A network security audit is like a health check for your client's digital world. It’s not just an automated scan. It's a hands-on investigation by certified pros who think like attackers to find vulnerabilities that software tools miss.
What a Network Security Audit Really Is
An automated vulnerability scan is like a security guard checking if doors are locked. It's a good first step, but it's basic.
A manual network security audit is like hiring a team to try and break in. They test every entry point with creative, human-led techniques to find what breaks. This is how you become an indispensable security partner, providing proof you are protecting data and helping with SOC 2, HIPAA, and PCI DSS compliance. The goal is to find hidden risks before attackers do.
A network security audit answers the question, "How would we hold up against a skilled attacker?" This is the insight that builds trust.
The need for these audits is growing. Cybercrime is projected to cost the world $10.5 trillion by 2025. Hackers attack a computer with internet access every 39 seconds, so periodic audits are a core part of any real defense. This flow chart shows how a proper security check creates a path from finding weaknesses to building stronger defenses.
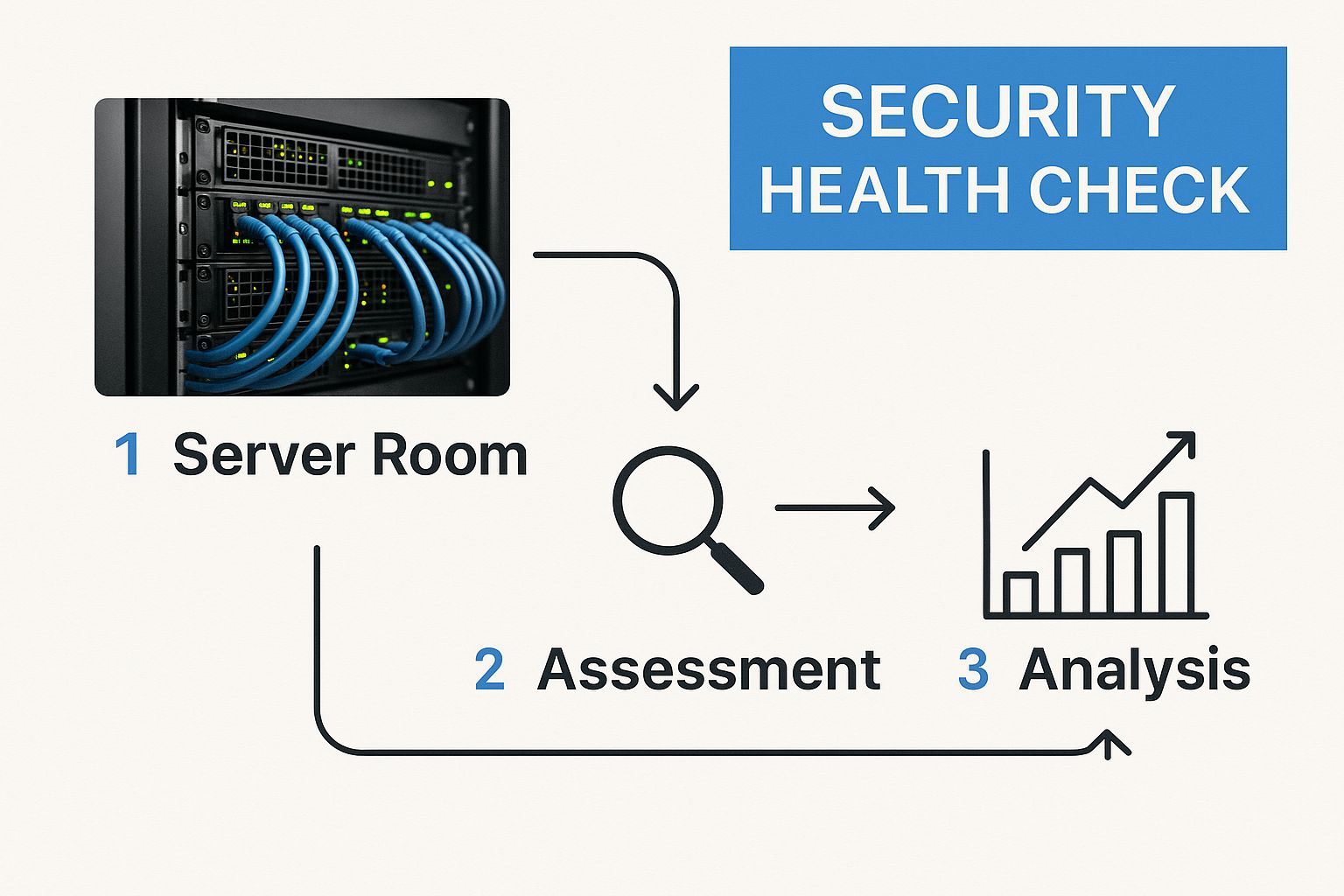
A real audit is about creating a cycle of continuous improvement. It combines hands-on testing with a review of security policies, connecting a simple firewall error to a potential data breach. A quick scan is never enough—you need the critical thinking that only a certified expert can provide. Our pentesters hold top certifications like OSCP, CEH, and CREST, giving them the skills to find what automated tools cannot.
