A solid third-party risk management process isn't about paperwork. It’s a game plan for finding, assessing, and shutting down risks your vendors bring to the table. This is about moving beyond checklists to actually understand how your partners impact your clients' security and compliance, making sure they don't become the weakest link.
Why Your Current Vendor Risk Process Is Failing You

Does your vendor risk process feel like you're just putting out fires with spreadsheets and endless questionnaires? You’re not alone. Most Managed Service Providers (MSPs) and vCISOs are stuck using outdated systems that create more noise than clarity.
You're juggling a growing list of vendors for your clients. Every single one—from their core SaaS platform to a simple marketing plugin—is a potential door for an attacker.
The industry is full of bad habits we've all accepted as a "functional" third-party risk management process. But these old-school methods just don't work anymore. They leave you and your clients wide open.
The Checkbox Compliance Trap
The biggest mistake is treating vendor risk like another compliance box to check. Your client needs a SOC 2 report, so you ask their key vendor for one, file it away, and move on. That's a disaster waiting to happen.
A compliance report is just a snapshot in time. It doesn't mean a vendor is secure today, and it definitely doesn't protect against real-world threats. Attackers couldn't care less about your paperwork. They're looking for unpatched systems, weak passwords, and sloppy cloud configurations—the stuff a piece of paper will never show you.
Relying on vendor self-assessments and stale reports is like letting a student grade their own test. You're getting the answer they want you to see, not the ground truth you need to make smart risk decisions.
Ignoring the Downstream Danger
Another massive blind spot is ignoring "fourth-party" risk. Your client’s marketing automation vendor is probably running on AWS and uses a dozen of its own third-party tools. A single vulnerability in any of those downstream providers can create a direct path back to your client's network.
A real third-party risk management process has to look at the entire supply chain. If you don't, you’re only seeing a sliver of the actual risk. This kind of oversight leads to ugly outcomes:
- Failed Audits: Auditors for frameworks like HIPAA and SOC 2 are getting much smarter about vendor management. A flimsy process is a guaranteed negative finding.
- Lost Clients: When a breach happens because of a vendor you supposedly vetted, that trust is shattered. It’s a fast way to lose a good client relationship.
- Reputation Damage: As the trusted reseller or service provider, the buck stops with you. In the client's eyes, their vendor's failure is your failure.
The solution isn't more paperwork. It's about a fundamental shift in thinking. A strong TPRM process isn't just a defensive chore; it's a service that adds real value. It's your chance to prove to clients that you're proactively securing their entire digital ecosystem. This means moving from "trust us" to "show us," where technical validation like manual pentesting actually confirms a vendor's security claims.
Building a Vendor Risk Management Framework That Works
You can't secure what you can't see. Before you can build a functional third party risk management process, you have to know exactly who you're dealing with. This means mapping every single third-party vendor that touches your clients' operations.
This isn't just about the big SaaS platforms. This inventory needs to include marketing plugins, outsourced development teams, freelance contractors—even the HVAC company with network access for their smart thermostat. If they connect to the network or handle data, they go on the list.
The goal here is to turn that messy, forgotten spreadsheet of vendors into a structured inventory that shows you where the real danger is.
Building Your Vendor Inventory
To get a complete picture, pull data from a few different places. Start with accounts payable, contract management systems, and single sign-on (SSO) logs. The finance department often has the most comprehensive list of who’s getting paid, which is a fantastic starting point.
But don't stop there. Talk to department heads. The marketing team’s shadow IT—that slick new analytics tool they signed up for with a credit card—isn't going to show up in any official procurement records.
Once you have your master list, enrich it with key details for each vendor:
- Business Owner: Who inside the client's organization owns this relationship?
- Service Provided: What exactly does this vendor do for the business?
- Data Access: What kind of data do they access, process, or store? (e.g., PII, PHI, financial data)
- System Criticality: If this vendor went down tomorrow, what would be the operational impact?
This initial mapping phase is a grind, but it's the foundation for everything else. Without it, you're just guessing.
