The vulnerability management game is a mess. You're drowning in a sea of CVSS scores, struggling with outdated testing methods, and dealing with pentesting partners who take forever. Then the ones who are good like Qualys, Tenable, etc charge a fortune. It feels like you're just patching the obvious while the real threats slip through. This constant reactive cycle of chasing alerts is unsustainable and, a massive waste of time. It burns out your team and leaves your clients exposed.
For MSPs, vCISOs, and GRC pros, this isn't just an IT headache. It's a huge business risk that hammers client trust and your reputation. The old way of reacting to every high-severity alert without a coherent strategy is totally broken. It’s time to shift from a chaotic scramble to a proactive, risk-based approach that actually crushes exposure. This isn't about working harder; it’s about working smarter and focusing your resources where they actually matter.
We're cutting through the noise to give you the actionable vulnerability management best practices you need to lock down your clients, ace compliance audits like SOC 2 and HIPAA, and grow your business. We'll cover everything from building a bulletproof asset inventory and implementing risk-based prioritization to establishing concrete remediation timelines and fostering killer cross-functional collaboration. Forget the generic advice. Let's dive into the specific strategies that separate the pros from the amateurs and turn your vulnerability management program from a cost center into a strategic weapon.
1. Establish a Comprehensive Asset Inventory
You can't protect what you don't know you have. It sounds cliché, but it's the absolute truth in cybersecurity. An effective vulnerability management program is built on the foundation of a comprehensive, up-to-date asset inventory. This isn't just a spreadsheet of servers anymore; it's a dynamic map of every piece of hardware, software, cloud instance, IoT device, and network appliance in an environment.
Without a complete inventory, you’re flying blind. You might run scans on known assets, but what about that forgotten dev server spun up in AWS or the marketing team's new SaaS tool connected via API? These "shadow IT" assets are where breaches happen. For MSPs and vCISOs managing multiple client environments, a rock-solid inventory process isn't just a best practice; it's a necessity for delivering real security value and a core component of compliance frameworks like SOC 2 and HIPAA.
Key Insight: A vulnerability scan is only as good as its scope. An incomplete asset inventory guarantees an incomplete and ineffective vulnerability management strategy, leaving critical blind spots for attackers to exploit.
How to Build Your Asset Inventory
Getting this right requires a multi-pronged approach. Relying on a single discovery method is a rookie mistake. Instead, combine several techniques to create a unified, accurate view of the entire IT estate.
- Automated Discovery: Use a mix of agent-based scanning on endpoints, passive network monitoring to catch unmanaged devices, and API integrations with cloud providers (AWS, Azure, GCP) to pull in cloud assets.
- Context is King: Don't just list an IP address. Tag assets with critical context: business owner, data sensitivity, operational importance, and physical location. This context is crucial for later prioritization steps.
- Constant Reconciliation: Your inventory is a living document. Regularly reconcile data from different discovery tools and your Configuration Management Database (CMDB) to identify discrepancies and keep the inventory fresh.
The following decision tree shows a simplified approach to selecting the right discovery method based on your primary asset environment.
