Penetration testing, or pentesting as it's often called, is a simulated cyberattack against your client's computer system to check for exploitable vulnerabilities. Think of it like hiring a security expert to try and break into a building. They check the doors, windows, and security system to find weak spots before a real burglar does.
We hire certified ethical hackers to probe your client's systems, networks, and applications to find these vulnerabilities first. It's a hands-on way to see how strong their security really is. This approach gives you tangible proof of a company's security posture, helping you protect your clients and meet compliance requirements.
What Does Penetration Testing Involve?

As an MSP or vCISO, you are the first line of defense for your clients. A pentest is one of the most powerful tools you can offer. It moves far beyond simple automated scans to give a real-world assessment of how secure they actually are. It’s not just about finding problems; it’s about understanding their potential business impact.
The entire point is to identify weaknesses and then safely exploit them, just like an attacker would. This process helps your clients get concrete answers to critical security questions. This includes whether an attacker can breach their defenses, what an insider threat could access, and if their web applications are vulnerable.
Why Is Pentesting Important For Your Clients?
The need for this service is exploding. The global pentesting market is on track to jump from USD 3.09 billion in 2026 to USD 7.41 billion by 2034. This isn't surprising, as cyber threats get more sophisticated and compliance requirements get stricter. You can dig into the specifics of this market growth in this detailed report.
This huge demand creates a massive opportunity for partners in the MSP, vCISO, and GRC spaces. Offering white label pentesting is no longer just a nice add-on. It's becoming a non-negotiable part of any mature security program that helps clients meet regulations like SOC 2 and HIPAA.
Why Is Manual Pentesting Better Than Scanning?
It’s critical to understand the difference between a pentest and a simple vulnerability scan. A vulnerability scan is an automated tool that just checks for known issues. It's like walking around a building and noting which doors are unlocked. A manual pentesting engagement, on the other hand, is done by a certified human expert who brings creativity and critical thinking to the table.
A pentester doesn't just find the unlocked door. They walk through it, see what sensitive data they can access, and show you exactly how much damage could be done. This human-led approach is the only way to find complex business logic flaws that automated tools always miss. Our pentesters hold top-tier certifications like OSCP, CEH, and CREST, guaranteeing a deep, intelligent analysis that goes way beyond what a scanner can do.
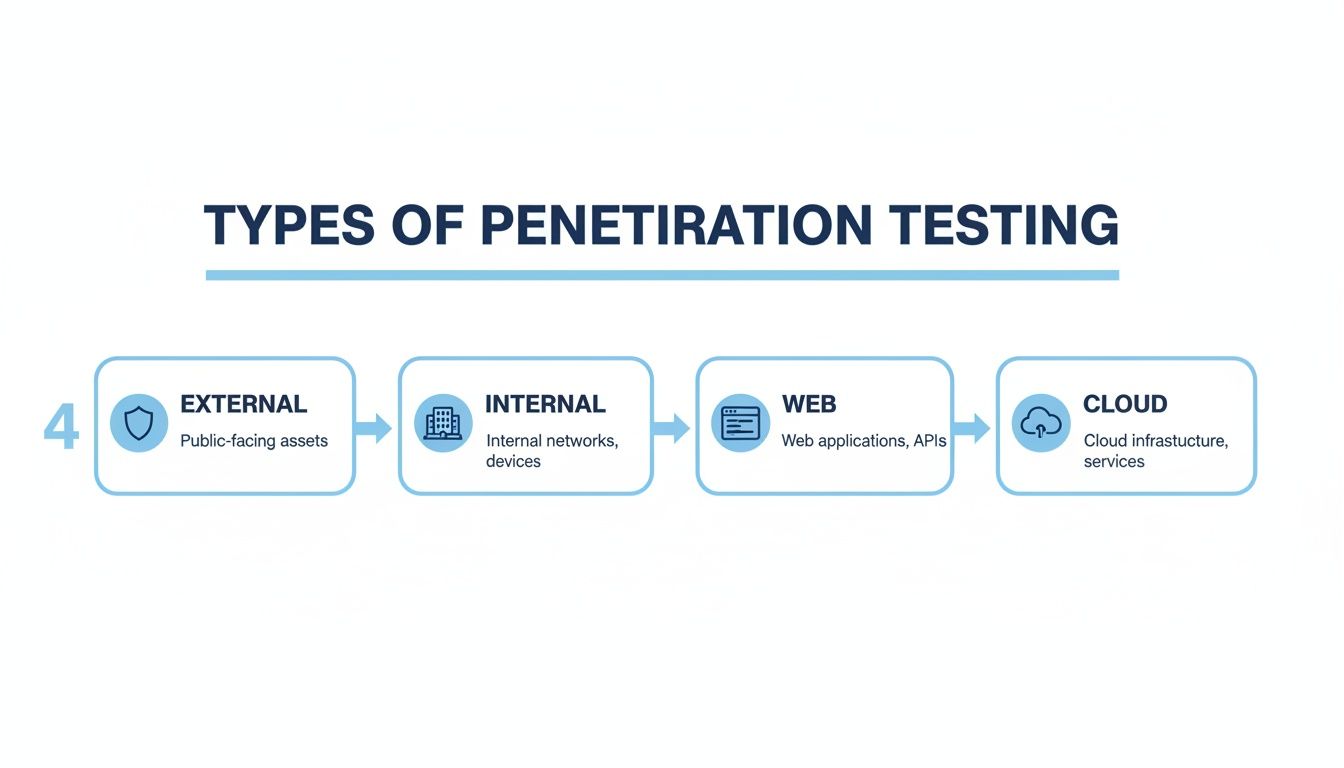
What Are The Different Types Of Pentesting?
