't list everything. Pick the top two or three most dangerous vulnerabilities and describe them in plain English.
- Potential Business Impact: This is where you make your case. Spell out the real-world consequences. Are they facing SOC 2 compliance failures? Could ransomware shut down their operation? If you can, quantify the risk.
Think of the executive summary as your 30-second elevator pitch. It has to give a non-technical executive enough ammo to walk into a board meeting and get immediate approval for remediation.
You are the translator between the server room and the boardroom. For any vCISO or MSP, mastering this skill is what separates a technical audit from true strategic advisory. A powerful summary proves you understand their business, not just their firewall rules.
This is the entire philosophy behind our white label pentesting service. We handle the deep technical work so you, the reseller, can deliver the strategic business insights that make you an indispensable partner.
Translating Technical Findings Into Business Impact
This is where you make your money. Seriously.
Finding an SQL injection is the easy part; the real value comes from explaining why it matters. A technical finding means nothing to a CEO. But framing it as "a flaw that could let an attacker steal your entire customer database and trigger massive HIPAA fines"—that gets immediate attention and budget approval.
As an MSP or vCISO, your ability to contextualize risk is what separates you from every other scanner jockey out there. It’s the art of mapping a technical vulnerability to tangible, cold, hard business risk. This elevates you from a tech provider to a strategic risk advisor, a critical differentiator for your business.
From CVSS Scores To Business Consequences
The Common Vulnerability Scoring System (CVSS) is a great starting point, but it's just that—a start. A CVSS score doesn't understand your client's business. It has no idea if a vulnerable server hosts cat pictures or the entire company's IP. That's your job.
To truly translate risk, you need to combine technical severity with business context. This means looking beyond the score and factoring in things like:
- Asset Criticality: How important is the affected system? A flaw on the main e-commerce server is infinitely more critical than one on a forgotten dev box.
- Data Sensitivity: What kind of data is at risk? Is it public marketing material or protected health information (PHI) that falls under strict compliance rules?
- Operational Disruption: What would happen if this system went down? Could it halt production, stop sales, or grind the entire business to a halt?
This process shows you're not just running a tool; you're thinking like an attacker who wants to cause maximum damage.
A Practical Risk Rating Methodology
A structured approach ensures you consistently and accurately assess risk for every finding. This infographic outlines a simple but powerful methodology for rating vulnerabilities based on their real-world impact.
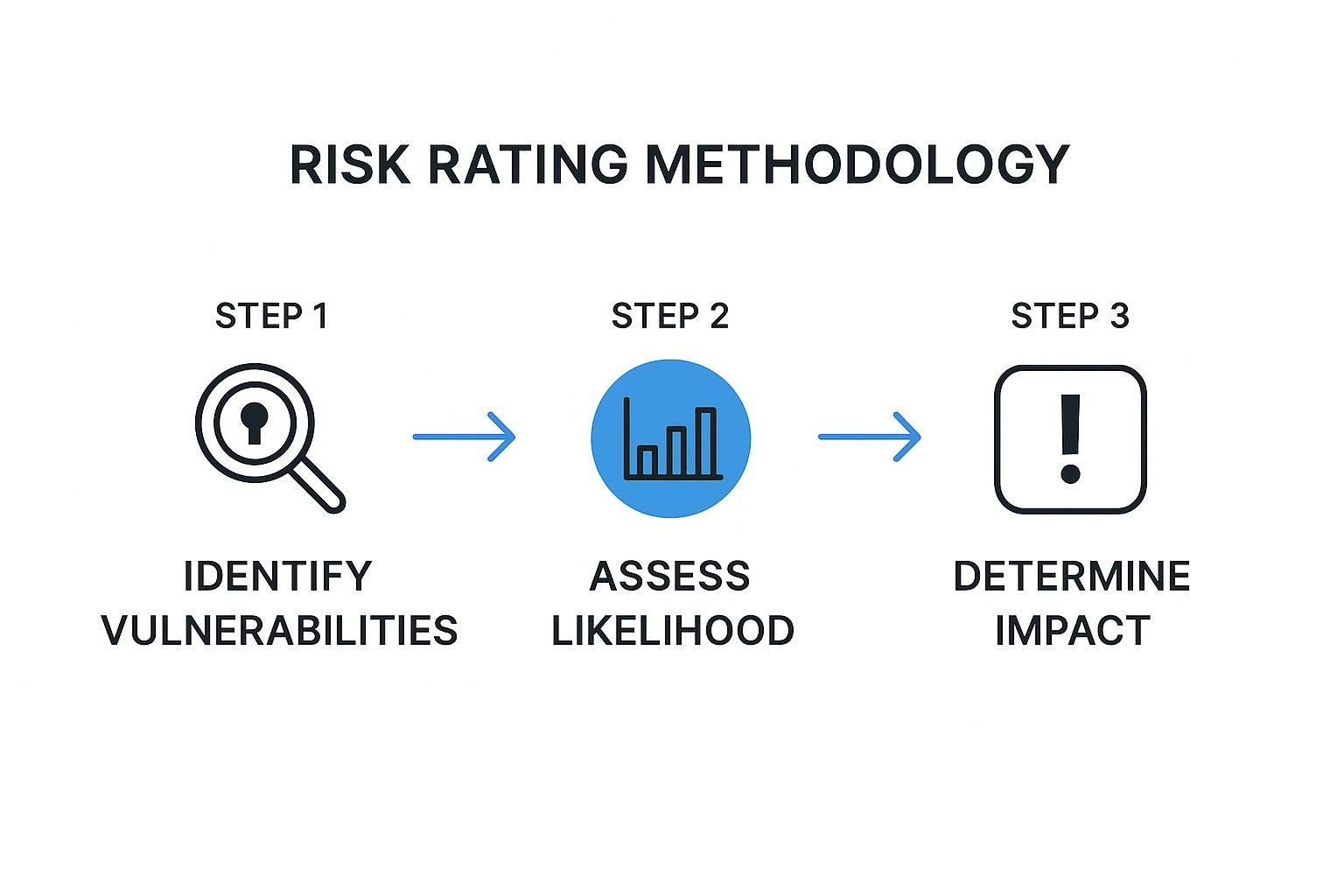
This visual flow clarifies how identifying a vulnerability is just the first step. Assessing its likelihood and potential impact is what ultimately determines its priority. Following this process helps you create a clear, defensible risk assessment that clients can easily understand and act upon.