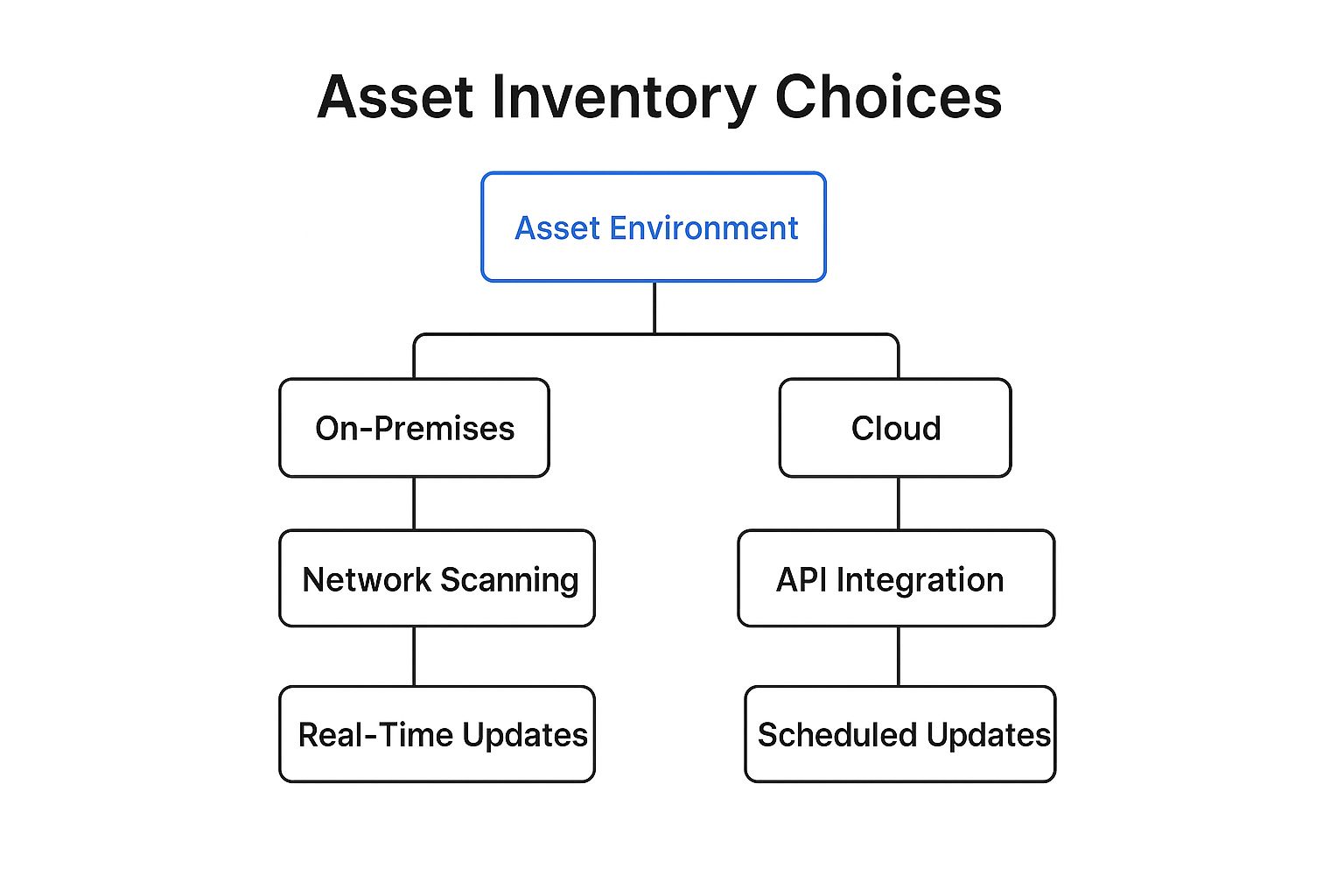
This visualization highlights that the core decision between network scanning and API integration depends on where your assets live, with the final step focusing on the desired frequency of updates for your vulnerability management program.
2. Implement Risk-Based Vulnerability Prioritization
Not all vulnerabilities are created equal. Chasing every "critical" finding based solely on its Common Vulnerability Scoring System (CVSS) score is a recipe for burnout and wasted resources. A modern, effective vulnerability management program moves beyond this outdated model to a risk-based approach, ensuring your limited remediation efforts are focused where they matter most.

This method prioritizes vulnerabilities by considering their real-world threat, not just their theoretical severity. It answers the crucial questions: Is this vulnerability actively being exploited in the wild? Is it on a business-critical asset? Answering these transforms your strategy from a high-volume whack-a-mole game to a precise, surgical strike against the threats that pose the biggest danger to the business. For MSPs and vCISOs, this is a game-changer, allowing you to demonstrate clear ROI by neutralizing the most significant risks first. Platforms like Tenable and Qualys have popularized this with methodologies like Vulnerability Priority Rating (VPR), showing how a risk-based model can slash critical backlogs by over 50%.
Key Insight: A CVSS score of 9.8 on a non-critical, internally isolated asset is far less of a priority than a CVSS 7.5 on a public-facing web server that is actively being exploited by ransomware groups. Context is everything.