Penetration testing isn’t a one-size-fits-all service. Different types of pentests are designed to check different parts of a company's security. As an MSP or vCISO, knowing the difference helps you guide clients to the right assessment for their security and compliance goals.
An external network pentest is like casing a building from the outside. Our ethical hackers look at everything the public can see to find a way in. This is a foundational test for compliance frameworks like PCI DSS and SOC 2. Internal pentesting assumes an attacker is already inside, showing what a malicious insider could do.
Web and mobile application pentesting zeroes in on custom-built apps, looking for coding flaws that could lead to data theft. Cloud infrastructure pentesting checks the security of services in AWS, Azure, or GCP. A simple misconfiguration in the cloud can expose huge amounts of data, making this test critical for a modern risk assessment.
How Does The Penetration Testing Process Work?
A real penetration testing engagement is a methodical, multi-stage process. This structured approach is what separates a genuine manual pentest from a simple automated scan. It’s also why this level of testing is required for tough compliance frameworks like PCI DSS and ISO 27001.
The first stage is scoping, where we define the rules of engagement and what systems are in play. Next is reconnaissance, where our ethical hackers gather intelligence to map out the attack surface. The third stage is exploitation, where our OSCP and CREST certified pros actively try to bypass defenses and gain access. This is the heart of manual pentesting.
After gaining access, the post-exploitation phase begins. Our team tries to move deeper into the network to find sensitive data, showing the true business impact of a flaw. Finally, we provide a clear, actionable report detailing every finding and providing step-by-step guidance on how to fix them. Our reports are fast, affordable, and delivered as a white label pentesting document you can brand as your own.
How Does Pentesting Help With Client Compliance?
For your clients, navigating compliance for frameworks like SOC 2, HIPAA, and PCI DSS is a huge challenge. Penetration testing is often a non-negotiable requirement for these standards. It provides the hard evidence that an organization has actively tried to find and fix its own security weaknesses.
For instance, PCI DSS requires both internal and external penetration testing at least once a year. Healthcare organizations under HIPAA must conduct a thorough risk assessment, and a pentest is the best way to find vulnerabilities that could lead to a breach and massive fines.
Failing a compliance audit can result in crippling financial penalties and reputational damage. Proactive, affordable testing is an insurance policy against a business-ending disaster. When you hand a client a thorough white label pentesting report, you’re giving them a roadmap to a stronger security posture and a tangible asset to show auditors.
How Do I Choose A Pentesting Partner?
Choosing a white label pentesting provider is a critical decision. The compliance and managed service industry has a problem with inflated prices and long lead times. As an MSP, vCISO, or GRC consultant, you need a partner built to solve these problems with affordable, manual, and fast testing.
First, find a partner who is channel-only. This means they will never compete with you or try to undercut your client relationships. Their success should be tied to yours. They should act as your silent, expert backend while you own the trusted client relationship.
Second, prioritize manual pentesting and certifications. Real security value comes from human experts with certifications like OSCP, CEH, and CREST. These credentials prove the testing goes beyond a simple scan and meets the high standards required for SOC 2 and PCI DSS.
Finally, focus on affordability and speed. You need an affordable partner who understands the reseller model and protects your margins. Speed is just as important. Our process delivers comprehensive reports within one week of test completion, giving you the agility your clients demand.
What Are The Most Common Pentesting Questions?
As you offer penetration testing, your clients will have questions. The most common one is how often they need a test. For compliance like PCI DSS, it's required annually. A good rule of thumb for all clients is at least once a year, or more frequently for high-risk businesses.
Another key question is the difference between a pentest and a vulnerability scan. A scan is an automated tool that finds potential issues. A penetration testing engagement is a manual process where a certified ethical hacker simulates a real attack to prove the risk and show the business impact.
We are a 100% channel-only partner, meaning we provide complete white label pentesting. Your brand is on the report, and we work as a silent extension of your team. And because speed is critical, we deliver full, actionable reports within one week of test completion, making us the fast and affordable choice for your business.
Ready to provide your clients with the certified, manual penetration testing they need to stay secure and compliant? Contact us today to learn more about our channel-only partnership and how our affordable, fast, and white-labeled services can help you grow your business. Visit us at https://msppentesting.com.



.avif)
.png)