Trying to explain the difference between a penetration test vs vulnerability assessment? It's simpler than it sounds.
Imagine you're securing a house. A vulnerability assessment is like walking around and checking if all your doors and windows are locked. It's a quick, automated scan for obvious weak spots.
A penetration test, however, is like hiring a professional to actually try and break into your house. They'll pick the locks, test the window frames, and see if they can get in through the garage. This test shows you exactly how a real burglar would succeed.

Understanding Key Differences in Security Testing
For any MSP or vCISO, explaining this difference to clients is crucial for managing their security and compliance goals. While both services look for weaknesses, their methods and goals are completely different. Your clients need to know that one service provides a list of potential problems, while the other proves which ones are real threats.
A vulnerability assessment is a broad, automated scan of a network. It uses tools to check systems against a huge list of known security flaws. The goal is to get a big-picture list of potential weaknesses, which is a great way to understand a company's basic security hygiene.
A manual penetration test goes much deeper. This is where one of our OSCP, CEH, or CREST certified pentesters gets involved. They don't just find vulnerabilities; they actively try to exploit them. They think creatively, like a real attacker, and can chain together minor issues to create a major breach. This hands-on approach is essential for meeting compliance standards like SOC 2, HIPAA, and PCI DSS. You can learn more in our guide on what is penetration testing.
Why Vulnerability Assessments Create a Security Baseline

A vulnerability assessment is the first step in any solid security program. It's like taking a wide-angle photo of your client's network to get a quick overview of potential weaknesses. The process is automated, using scanning tools to check systems against databases of known flaws.
These scans are fast and affordable, making them perfect for regular security check-ups. For any MSP or vCISO, offering vulnerability assessments is a great way to give clients a consistent security baseline. It’s a routine digital health screen that flags potential problems before they become emergencies.
The final report is a list of every potential issue the scanner found, usually ranked by severity. This helps you and your client prioritize fixes. The big catch is that an automated scan doesn't know if a vulnerability is actually exploitable in your client's specific environment. It might flag a vulnerability on a server that, because of a well-configured firewall, poses zero real risk. This is where a manual penetration test becomes necessary to confirm which risks are real.
How Manual Penetration Testing Uncovers Real Risks
Think of a vulnerability assessment as a map of potential roadblocks. A manual penetration test is where our experts see if those roadblocks can actually be bypassed. This is where human skill easily beats automated scanners.
Our certified ethical hackers simulate a real-world cyberattack. Armed with top certifications like OSCP, CEH, and CREST, they've been trained to think like an attacker. They use creativity and logic to not just find vulnerabilities but to actively exploit them.
A manual pentest shines by chaining vulnerabilities together. An automated scanner might report three separate low-risk issues that you'd ignore. A skilled pentester might see that exploiting those three minor issues in a specific order gives them administrator access to a critical server. This is the kind of insight an automated tool will always miss. We show you the actual business impact of a security gap, which helps you get client buy-in for necessary upgrades.
When your clients face a compliance audit, a vulnerability scan report isn't enough. Frameworks like SOC 2, HIPAA, and PCI DSS demand proof that you've actively tested your defenses. Our affordable, white label pentesting services deliver exactly that. As your channel-only partner, we give you the expert validation you need—quickly and affordably.
Choosing the Right Test for Client Needs
So, how do you help clients with the penetration test vs vulnerability assessment choice? Stop thinking of them as competitors. They are teammates in a solid security strategy. Your job as an MSP or vCISO is to know when to use each one.
A vulnerability assessment is for routine health checks. It’s fast, affordable, and provides a great baseline to show you’re maintaining good security hygiene.
A penetration test, on the other hand, is for big moments. It is essential for annual compliance needs like ISO 27001, SOC 2, or PCI DSS. Auditors want to see proof that you’ve tried to break in. You also need one before launching a new application or after major infrastructure changes. Our certified OSCP, CEH, and CREST pentesters provide the real-world risk assessment needed for these critical scenarios.