How to Implement Risk-Based Prioritization
Shifting to a risk-based model means enriching vulnerability data with business and threat context. It’s about combining what’s vulnerable with what’s valuable and what’s exploitable. A thorough approach involves a continuous cycle of data aggregation and analysis.
- Combine Data Sources: Your prioritization engine needs more than just scan data. Integrate threat intelligence feeds for active exploits, asset criticality data from your inventory or CMDB, and business impact context from stakeholders.
- Contextualize with Business Impact: A vulnerability on the CFO's laptop or a database containing sensitive PII for SOC 2 compliance carries inherently more risk than one on a test server. Tagging assets with business criticality is non-negotiable.
- Automate Recalculation: The threat landscape changes daily. Use automation to continuously pull in new threat intel and recalculate risk scores. What was a low priority yesterday could become your top priority today if a public exploit is released. You can learn more about building a robust framework for this on our guide to risk assessment.
3. Establish Clear SLAs and Remediation Timelines
Discovering a vulnerability is only half the battle; fixing it is what actually reduces risk. This is where clear, documented Service Level Agreements (SLAs) for remediation become non-negotiable. An SLA defines the "shot clock" for fixing a vulnerability, creating a system of accountability and ensuring that critical issues don't get lost in a backlog of low-priority IT tickets.
For MSPs and their vCISO offerings, SLAs are a powerful tool for demonstrating value and managing client expectations. They transform vulnerability management from a chaotic, reactive process into a structured, measurable, and defensible program. When you're prepping a client for a SOC 2 or HIPAA audit, showing an auditor your defined SLAs and the metrics to prove you're hitting them is a massive win. It proves you have a mature process for handling risk.
Key Insight: Without remediation SLAs, your vulnerability management program is just a glorified reporting exercise. SLAs introduce urgency, accountability, and the necessary friction to force action and demonstrably reduce an organization's attack surface.
How to Build Your Remediation SLAs
Effective SLAs are not one-size-fits-all. They must be tailored to the organization's risk tolerance, balancing security needs with operational realities. This is a core component of effective vulnerability management best practices.
- Tier by Severity: The foundation of any good SLA is risk-based prioritization. Classify remediation timelines based on vulnerability severity (e.g., Critical, High, Medium, Low) and the business criticality of the affected asset. For instance, a critical vulnerability on an internet-facing production server demands a much faster response than a medium vulnerability on an internal development machine.
- Get Stakeholder Buy-In: Don't create SLAs in a vacuum. Work with business unit leaders and system owners to agree on timelines that are both aggressive and achievable. This collaboration prevents pushback and ensures everyone understands their responsibilities when the clock starts ticking. For example, JPMorgan Chase reportedly uses a 72-hour SLA for critical production vulnerabilities, a timeline that requires absolute buy-in from technical and business teams.
- Track and Report Everything: Use your vulnerability management platform or ticketing system to track the entire lifecycle of a vulnerability from discovery to closure. Regularly report on SLA compliance to leadership and clients. This data highlights systemic issues, identifies overburdened teams, and justifies resource allocation for security initiatives.
4. Integrate Vulnerability Scanning Across the DevSecOps Pipeline
Traditional vulnerability management often treats security as an afterthought, a final check before deployment that inevitably causes friction and delays. Modern, high-velocity environments can't afford that bottleneck. The solution is to shift security left by embedding vulnerability scanning directly into the software development lifecycle (SDLC), a core principle of DevSecOps. This approach makes security a shared responsibility, not just a problem for the security team to solve at the end.

For MSPs and vCISOs managing clients who develop their own software, introducing this practice is a game-changer. It transforms vulnerability management from a reactive, periodic audit into a proactive, continuous process. By catching flaws early, you drastically reduce the cost and complexity of remediation, prevent insecure code from ever reaching production, and demonstrate a mature security posture crucial for compliance frameworks. Leaders like Shopify have used this method to prevent thousands of vulnerable deployments, proving its real-world value.
Key Insight: Finding a vulnerability in a developer's IDE is a quick fix. Finding that same vulnerability in a production application months later is a fire drill. Shifting left isn't just a buzzword; it's a fundamental change in how you manage risk, cost, and speed.