Tiering Vendors by Actual Risk
With a complete inventory, the next step is to categorize or "tier" each vendor based on their risk profile. This isn't about treating every vendor the same; it's about focusing your energy where it matters most. A high-risk vendor needs a much deeper dive than a low-risk one.
For example, the vendor hosting your client’s production database is in a completely different universe of risk compared to the company that supplies office snacks. Your due diligence process has to reflect that reality.
A classic mistake is tiering vendors based on how much they cost. That vendor that costs $50 a month but has admin access to your client's entire cloud environment? That’s a far greater risk than the six-figure consulting firm that only gets anonymized data.
This visual shows a pretty typical risk distribution you'll see after an initial assessment.
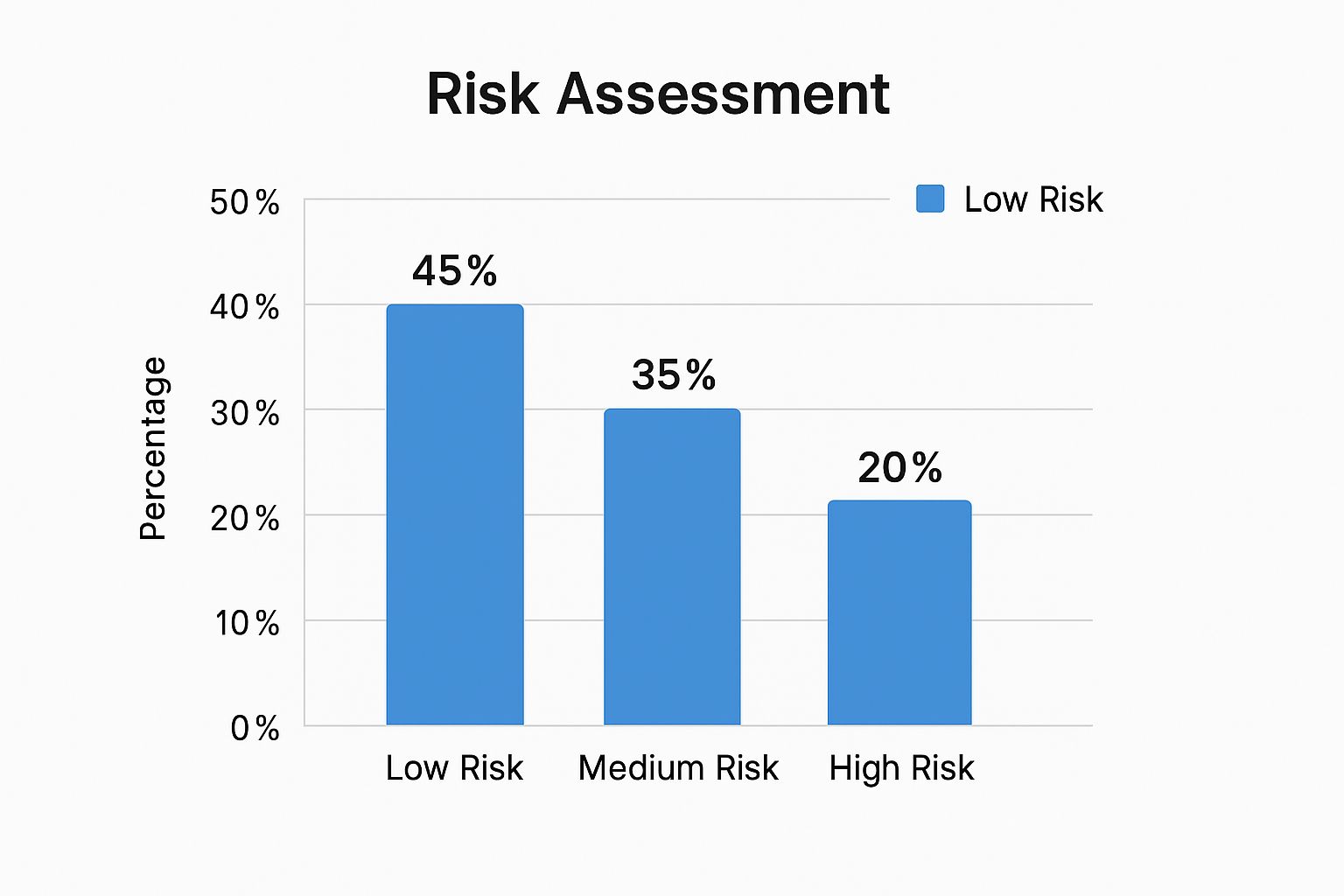
A big chunk of your vendors will likely fall into the low or medium-risk categories. This is good news—it lets you focus your most intensive due diligence efforts on the critical few that really matter.