This is especially critical when you consider how much is at stake. As of early 2025, global data shows that about 51% of organizations outsource their testing to specialized third-party providers. In the U.S. alone, enterprises spend an average of $187,000 annually on pentesting. That spending is an investment, and your report is the ROI. The ability to translate findings into actionable business insights is what justifies that budget and cements your value. You can read more about these emerging penetration testing statistics and see how top firms are adapting.
Using A Risk Matrix To Communicate Priorities
Once you’ve assessed the risk, you need to communicate it clearly. A risk matrix is one of the most effective tools in your penetration testing report template for this. It visually plots each vulnerability based on its likelihood and business impact, instantly showing clients where to focus their limited resources.
Stop giving clients a flat list of problems. Give them a prioritized, risk-based action plan. A risk matrix turns a confusing data dump into a strategic roadmap.
Imagine presenting a matrix where one critical finding sits in the top-right corner—high likelihood, catastrophic impact. That visual instantly cuts through the noise. It tells the executive team, "Fix this first. Everything else can wait."
This approach changes the conversation. You're no longer just the person who breaks things; you're the trusted partner who helps them make smart, risk-informed decisions. For a reseller, this is the foundation for building long-term, high-margin relationships. Our white label pentesting services provide the deep technical analysis, empowering you to deliver these high-level strategic insights under your own brand.
Building Actionable Remediation Roadmaps
Finding the problems is just the warm-up. The main event—and where you really prove your worth as an MSP or vCISO—is carving out a clear path to fix them. A great penetration testing report template doesn’t just dump a list of what's broken on your client's desk; it hands them a step-by-step, actionable roadmap they can actually follow.
Forget lazy, generic advice like "patch your servers." That’s the kind of fluff that gets your report ignored. Your clients are paying for real expertise, not for you to state the obvious. True value comes from guidance that is specific to their environment and, just as importantly, realistic.
Prioritizing Fixes Based On Risk and Effort
Not all vulnerabilities are created equal, and your client's time and money are never infinite. Your job is to help them point their resources where they'll have the biggest impact. The best remediation plans prioritize everything based on a simple but powerful matrix: risk vs. effort.
This means you need to break down your recommendations into clear buckets:
- Quick Wins (High Risk, Low Effort): These are the no-brainers. Think patching a critical remote code execution flaw on a public-facing server. These should be at the very top of the list, highlighted in red, with clear instructions to get them fixed now.
- Strategic Initiatives (High Risk, High Effort): These are the bigger projects that tackle systemic issues. This could be implementing proper network segmentation or rolling out a real identity and access management system. They won't get done in an afternoon, but they're critical for long-term security.
- Scheduled Maintenance (Low Risk, Low Effort): Think of these as good security hygiene. Cleaning up old, inactive user accounts or disabling legacy cipher suites. They should be done, but they don't need to derail more urgent work.