How to Embed Security in the Pipeline
Integrating security scanning requires a strategic, phased approach to gain buy-in and avoid overwhelming development teams. The goal is to make security a seamless part of their existing workflow, not another frustrating hurdle.
- Start with Non-Blocking Scans: Begin by integrating Static Application Security Testing (SAST) tools like SonarQube or Checkmarx into CI/CD pipelines in a non-blocking or "audit" mode. This surfaces vulnerabilities without stopping builds, allowing developers to get used to the feedback.
- Provide Actionable Guidance: Don't just flag a problem. Ensure scan results provide clear context, code snippets, and specific remediation advice. Integrating tools directly into developer IDEs offers the fastest feedback loop, helping them learn secure coding practices on the fly.
- Introduce Gating and Policy: Once the process is established, create policies to "break the build" or block deployments for high or critical-severity vulnerabilities. This creates a hard security gate that enforces your standards automatically.
- Appoint Security Champions: Identify developers who are passionate about security and empower them as "security champions." They can advocate for best practices, help triage findings, and bridge the gap between development and security teams, accelerating adoption across the organization.
5. Implement Continuous Monitoring and Scanning
The days of quarterly vulnerability scans are long gone. In a modern threat landscape where new exploits are weaponized in hours, not months, a periodic "snapshot" of your security posture is dangerously insufficient. The only effective strategy is continuous monitoring, a practice that shifts vulnerability management from a scheduled event to an ongoing, real-time process. This provides constant visibility into your security posture and enables a rapid response to newly discovered threats.
For MSPs and vCISOs, this isn't just a technical upgrade; it's a fundamental shift in service delivery. Offering continuous monitoring demonstrates a commitment to proactive security, moving beyond checkbox compliance to offer genuine risk reduction. It’s the difference between telling a client they were secure last quarter and assuring them they are secure right now. This proactive stance is essential for maintaining trust and protecting client assets against fast-moving attackers.
Key Insight: Attackers operate 24/7. Your vulnerability management program must do the same. Continuous monitoring closes the critical gap between when a vulnerability is discovered and when your team can find and fix it.
How to Implement Continuous Monitoring
Effective continuous monitoring isn't just about cranking up scan frequency; it's about a strategic blend of technologies and processes that provide comprehensive coverage without overwhelming your team or network resources.
- Combine Scanning Methods: Deploy a mix of agent-based monitoring on critical endpoints for real-time data, authenticated network scans for deep internal visibility, and unauthenticated external scans to see what an attacker sees. This multi-layered approach ensures no asset is left unmonitored.
- Balance Frequency and Impact: Don't scan every asset every hour. Use intelligent scheduling based on asset criticality. Your public-facing web servers and domain controllers need more frequent attention than a low-priority internal file server. This optimizes resources and reduces operational noise.
- Correlate and Filter Alerts: Raw vulnerability data is just noise. Implement tools that correlate findings, filter out false positives, and enrich alerts with threat intelligence and business context. This ensures your team focuses on the vulnerabilities that pose a genuine, immediate threat.
Ultimately, continuous scanning is one piece of a larger security puzzle. To truly understand your risk, you need to validate these findings. Understanding how different security assessments compare, such as continuous vulnerability scanning versus more in-depth AI or manual pentesting, is critical for building a mature program. Learn more about the differences between vulnerability scanning, AI pentesting, and manual pentesting to determine the right testing methodology for your clients.
6. Maintain Detailed Vulnerability Documentation and Reporting
A vulnerability management program that operates in a black box is useless. If you can't show progress, demonstrate risk reduction, or communicate status to stakeholders, you’re just spinning your wheels. This is where detailed vulnerability documentation and reporting become critical. It’s the mechanism for translating raw technical data into business-relevant insights that drive action and prove value.
For vCISOs and MSPs, reporting isn't just about sending a CSV of vulnerabilities; it's a key deliverable that demonstrates the effectiveness of your security program. Proper documentation is also non-negotiable for compliance frameworks like PCI-DSS and SOC 2, which require clear audit trails of how vulnerabilities are identified, assessed, and remediated. Without this, you fail the audit, simple as that.