By working with a channel-only provider, you can offer this high-value service. Our white label pentesting is affordable and fast, letting you deliver expert results without the high overhead. This is a key part of a larger strategy, which you can read more about in our guide on risk assessment.
The Manual Audit Process From Start to Finish

A real manual network security audit is a methodical, human-led process. It uncovers the real-world risks that automated tools always miss. Think of it as a friendly hacker trying every door and window while taking detailed notes for you. For an MSP, vCISO, or GRC company, knowing these steps shows clients the value of a comprehensive risk assessment by certified pros.
First, we work with you (our reseller partner) to map out the pentesting scope. We figure out what really matters to your client's business. We identify critical assets, define network boundaries, and set the rules of engagement to avoid disrupting daily operations. Getting the scope right ensures our OSCP and CEH certified pentesters focus where it counts, keeping the audit affordable and effective.
Next, our team starts intelligence gathering, just like a real attacker. We use various techniques to map the network, identify targets, and collect intel. This phase is quiet and non-intrusive, building a blueprint of the network's footprint. As part of this, we also run checks for known issues, a process we cover in our guide to security vulnerability scanning.
This is where real manual pentesting begins. Our testers actively probe for holes, hunting for complex logic flaws and tricky misconfigurations. It's not about running a tool; it’s about a certified expert using creativity to chain small issues into a major security breach. When a vulnerability is found, our testers carefully exploit it to provide undeniable proof of the risk, which is what compliance frameworks like PCI DSS and ISO 27001 demand.
The final step is a comprehensive, white label pentesting report you can put your brand on. It’s a clean, actionable document with an executive summary, detailed technical findings, and clear recommendations on how to fix every issue. We give you the expert findings so you can be the indispensable security partner your clients rely on.
Why Audits Are Essential for MSP and vCISO Growth
Offering a network security audit is fundamental for any MSP, vCISO, or GRC firm looking to grow. Clients count on you to shield them from cyber threats. A proactive audit is the best way to deliver on that promise. Finding and patching security holes before a breach proves your value as a strategic advisor.
A proper network security audit flips the script on security spending. Instead of putting out fires, you give clients a roadmap to a more resilient business. Every vulnerability is a chance for you to offer a solution, whether it's a new managed service or consulting hours. This process also helps meet compliance needs like SOC 2 and HIPAA, making your services essential.
Trust is everything in the MSP game. A manual pentesting report from a certified expert is tangible proof of the value you provide. It shows clients you are actively protecting their assets. This is a game-changer for GRC companies and CPAs who need to prove due diligence for PCI DSS or ISO 27001 requirements.
Partnering with a channel-only provider means you deliver expert-level pentesting without the huge cost of an in-house team. We provide affordable, fast, manual pentesting, and you remain the hero. You can dive deeper into these cyber security statistics to understand the full threat landscape.
For any reseller, scaling high-end services is a challenge. Building an in-house team of certified pentesters is expensive and time-consuming. Our OSCP, CEH, and CREST certified experts become an extension of your team, instantly boosting your capabilities. We built our model to solve the industry's biggest problems: inflated prices and long lead times.
Our channel-only model means we don't have the massive overhead of traditional firms, making manual pentesting genuinely affordable. We deliver reports fast, so you can provide solutions quickly. We will never sell directly to your clients. Our success is tied to yours. By partnering with us, you can offer a premium risk assessment and penetration testing service under your brand.
A network security audit is a powerful business tool that deepens client relationships and generates new revenue. Contact us today to learn how our white-labeled services can fuel your growth.
How Network Security Audits Make Compliance Painless
Compliance is a high-stakes game for your clients. A solid network security audit is the foundation for meeting tough standards like SOC 2, HIPAA, PCI DSS, and ISO 27001. These are mandatory hurdles businesses must clear to avoid huge fines or losing customer trust.
Failing an audit can damage a client's business. As their MSP or vCISO, you guide them through this process. A professional penetration testing report gives you the proof auditors demand, showing your client has done their due diligence to protect sensitive data.
