A network security assessment is a full health checkup for your client's digital world. Think of it like a friendly expert checking all the doors and windows in a building before a real burglar can. Our certified pentesters meticulously examine a network to find vulnerabilities.
This process is a deep-dive, manual pentesting effort. It uncovers weak spots in servers, firewalls, and applications that automated scanners miss. For any MSP or vCISO, this service is the foundation for protecting client data and meeting critical compliance goals.
What Are Network Security Assessments?

A real network security assessment is not just running an automated scanner. It’s a thorough process where our certified professionals—like our OSCP, CEH, and CREST pentesters—manually search for security holes. They look for weaknesses that a real attacker could exploit.
This assessment provides the proof of due diligence needed for standards like SOC 2, HIPAA, PCI DSS, and ISO 27001. It answers the most important questions a business has about its security: Where are our biggest security gaps? How would a real attacker get in? What's the fastest way to fix these issues?
For GRC and CPA firms, offering these assessments shows a true commitment to your client's total health. You move beyond simple audits into proactive protection. As a channel-only partner, we provide fast, affordable, and manual assessments that you can white label and resell as your own.
Why MSPs Should Offer Pentesting Services
For your clients, operating without a network security assessment is a huge gamble. The goal is to find weaknesses before an attacker does. It’s about proactive risk assessment, not waiting for a breach notification.
A professional assessment hunts down vulnerabilities first. This drastically reduces the chance of a data breach that could wreck your client's finances and reputation. Offering these services positions you as a strategic partner, not just an IT provider.
When an auditor for SOC 2, HIPAA, or PCI DSS shows up, a detailed penetration testing report is exactly what they want to see. It’s proof that your client is serious about protecting data. It's the difference between a smooth audit and a nightmare of fines.
As a channel-only partner, we never compete with you. We give you the expert-led, certified firepower to deliver these critical services under your own brand. Our white label pentesting is built to be affordable and fast, with reports from our OSCP, CEH, and CREST certified team delivered in about a week.
Understanding Different Types Of Security Assessments
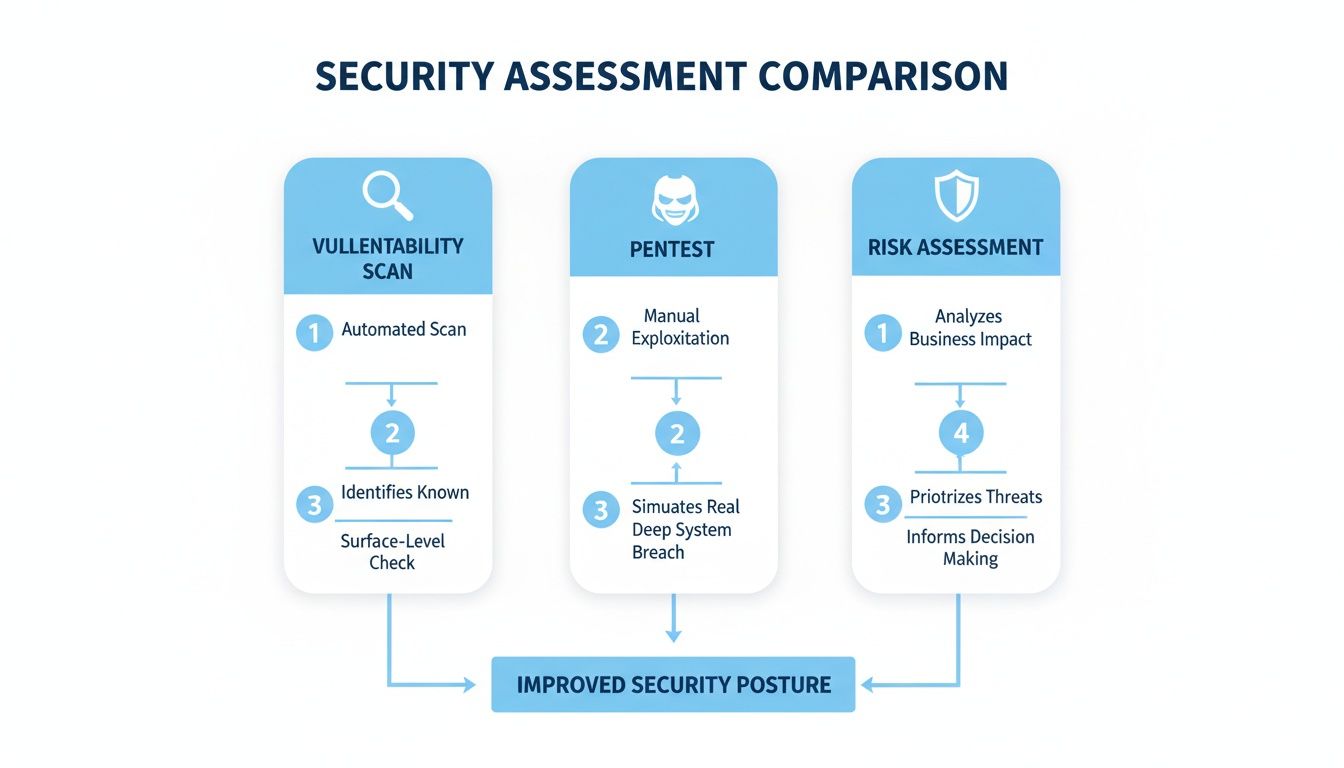
Not all assessments are the same. A vulnerability scan is like a quick check-up. It uses automated tools to find common, known weaknesses like unpatched software. It’s a good first step but often produces a lot of noise and false positives.
A penetration test, or pentest, is a real-world attack simulation. Instead of just listing potential flaws, our certified ethical hackers actively try to exploit them. This hands-on, manual pentesting approach proves which vulnerabilities pose a genuine threat.
A vulnerability scan tells you a door might be unlocked. A pentest has a certified expert actually try to open the door and see what they can steal. Our OSCP, CEH, and CREST certified pentesters uncover complex flaws that automated tools always miss. This is the only way to meet strict compliance standards.
We also offer different angles of attack. External pentesting tests your client’s internet-facing defenses, like firewalls. Internal pentesting simulates what an attacker who is already inside the network could do, like a disgruntled employee.
How Our Manual Pentesting Process Works
A professional penetration test is a structured, methodical process. This disciplined approach is what separates a genuine manual pentesting engagement from a simple automated scan. For any MSP or GRC firm, understanding these stages helps show clients the real value of the work.
First is the planning stage. We work with you to define the scope and goals to ensure the pentest aligns with your client’s business objectives and compliance needs for frameworks like SOC 2 or HIPAA. Our OSCP and CREST certified experts then perform reconnaissance, gathering public information just like a real attacker.
Next, we move to scanning and enumeration. We use a mix of tools and manual techniques to map the attack surface and identify potential entry points. This detailed blueprint of the environment fuels the next phase: gaining access. Here, our experts use their creativity to exploit vulnerabilities and breach systems, proving which risks are real.
Once inside, we try to maintain access and move through the network to show the potential damage of a breach. Finally, we provide a clear, straightforward report that you can white label. It breaks down every vulnerability, its risk level, and gives you concrete steps to fix it. Our pen testing methodology is designed for clarity and action.
How to Resell White Label Pentesting
The security industry has a problem: inflated prices and long lead times. Your client needs a penetration test for a compliance deadline, but you get a high quote and a six-week wait. This is a massive opportunity for you to offer a better, faster, and more affordable solution.
This is where white label pentesting comes in. By partnering with a dedicated, channel-only provider, you can offer top-tier, manual pentesting under your own brand. We handle all the technical work behind the scenes, becoming your on-demand security team.
The process is simple. Our certified OSCP, CEH, and CREST pentesters do the work, and you deliver the final, branded report to your client. As a channel-only partner, we never compete with you. You get access to an elite team without the huge cost of building one yourself, with comprehensive reports delivered in about a week.
Offering white label penetration testing makes you a strategic security advisor. When a client needs to pass an audit for SOC 2 or HIPAA, you have a fast, credible, and affordable answer. You become the first person they call for their biggest security challenges.
Choosing Your Ideal Pentesting Partner