To help with this, here's a simple framework that works well for most organizations.
Vendor Risk Tiering Framework
This table breaks down a simple, effective three-tier system. It helps you quickly classify vendors and understand what level of scrutiny each one needs.
Risk TierVendor DescriptionData Access LevelRequired Due DiligenceTier 1 (High)Vendors integrated into critical operations or with access to sensitive data (PII, PHI).Direct access to sensitive, regulated, or mission-critical data.Full security assessment, technical validation (e.g., pentesting), contract review.Tier 2 (Medium)Vendors with access to confidential, but not highly sensitive, business data.Access to internal business information or operational systems.Security questionnaire (e.g., SIG, CAIQ), review of SOC 2 report.Tier 3 (Low)Vendors with no access to sensitive data or critical systems. Minimal operational impact.No access to sensitive data or critical infrastructure.Basic vendor screening, confirmation of business legitimacy.
Using a framework like this is vital for efficiency. It’s the only way to stay sane, especially when you consider that most security teams are already stretched thin.
The Ncontracts 2025 Third-Party Risk Management Survey found that 73% of financial institutions have two or fewer full-time employees managing vendor risk, even though more than half of them oversee over 300 vendors. This just proves why a risk-based approach is the only way to effectively manage a large vendor ecosystem.
By mapping and tiering your ecosystem, you create a strategic roadmap. You now know exactly where to point your cannons, ensuring your vCISO or MSP team spends its valuable time scrutinizing the vendors that pose the greatest threat to your clients' security and compliance.
Executing a Vendor Due Diligence Process That Works

Alright, you've mapped your vendors and sorted them into tiers. Now comes the real work: the due diligence phase of your third party risk management process. This is where you separate partners from liabilities.
This isn't just about sending a questionnaire and checking a box. Those are just self-assessments. They give you the answers the vendor wants you to see. To get this right, you have to dig deeper and actually validate what they're telling you.
Deconstructing the SOC 2 Report
For your Tier 1 and most of your Tier 2 vendors, the first piece of evidence you'll look at is a SOC 2 report. A lot of people just glance at it, see the "unqualified" opinion, and file it away. Big mistake.
The real value is buried in the details. You need to read it like an attacker would, hunting for weaknesses and loopholes.
When you crack open a SOC 2, here's where to focus:
- The Auditor's Opinion: Anything besides an unqualified opinion is a massive red flag. Follow up on that immediately.
- Management's Assertion: This section is the vendor's management team explaining the controls they claim are in place. Your job is to compare this to what the auditor actually found.
- Exceptions and Deviations: No one is perfect. The auditor will list every time a control failed. You need to figure out if these are minor slip-ups or systemic security failures. A single failed control around access reviews could be all an attacker needs.
- Subservice Organizations (Fourth Parties): The report lists the vendor's own critical suppliers. This is your first real glimpse into your client's fourth-party risk. If their main SaaS provider is using a tiny, unknown data center, that's a risk you now own.
Reading a SOC 2 this way turns a boring compliance document into a powerful threat intelligence tool.
Beyond the Paperwork to Technical Validation
This is where you can seriously set your MSP or vCISO services apart. Paperwork can lie, but configurations and code don't. For your most critical Tier 1 vendors—the ones with deep hooks into sensitive data—you need to get technical.
This is exactly why services like pentesting exist. An annual manual pentesting engagement on a critical vendor isn’t just an expense; it's a non-negotiable verification step. It answers the one question a SOC 2 report can't: Can someone actually break in?