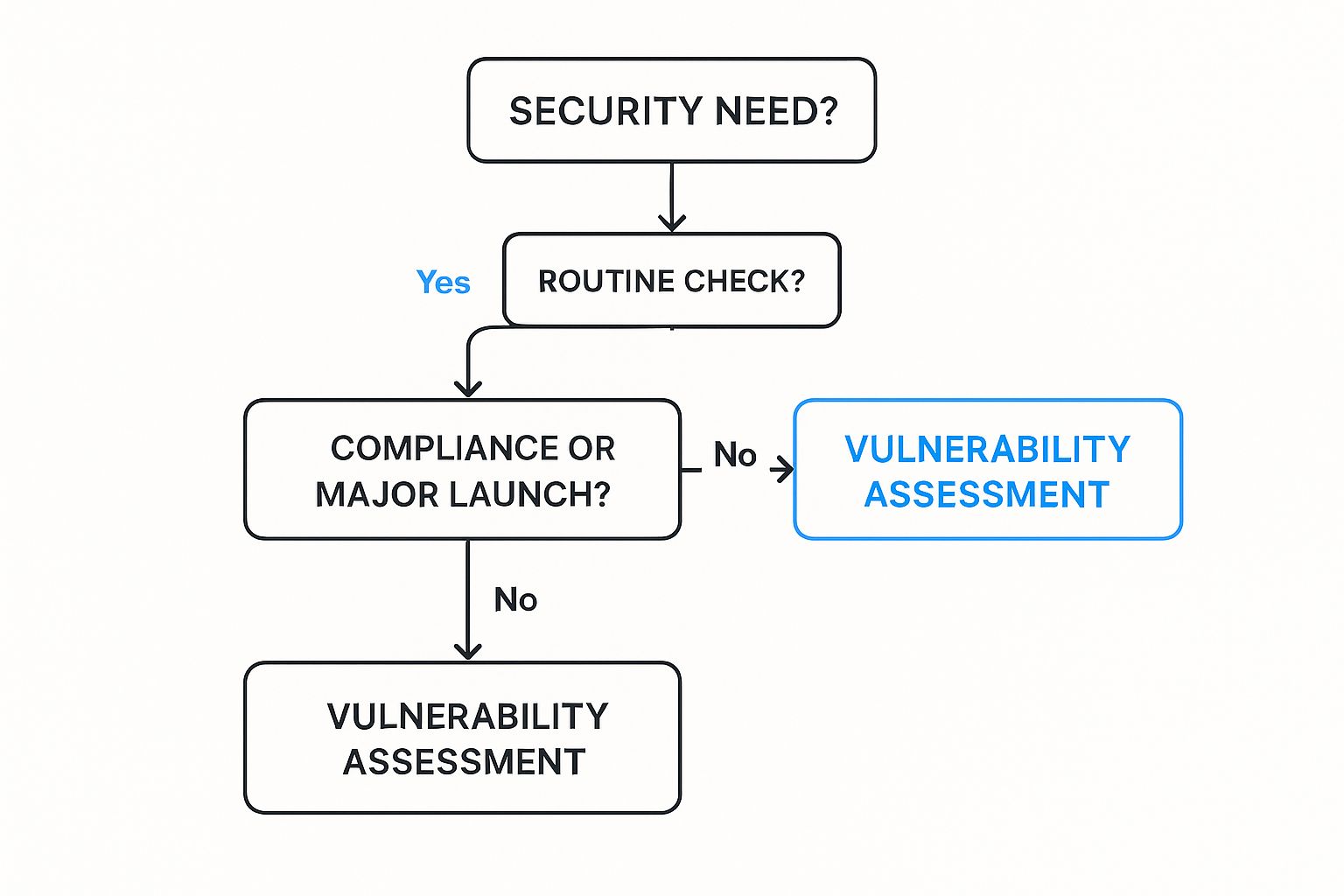
Knowing when to recommend each service makes you a more valuable partner. A vulnerability assessment is a proactive way to stay on top of security, while manual pentesting is a strategic investment to validate security controls and meet regulatory demands. We are the channel-only partner that empowers you to deliver both. Our fast, affordable, and white label pentesting services give you the tools to be the security expert your clients trust.