Don't just give your client a to-do list; give them a phased, strategic plan. This approach turns a scary list of vulnerabilities into a manageable project, positioning you as the go-to partner to lead them through it.
This is a massive value-add. You're not just the person who found the problems; you're the architect of the solution. This is exactly where our channel-only model is designed to make you shine. We deliver the expert findings from our deep-dive manual pentesting, and you get to own all the high-margin remediation work, driving new project revenue and cementing your role as that trusted advisor.
From Vague Suggestions To Concrete Steps
Let's get practical. Providing "concrete steps" means giving the client's technical team everything they need to implement the fix without having to go on a research expedition.
For instance, instead of just saying: "Remediate the outdated Apache Struts library."
A genuinely actionable recommendation looks more like this:
Vulnerability: Outdated Apache Struts Library (CVE-2017-5638)Recommendation:
- Immediately upgrade the Apache Struts library on web servers
[Server Name/IP]to version 2.3.32 or newer. - Have developers review the application code to ensure it isn't vulnerable to similar object-graph navigation attacks.
- As a temporary control, implement a web application firewall (WAF) rule to block common Struts exploit patterns until the patch is fully deployed.
- Reference the official Apache security bulletin for detailed patching instructions:
[Link to Advisory]
This level of detail is a complete game-changer. It turns your report into a working document, not just another binder on a shelf. The demand for this kind of detailed reporting is exploding globally. For example, the penetration testing market in the Asia-Pacific region is seeing massive growth thanks to new digital infrastructure and a surge in cyber threats. This trend shows that effective pentesting reports are critical for decision-making everywhere, and a solid template has to be adaptable. For more on these global trends, you can explore the market dynamics in this detailed report.
As a reseller, this is your cue. You can step in and offer your services to manage this whole process—from patch management to bigger architectural overhauls—further locking in that client relationship for the long haul.
Common Questions About Pentest Reports
If you've got questions, you're not alone. Let's run through some of the most common things MSPs and vCISOs ask us about using a penetration testing report template and delivering results that actually make an impact.
How Can I Effectively White Label A Pentest Report
Real white label pentesting is so much more than sticking your logo on a PDF. It’s about owning the entire client conversation. Your brand, your strategic advice, and your remediation plan need to be front and center, proving your value as their go-to security partner.
The best templates are built for this. They have sections you can completely customize—your company info, the executive summary, and the remediation roadmap. Our entire channel-only partnership is designed to make you the hero. We handle the deep technical work with our manual pentesting and AI pentesting (Node Zero), and you deliver the complete, branded report as a key part of your vCISO or managed security offering. We never compete with you.
What Is The Difference Between A Vulnerability Scan And A Pentest Report
It’s a night-and-day difference, and it’s a critical one to explain to your clients. They need to understand why they're paying for a premium service, not just a cheap scan. Don't let them get the two confused.
- A vulnerability scan report is just an automated, noisy list of potential problems. Think of it as a security system that beeps every time a leaf blows past the window—it’s mostly false alarms with zero real-world context.
- A true manual penetration testing report tells the story of a simulated attack. It shows exactly how our ethical hackers actively exploited vulnerabilities to gain access, mimicking what a real attacker would do.
A scan says, "You might have an unlocked door." A pentest report says, "We walked through your unlocked door, accessed the customer database, and here’s exactly how to fix the lock, the frame, and the alarm system."
Our reports are proof that deep, manual pentesting delivers real, actionable intelligence—not just noise. To really nail this conversation, it's crucial to understand the difference between a risk assessment and a penetration test so you can properly educate your clients.
How Often Should My Clients Get A Penetration Test
The right schedule really depends on their industry, compliance pressures, and how quickly their tech environment changes. There's no one-size-fits-all answer, but there are some solid guidelines to follow.
For clients dealing with frameworks like PCI DSS or chasing SOC 2 compliance, an annual test is often a non-negotiable requirement. They'll also need re-testing after any major system changes.
For everyone else, we recommend an annual pentest as a solid baseline for good security hygiene. If you have clients in high-risk sectors or those who are constantly deploying new code, stepping up to a bi-annual or even quarterly test is a smart move.
The key is to frame it not as a one-off project but as a fundamental part of the ongoing security program that you, their trusted reseller, manage for them.
Ready to deliver pentesting reports that win clients and drive revenue? MSP Pentesting is your channel-only partner. We provide the expert, affordable pentesting so you can focus on being the hero.
Contact us today to learn more about our white-label pentesting services.


.avif)
.png)
.png)
.png)