A clean SOC 2 report tells you the vendor claims to have strong locks on their doors. A manual pentest tells you if those locks can be picked. This shift from trust-but-verify to a true validation mindset is what separates a basic from an advanced third party risk management process.
As a reseller, offering white label pentesting is a total game-changer. You don't need to build your own team of expensive ethical hackers. Instead, you can partner with a channel-only provider (like us) to deliver high-end, affordable security testing under your own brand.
This solves a huge headache for your clients. They get the assurance they desperately need without the pain of finding, vetting, and managing a separate security firm.
For you, it creates a new, high-margin revenue stream that directly cuts down client risk and cements your role as their go-to security advisor. It makes the entire risk assessment process genuinely robust.
The Power of Manual Pentesting in TPRM
When you’re looking at a vendor, it's critical to know the difference between an automated vulnerability scan and a true manual pentesting engagement. Scanners are fine for spotting low-hanging fruit like missing patches, but they are completely blind to business logic flaws and complex attack chains.
A real human pentester thinks like an attacker. They can:
- Chain together multiple low-risk vulnerabilities to create a major breach.
- Spot business logic flaws that an automated tool would never understand.
- Adapt their attacks on the fly based on the target's defenses.
This is why manual pentesting is so essential for verifying the security of your high-risk vendors. It finds the exact kind of vulnerabilities that end up in the headlines. By building this level of technical scrutiny into your third party risk management process, you move past simple compliance and into actual risk reduction.
Integrating Security into Vendor Contracts and Onboarding
A verbal agreement isn't a security control. Once a vendor has made it through your due diligence gauntlet, the contract is where the rubber meets the road. This is your chance to make all those security promises legally binding and technically enforceable from day one. It's how you turn your third party risk management process from a polite suggestion into a firm mandate.
Handshakes and good faith won't cut it. Your contracts are where you set crystal-clear expectations and spell out the consequences if they're not met. If you aren't baking security requirements directly into your Master Service Agreements (MSAs) and Statements of Work (SOWs), you’re leaving a massive, gaping hole in your defenses.
Writing Security Clauses That Have Teeth
Sure, your legal team should always give contracts a final review, but as an MSP or vCISO, it's your job to make sure the technical security requirements are rock-solid. Vague language like "the vendor will maintain reasonable security" is completely useless. You need specifics.
Here are the non-negotiable clauses that must be in every contract for your Tier 1 and Tier 2 vendors:
- Right to Audit: This gives you the right to actually assess the vendor's controls. It might be a simple document review, or for your most critical vendors, it could mean the right to conduct your own manual pentesting. This is your leverage to verify their security, not just trust it blindly.
- Specific Breach Notification Timelines: Don't ever accept "in a timely manner." Your contract needs to demand notification within a hard deadline, like 24 or 48 hours, of a confirmed security incident that could impact your data or services.
- Data Handling and Encryption: Get specific. Mandate encryption standards for data at rest and in transit (e.g., AES-256, TLS 1.2+). Spell out how your data will be segregated and walled off from their other clients.
- Security Standards Adherence: Require them to adhere to specific frameworks relevant to your client's industry, like NIST CSF, or prove compliance with regulations like HIPAA or PCI DSS.
The contract is your ultimate backstop. When a vendor pushes back hard on a security clause, it's a huge red flag. It either means they know they can't meet the requirement or they just don't want to be held accountable for it. Either way, it’s a strong signal to think twice about the partnership.
Technical Onboarding and The Principle of Least Privilege
Once the ink is dry on the contract, the real technical work begins. This is where you actually enforce the security principles you just legally mandated. The single most important concept to hammer home here is the principle of least privilege.
It’s simple: every vendor account, every API key, every network connection gets the absolute minimum level of access required to do its job—and not one permission more. Over-provisioning access is one of the fastest ways a minor vendor compromise snowballs into a catastrophic breach for your client.
For your high-risk vendors, this means getting your hands dirty and implementing real technical controls:
- Network Segmentation: Isolate the vendor's access in its own dedicated VLAN or subnet. This way, even if their systems get popped, the blast radius is contained and can't spread across the entire network.
- Strict Access Controls: Use role-based access control (RBAC) to create specific, limited-permission accounts. Never give a vendor a domain admin account or a shared, generic login. That's just asking for trouble.