Comparing Security Testing Scopes and Methods

Let's discuss the "how" of a penetration test vs vulnerability assessment. A vulnerability assessment is like casting a wide, automated net. It’s fast, covers a huge area, and gives you a quick inventory of potential issues.
A penetration test is like sending a skilled diver to find a specific shipwreck. This is a manual, targeted, and deep approach. Our certified pentesters don't just run a tool—they are actively problem-solving and chaining together small weaknesses to achieve a goal, like accessing sensitive data.
An automated scanner is a machine following a script. It can’t think creatively or change its attack plan. It just checks what it sees against a database of known problems. Our manual pentesting process is driven by human intelligence. Our OSCP, CEH, and CREST certified experts have intuition that software can't match. This human element is why auditors for SOC 2 or PCI DSS demand a manual test—they need proof of a real-world attack simulation.
This table highlights why one test is for regular hygiene and the other is for deep security validation.
The methodology defines the value. As an MSP or vCISO, you need to provide that deeper, human-led validation. With our affordable, fast, and white label pentesting, you can give clients the proof they can't get from a simple scan.
Our Channel-Only Solution for MSPs and vCISOs
The security testing industry has a problem. Inflated prices, bad testing methodology, and long lead times make it hard for partners like you to succeed. Worse, some vendors compete with their own resellers. We are the solution.
We built our business to fix these problems. We offer affordable, transparent pricing created specifically for a reseller. There are no hidden fees, just a straightforward structure that lets you build a profitable security practice. We are a 100% channel-only company. We will never compete with our MSP or vCISO clients.
Waiting weeks for a penetration testing report is a deal-breaker when your client has a deadline for a SOC 2 or ISO 27001 audit. Our expert team of certified pentesters—holding credentials like OSCP, CEH, and CREST—delivers comprehensive manual pentesting reports quickly. Our reports are thorough, detailing exploited vulnerabilities and providing clear, actionable guidance. You can learn more about our secure testing services.
Our white label pentesting services are built to slide seamlessly into your offerings. You can put your own brand on our detailed reports, positioning yourself as the security authority. For GRC companies and CPAs, this allows you to confidently offer robust testing to support clients' compliance needs for frameworks like HIPAA and PCI DSS. We are the trusted, behind-the-scenes team dedicated to helping you grow your security practice.
Frequently Asked Questions from Our MSP Partners
We talk to MSPs and vCISOs every day. Here are answers to some of the most common questions we hear, designed to help you guide your clients.
How often should clients get a penetration test?
For most compliance frameworks like SOC 2 or PCI DSS, an annual penetration test is the standard. We also strongly recommend one after any major infrastructure or application changes. Vulnerability scans, however, should be run far more often, ideally monthly or quarterly.
Is a vulnerability scan enough for auditors?
Almost never. A vulnerability scan alone is not enough for major compliance standards like PCI DSS or ISO 27001. Auditors require a manual pentesting engagement to see proof that you’ve simulated a real-world attack. A scan gives you a list of potential problems, but a pentest delivers hard evidence of actual risk.
Why is your white label pentesting great for MSPs?
Our entire model was built for the channel. We are a silent extension of your team, providing a professionally formatted, white-labeled report you can put your own logo on. You get the expert manual pentesting your clients need for compliance, and our affordable pricing ensures you maintain healthy margins. It’s the simplest way to add a profitable security offering.
Ready to give your clients the affordable, expert validation they need? We are your silent, channel-only partner. Contact us today to learn more about our white-label pentesting services.


.avif)
.png)