An auditor wants to see engineering reports and stress tests. Our penetration testing report is hard evidence that security controls were tested against real-world attack methods. When an auditor for PCI DSS asks how your client validates firewall rules, you can hand them a report showing how our OSCP and CEH certified experts tried to break through.
Your job is to navigate clients through the compliance maze. We give you a white label pentesting report that is clean, professional, and easy for everyone to understand. Our audit report provides clear, third-party validation you can take to auditors, saving you and your client hours of work. Our fast, affordable process lets you bake manual pentesting into your services without hurting your margins.
Different compliance standards focus on different areas, but all require a thorough risk assessment. A network security audit addresses the technical controls that support nearly every major framework.
Audit Focus Areas for Key Compliance Standards
As you know a manual pentest engagement directly satisfies core requirements of all pentest requirements. While automated tests will only satisfy several. By partnering with us, you can confidently tell your clients you have a solution that meets their specific compliance needs. We're a channel-only partner, which means we never go after your clients. We're here to make you the hero.
Ready to simplify compliance for your clients? Contact us today to learn how our fast, affordable, and expert-led network security audit services can become a key part of your toolkit.
Choosing the Right White Label Pentesting Partner

Not every penetration testing provider understands the channel. Many have inflated prices, long lead times, and outdated testing methods. As an MSP or vCISO, you need a true partner who understands your business and respects your client relationships. The solution is a partner who is channel-only, built to be an affordable, fast, and effective extension of your team.
Look for a real commitment to manual pentesting. Automated scans barely scratch the surface. A proper network security audit needs the critical thinking of a human expert who can uncover major business risks. Check that the provider’s team holds top certifications like OSCP, CEH, and CREST. These prove the pentesters have the hands-on skills to simulate a real-world attack.
Your pentesting partner must be 100% committed to the channel. This means they will never compete with you for your clients. A true partner works behind the scenes to make you the hero. Their success is directly tied to yours. It’s a conflict-free model that protects your business. You can learn more about this approach in our guide on manual white-labeled pentesting.
The old way of doing things is broken. The pentesting industry has a serious problem with inflated prices and bad methodology. We are here to fix it. Your business moves fast, and your security partner must keep pace. A streamlined, channel-focused model cuts out massive overhead, passing those savings to you. This makes a high-quality network security audit genuinely affordable.
Fast turnarounds are critical. You need to deliver findings to your clients quickly to move from problem to solution. This agility is key for meeting compliance requirements for frameworks like SOC 2, HIPAA, and PCI DSS. This comprehensive global outlook report has more details on how AI is shaping cybersecurity.
Choosing the right partner changes your ability to deliver security services. By focusing on a channel-only provider with certified manual testers and a commitment to speed and affordability, you can expand your offerings and drive real growth. Contact us today to learn how we can be that partner for you.
Frequently Asked Questions About Network Security Audits
The term network security audit can bring up questions. As an MSP or vCISO, your clients look to you for clear answers. Here are the questions we hear most often from our partners, with straightforward answers.
How often should a network security audit be performed? The answer depends on the client. For most, a full penetration testing engagement once a year is a solid practice. But some situations require more frequent audits. Clients in high-compliance industries like PCI DSS may need quarterly or semi-annual tests. Any major network change, like a new app launch, also calls for a new audit.
What is the difference between a scan and an audit? This is a critical distinction. An automated vulnerability scan is like a spell-checker for your network. It’s fast and catches common, known issues, but it lacks context. A manual pentesting audit is like hiring a professional editor. Our OSCP and CEH certified pentesters dig into business logic, find clever ways around controls, and chain small issues together to create a massive risk.
How can manual pentesting be so affordable? There’s a myth that quality manual pentesting must be expensive. This comes from traditional firms with bloated overhead. We built our business to fix that for the channel. As a channel-only provider, we have zero direct sales costs. Those savings are passed directly to our reseller partners. Our efficient process delivers a top-tier network security audit at a price that makes sense.
What happens after the audit is finished? The audit is just the start. We deliver a comprehensive white label pentesting report you can brand as your own. It includes a high-level executive summary, detailed technical findings, and actionable remediation steps. You can use this report to build a project plan and guide your client toward a stronger security posture. We also offer re-testing to confirm vulnerabilities are patched, which is essential for compliance frameworks like SOC 2, HIPAA, and ISO 27001.
At MSP Pentesting, we empower our partners with fast, affordable, and expert-led security services. Let us be the silent partner that helps you grow. Contact us today to learn more.


.avif)
.png)
.png)
.png)