- API Key Scoping: If a vendor connects via an API, make damn sure the key is scoped with minimal permissions. It should only be able to read or write the specific data it needs, and nothing else.
For MSPs and resellers, this is a massive value-add. You can show your clients tangible risk reduction by properly configuring and locking down vendor access right from the start.
It’s also the perfect time to talk about ongoing verification. You can frame it by explaining that while you’ve set up strong controls, periodic checks are essential to make sure they hold up. This opens the door to introduce the value of attested 3rd party manual pentesting to ensure these controls can actually withstand a real-world attack.
This dual approach—legally binding contracts backed by technically enforced controls—is what makes a third party risk management process robust and truly effective. It's how you genuinely reduce risk, rather than just ticking a box for a SOC 2 audit.
Your Guide to Continuous Vendor Monitoring
Here's the biggest mistake you can make in your third party risk management process: thinking it's a one-and-done deal. Onboarding is just the start. The real challenge is ensuring a vendor who was secure yesterday is still secure today, tomorrow, and a year from now.
Vendor risk isn't static; it's a constantly moving target. A secure partner today could get breached tomorrow, misconfigure a cloud server next week, or let a critical patch slip next month. You have to treat TPRM as a lifecycle, not a project. This is where continuous monitoring comes in, and it's a massive opportunity for an MSP or vCISO to deliver serious, ongoing value.
Moving Beyond the Annual Review
The old-school annual security review is dead. Sure, it might check a box for a SOC 2 audit, but it leaves you completely blind for the other 364 days of the year. Real risk management demands a more dynamic approach—one that gives you a near real-time view of a vendor's security posture.
This means getting past static questionnaires and digging into live intelligence. Modern techniques and tools can help you keep a constant pulse on your most critical vendors.
Here’s what a modern monitoring strategy looks like:
- Security Posture Monitoring: Use tools to continuously scan a vendor's external attack surface for new vulnerabilities, misconfigurations, and expired certificates.
- Threat Intelligence Integration: Subscribe to threat feeds that alert you if a vendor's credentials pop up in a data dump on the dark web or if their IP ranges are linked to malicious activity.
- Adverse Media Monitoring: Set up alerts for negative news about a vendor—like reports of a data breach, financial instability, or regulatory fines. This can be your earliest warning sign of trouble.
This proactive approach completely flips the script. Instead of waiting for a vendor to tell you something’s wrong, you're actively hunting for indicators of risk.
The Critical Role of Periodic Technical Assessments
While automated monitoring is great for spotting surface-level issues, it can't tell you if a vendor's defenses can actually withstand a dedicated attack. For your high-risk vendors, periodic technical validation is non-negotiable. This is where you prove, not just assume, their security is holding up.
This is the perfect opportunity to offer recurring white label pentesting. By scheduling a manual pentesting engagement every 12-18 months for Tier 1 vendors, you provide clients with concrete evidence that their most critical partners are secure. You can explore our detailed guide on threat and vulnerability management to learn more about structuring these engagements.
Think of it like this: automated monitoring is your security camera system—it shows you what's happening on the perimeter. A manual pentest is your expert security team physically trying to break in. You absolutely need both to have a complete picture of your security.
This model is a win-win. Your client gets a massive reduction in their supply chain risk, and you, the reseller, build a high-value, recurring revenue stream. You deliver the service under your brand, using our channel-only team to do the heavy lifting. We provide the affordable, fast, and manual expertise; you get the credit and strengthen the client relationship.
This focus on proactive assessment is fast becoming the industry standard. The 2025 EY Global Third-Party Risk Management Survey found that 87% of companies are committed to taking urgent action if vendors fail to respond to risk questionnaires promptly. It also highlighted a growing focus on the supply chain, with 64% now assessing the "fourth-party" risks posed by their vendors' vendors. You can find more details in the full survey analysis on safe.security.
By implementing a continuous monitoring program backed by technical validation like manual pentesting, you transform your third party risk management process from a reactive, compliance-driven task into a proactive, security-first operation that provides genuine protection and peace of mind for your clients.