Your choice of a pentesting partner reflects on your own credibility. The first rule is simple: they must be channel-only. You need a partner who supports you, not competes with you. We will never poach your clients.
Next, look for certified experts. A serious penetration testing firm will have a team with top-tier certifications. The big three you should look for are OSCP, CEH, and CREST. These prove the team has the real-world skills to deliver a professional network security assessment.
Demand a manual-first methodology. Many companies just run automated scanners and call it a day. That is not a real risk assessment and will not hold up in a SOC 2 or PCI DSS audit. Manual pentesting is the only way to find the complex flaws that automated tools miss.
Finally, look at their speed and pricing. Deadlines are everything in the GRC world. You need a partner who delivers a comprehensive white label pentesting report within a week. The service must also be affordable, allowing you to build a healthy margin while providing incredible value. This is how you find the right pentest partner for your business.
Your Pentesting Questions Answered By Experts
As an MSP, vCISO, or GRC firm, you probably have questions about network security assessments. Let's get you some straight answers.
How Often Should My Clients Get A Penetration Test?
This depends on compliance rules and how often their environment changes. Regulations like PCI DSS require an annual penetration test, plus re-tests after major changes. For most businesses, an annual pentest is a great baseline. For high-risk industries, quarterly testing is a smarter move.
What Is The Difference Between Internal and External Tests?
An external network security assessment tests defenses from the outside, like a hacker on the internet trying to get in. An internal assessment assumes the attacker is already inside the network. This test shows how much damage a compromised account or malicious employee could do.
Why Is White Label Pentesting Important?
White label pentesting lets you offer expert security services under your brand. You partner with a specialized, channel-only company like us. We perform the manual pentesting and give you a detailed report with your logo on it, creating a new revenue stream without the high cost of an in-house team.
Why Is Manual Pentesting Better Than Automated Scanning?
Automated scanners find common problems but miss the bigger picture. They lack the creativity of a human attacker and can't understand business context. Manual pentesting, performed by our OSCP, CEH, and CREST certified experts, uncovers complex flaws that scanners are blind to. It provides a true risk assessment, which is essential for meaningful compliance.
Ready to offer fast, affordable, and expert-led pentesting services under your own brand? We are your dedicated, channel-only partner.
Contact us today to learn more about our white label pentesting solutions.


.avif)
.png)
.png)
.png)