Key Insight: Reporting is not the end of the vulnerability management process; it is the engine that powers it. Effective reports provide the visibility needed for executive buy-in, budget allocation, and operational accountability.
How to Build Your Reporting Framework
Great reporting tells a story. It answers key questions for different audiences, from a CEO asking "Are we secure?" to an IT admin asking "What do I need to patch today?" Building a solid framework means creating targeted, automated, and context-rich reports.
- Tailor Reports to the Audience: Don't send a 500-page vulnerability scan PDF to the board. Create distinct reports: high-level executive dashboards with risk trends and ROI, tactical reports for IT teams with specific remediation instructions, and detailed evidence for compliance auditors.
- Focus on Actionable Metrics: Vanity metrics like "total vulnerabilities found" are meaningless without context. Instead, track metrics that drive decisions: Mean Time to Remediate (MTTR), vulnerability age by severity, and remediation progress against Service Level Agreements (SLAs).
- Automate and Integrate: Manually building reports is a time sink and prone to errors. Leverage your vulnerability management platform's reporting engine or integrate data into BI tools like Power BI or Splunk to automate report generation and distribution, ensuring stakeholders get timely, consistent updates.
7. Establish Cross-Functional Collaboration and Communication
Vulnerability management isn't just a security team problem; it's an organizational one. Siloing vulnerability data within the security team is a surefire way to slow remediation to a crawl and create friction. The most successful vulnerability management best practices are built on seamless collaboration between security, IT operations, development, and business units. This means breaking down walls and creating shared ownership of risk.
This collaborative approach, often central to the DevSecOps movement, ensures that the people who can actually fix the vulnerabilities (developers and system admins) are involved early and often. For MSPs and vCISOs, fostering this culture within a client's organization is critical. It transforms the relationship from a simple service provider to a strategic partner, embedding security into their operational DNA and proving immense value for compliance audits like SOC 2.
Key Insight: A vulnerability ticket assigned without context or conversation is just noise. True remediation velocity is achieved when IT, security, and business teams work from a shared understanding of risk and a common goal.
How to Build a Collaborative Framework
Creating a culture of shared responsibility doesn't happen overnight. It requires deliberate effort to build bridges, establish clear communication channels, and create workflows that empower every team to contribute to security.
- Create Security Champions: Identify and empower individuals within development and IT operations to act as security advocates. These champions become the go-to resource for their teams, translating security requirements into practical actions and building trust between departments.
- Integrate into Existing Workflows: Don't force developers and IT admins to use yet another security tool. Instead, integrate vulnerability data directly into the platforms they already live in, like Jira, ServiceNow, or Slack. This reduces friction and makes security a natural part of their daily tasks.
- Establish Regular Cross-Functional Reviews: Schedule recurring meetings with key stakeholders from each department. Use this time to review high-priority vulnerabilities, discuss remediation challenges, and celebrate successes. This creates a transparent feedback loop and ensures everyone is aligned on priorities. Capital One’s DevSecOps transformation is a prime example of embedding this shared responsibility model at scale.
8. Develop Comprehensive Patch Management and Remediation Processes
Identifying vulnerabilities is only half the battle; closing the gaps is where the real work happens. A robust vulnerability management program hinges on having well-defined, repeatable processes for patch management and remediation. This isn't just about clicking "update" when a notification pops up. It's a structured approach to deploying fixes without breaking critical business operations, a constant balancing act for any MSP or vCISO.
Without a formal process, you’re stuck in a chaotic cycle of reactive firefighting. A critical zero-day drops, and teams scramble, often deploying untested patches that cause more downtime than the vulnerability ever could. A mature remediation process ensures that patches are tested, deployed in a controlled manner, and that rollback plans are ready if things go sideways. For organizations navigating compliance frameworks like SOC 2, a documented patch management policy isn't just a suggestion; it's a hard requirement.
Key Insight: The goal of remediation isn't just to apply a patch. It's to reduce risk in a controlled, predictable, and auditable manner. Sometimes the best immediate action isn't a patch but a compensating control.
How to Build Your Remediation Process
Building an effective process means preparing for multiple scenarios, from routine updates to emergency, out-of-band patches for critical exploits. This framework ensures you can act swiftly and safely.