Don't Botch the Vendor Offboarding Process
When a contract ends with a vendor, it might feel like the job is done. But a sloppy offboarding process is a security incident just waiting to happen. This is the last, and arguably one of the most critical, phases of your third party risk management process.
Get it wrong, and you’re leaving a trail of active accounts, forgotten data, and open backdoors for attackers to find later.
A clean break isn't just good practice; it's mandatory. You absolutely need a repeatable checklist to make sure nothing gets missed. The goal here is simple: completely sever all access and ensure every bit of client data is securely handled. This is about more than just deleting a user account; you're systematically dismantling the digital connections you spent months or years building.
The Offboarding Checklist Every MSP Needs
Every single action you take during offboarding has to be documented. This isn't just for your own records—it creates a crucial audit trail that proves you’ve met your compliance duties for frameworks like SOC 2 or HIPAA.
Here's a practical checklist our MSP and reseller partners swear by:
- Kill All Logical Access: This is job number one, and it needs to happen immediately. Disable every user account, API key, and service account tied to that vendor. Don't just suspend them—get rid of them for good.
- Get Your Data Back (or Proof of Destruction): Make sure all client data is either securely returned to you or wiped from the vendor's systems. And don't just take their word for it. Demand a signed certificate of destruction as proof.
- Reclaim Physical Access: Get back every physical asset. This includes badges, keys, or any company-owned hardware they might have.
- Close Out the Paperwork: Settle the final invoice and formally terminate the contract. This prevents any auto-renewals or weird legal ties from lingering.
This disciplined approach protects your clients from the "ghost" accounts that attackers are actively hunting for. Organizations are relying more and more on third-party providers, and each new connection introduces another potential vulnerability. As security experts often point out, this growing ecosystem means your risk management has to cover not just your vendors, but their vendors, too.
A proper offboarding process is your final security control in the vendor lifecycle. It ensures that when a business relationship ends, the associated security risks end right along with it. Leaving any access intact is like giving a former employee your house keys and hoping for the best.
Third Party Risk Management FAQ
Got questions about the nitty-gritty of your third party risk management process? Good. Smart questions are what separate a secure business from the next headline. Here are some straight answers to what we hear most often from MSPs and vCISOs out in the field.
How Often Should We Really Be Assessing Critical Vendors?
For high-risk vendors—the ones with the keys to your client's kingdom—an annual deep-dive review is the absolute minimum. But that's just the baseline. You absolutely have to pair that with continuous monitoring to catch any red flags that pop up between those big reviews.
For your most mission-critical partners, you need to go a step further. We recommend a full technical validation, like our white label manual pentesting, every 12-18 months. This is how you verify their controls aren't just a paper tiger. Don't just trust the paperwork; make them prove they can stand up to a real attack.
What Is the Biggest Mistake MSPs Make with Vendor Risk?
The most common trap is treating TPRM like just another checkbox for compliance. It’s painful to see. Many MSPs will grab a vendor's SOC 2 report, file it away in a folder, and call it a day. That's not risk management; that's just paper shuffling.
The most effective MSPs and vCISOs treat this process as a legitimate security tool. They actually read those reports, rip them apart, and ask the tough follow-up questions. Then, they use technical assessments like manual pentesting to verify the vendor's claims. It’s about being proactive and preventing a breach, not just documenting compliance after one happens.
Can We Actually Resell Vendor Pentesting Services?
Absolutely. In fact, our entire business is built for the channel. As a channel-only partner, we provide affordable, fast manual pentesting that you can deliver to your clients under your own brand. It's that simple.
You sell the service and own the client relationship from start to finish. We handle all the heavy lifting on the technical side, completely behind the scenes. You get all the credit, lock in that client loyalty, and open up a powerful new revenue stream without the massive overhead of building an in-house pentesting team.
We are your partner, plain and simple. We never compete with you.
Ready to turn third-party risk management from a headache into a profit center? MSP Pentesting provides the channel-only, white-labeled pentesting services you need to secure your clients and grow your business. Contact us today and let's get started.


.avif)
.png)
.png)
.png)