- Standardized Patching Cadence: Establish a regular schedule for patching (e.g., "Patch Tuesday"). This creates predictability for business units and ensures systems are consistently updated. Use tools like Microsoft's Windows Update for Business or Red Hat Satellite to manage staged deployments.
- Develop Compensating Controls: Not all vulnerabilities can be patched immediately. An application might have a dependency on a vulnerable library, or a patch might not be available for legacy hardware. In these cases, implement compensating controls like stricter firewall rules, network segmentation, or enhanced monitoring as temporary measures.
- Practice Emergency Procedures: Don't wait for a real crisis to test your emergency patching protocol. Run tabletop exercises to simulate a zero-day response. Who approves the emergency change? How is the patch deployed? What is the communication plan? Having these answers ready is critical. This level of preparedness is often validated during security assessments, and you can learn more about how white-label pentesting can help validate these processes for your clients.
Ready to Partner Up and Crush Your Security Goals?
Look, vulnerability management isn't a "set it and forget it" task. It's a continuous, dynamic cycle that separates the pros from the amateurs. We’ve walked through the eight core vulnerability management best practices that form the bedrock of any serious security program. From building a rock-solid asset inventory to establishing ironclad remediation SLAs, each practice is a critical gear in a machine designed to keep your clients safe and compliant.
Mastering these fundamentals is non-negotiable for any MSP, vCISO, or CPA firm aiming to deliver real value. You can’t just run a scan and call it a day. The real magic happens when you move beyond basic discovery and into a strategic, risk-based approach. It’s about understanding what matters most, acting decisively, and proving your value with clear, comprehensive reporting. This is how you build trust and become an indispensable partner, especially for clients navigating tricky compliance frameworks like SOC 2 or HIPAA.
Your Key Takeaways: From Theory to Action
Let's cut through the noise. If you remember nothing else, burn these points into your brain:
- You Can't Protect What You Can't See: Your asset inventory is the foundation. If it's weak, your entire security posture is built on sand. Make it comprehensive and keep it current.
- Not All Vulns Are Created Equal: Stop chasing every single finding. A risk-based approach using frameworks like EPSS is the only scalable way to prioritize. Focus on what attackers are actually exploiting.
- Speed and Collaboration Are Your Superpowers: A vulnerability isn't fixed until it's patched. Tight SLAs and strong communication channels between security, IT, and dev teams are what turn findings into fixes.
- Documentation Is Your Shield: When the auditors come knocking, or a client questions your process, detailed documentation and clear reporting are your best defense. It proves diligence and demonstrates value.
Implementing these vulnerability management best practices transforms your service from a simple checklist item into a strategic security function. It’s the difference between just selling a tool and delivering a true, security-focused outcome.
The Next Level: Validating Your Defenses
Here’s the hard truth: a clean vulnerability scan is a great start, but it’s not the finish line. It tells you what could be wrong, but it doesn't prove your defenses will hold up against a determined attacker. To truly validate your security controls and show clients you’ve got their back, you need to think like the enemy.
That’s where offensive security comes in. Manual pentesting is the ultimate reality check. It moves beyond theoretical risk to demonstrate real-world, exploitable pathways into a network. For MSPs and vCISOs, offering robust pentesting services as a reseller is a massive differentiator. It elevates your offering, deepens client trust, and unlocks higher-margin revenue streams. But finding a reliable partner can be a nightmare of inflated prices, slow turnarounds, and vendors that compete for your clients.
We built our entire business to solve that problem. We are a channel-only partner, meaning we exist to make you the hero. We offer affordable, fast, and expert-led manual pentesting and AI pentesting (Node Zero) that you can white label and resell as your own. We handle the complex testing, you deliver the high-value results. It’s a win-win that helps you secure your clients and grow your business without the typical headaches.
Ready to add expert-led, white label pentesting to your service catalog? MSP Pentesting is your dedicated, channel-only partner, providing the offensive security services you need to validate defenses and meet compliance demands. Partner with us at MSP Pentesting and let's start securing your clients together.


.avif)
.png)
.png)
.png)

