A vendor security assessment questionnaire is basically a background check for any third-party company you want to work with. Before you connect their software to your client's network, you need to know if their security is any good. This questionnaire is how you find out and spot potential risks early.
As an MSP or vCISO, your clients rely on you to protect their data. Every new vendor adds a potential weak spot. Without a formal process to check them out, you're just hoping they take security as seriously as you do. A good questionnaire is your first line of defense.
Why Vendor Questionnaires Are So Important
Using a vendor security assessment questionnaire isn't just about checking a box for compliance. It’s a key part of a smart security strategy. It gives you a clear picture of a vendor’s security controls before they access your client’s systems, which is essential for any risk assessment.
This process is a must-have, not a nice-to-have. Many data breaches start with a compromised vendor. Flying blind is a huge gamble for your clients and your reputation. Making a detailed questionnaire a standard part of your onboarding process helps you achieve several important goals.
First, you set a clear security baseline for all partners. Second, you can spot red flags right away, like vague answers or a refusal to share information. Third, it provides an audit trail for frameworks like SOC 2, HIPAA, ISO 27001, and PCI DSS. Finally, it protects your reputation as a trusted security advisor.
This all fits into the broader strategy of Third-Party Risk Management (TPRM). A strong questionnaire gives you the power to make informed decisions and ensure you only partner with vendors committed to data protection. Our guide on the third-party risk management process explains how to build a complete strategy.
How To Build An Effective Questionnaire
A generic questionnaire won't cut it. To get a real sense of a vendor's security for a proper risk assessment, you need to ask smart, targeted questions. Building an effective vendor security assessment questionnaire means focusing on the areas that could actually expose your client's data.
This isn't just about compliance paperwork. It's about creating a tool that reveals a vendor's real approach to security. By focusing on the right categories, you can build a questionnaire that is both efficient and thorough, aligning with major frameworks like PCI DSS and ISO 27001. A strong questionnaire is broken down into logical sections covering their entire security program.
Questions For Information Security and Governance
This is where you start. You need to find out if security is part of the vendor’s culture or just something they talk about to make sales. The goal is to see proof of clear policies, defined roles, and a real strategy for managing risk. If their foundation is shaky, the rest doesn't matter.
Here are some questions that get straight to the point:
- Do you have a documented information security policy, and how often is it reviewed?
- Who is responsible for information security in your organization?
- Describe your security awareness training program for all employees.
If a vendor can't answer these basic questions, it's a huge red flag. It suggests a chaotic approach to security that you don't want anywhere near your client's data.
Evaluating Access Control and Identity Management
This section is all about who can access what data. Weak access controls are a common cause of data breaches, so you need to be thorough. You're looking for proof that the vendor enforces the principle of least privilege, meaning people only have access to the data they need to do their jobs.
Strong answers show a vendor is serious about preventing both external attacks and insider threats. Vague responses are a sign of poor controls, a major risk for any MSP or vCISO.
Key questions should include:
- What is your process for removing access for terminated employees?
- Is multi-factor authentication (MFA) required for all administrative accounts and remote access?
- How do you manage and log access to systems containing sensitive data?
Assessing Data Encryption and Protection Methods
Since data is the target, how a vendor encrypts it is critical. Your vendor security assessment questionnaire must verify that data is protected everywhere. This means encryption should be active when data is stored (at rest) and when it's being sent over a network (in transit).
A vendor that just says their data is "secure" without providing details is a problem. You need specifics, like AES-256 for data at rest and TLS 1.2+ for data in transit. These technical details are essential for meeting strict compliance frameworks like HIPAA and SOC 2.
Checking Vulnerability and Patch Management Processes
Every system has weaknesses. A mature vendor has a proactive process for finding and fixing them before an attacker can. This section is about understanding how quickly and effectively they handle vulnerabilities. A vendor that regularly hires a firm for penetration testing is a good sign.
It shows they’re actively looking for weaknesses instead of just waiting for an incident. As a channel-only partner, we help MSPs verify these claims. Our affordable, manual pentesting services, led by OSCP and CEH certified experts, provide the independent validation you need. To manage these questionnaires, this guide to finding the best form builder can help.
Reviewing Incident Response and Business Continuity
No one is 100% secure, so you need to know what a vendor will do when an incident occurs. An incident response plan is their roadmap for a breach. It should detail how they detect, contain, and recover from an attack, and how they will notify you.
Without a tested plan, a small issue can quickly escalate. This is a critical area of evaluation for any GRC company or security reseller. You need confidence that your vendor can manage a crisis and keep your client’s business running.
How To Score Responses and Prioritize Risk
Once the answers to your vendor security assessment questionnaire come back, the real work begins. You need a system to interpret the data and make smart, risk-based decisions. A simple scoring model helps you move beyond gut feelings and objectively measure the risk each vendor introduces.
This is about having a clear reason for your recommendations and protecting your clients. The flowchart below shows the three pillars of a strong security program: how they govern security, what controls are in place, and how they respond to incidents.
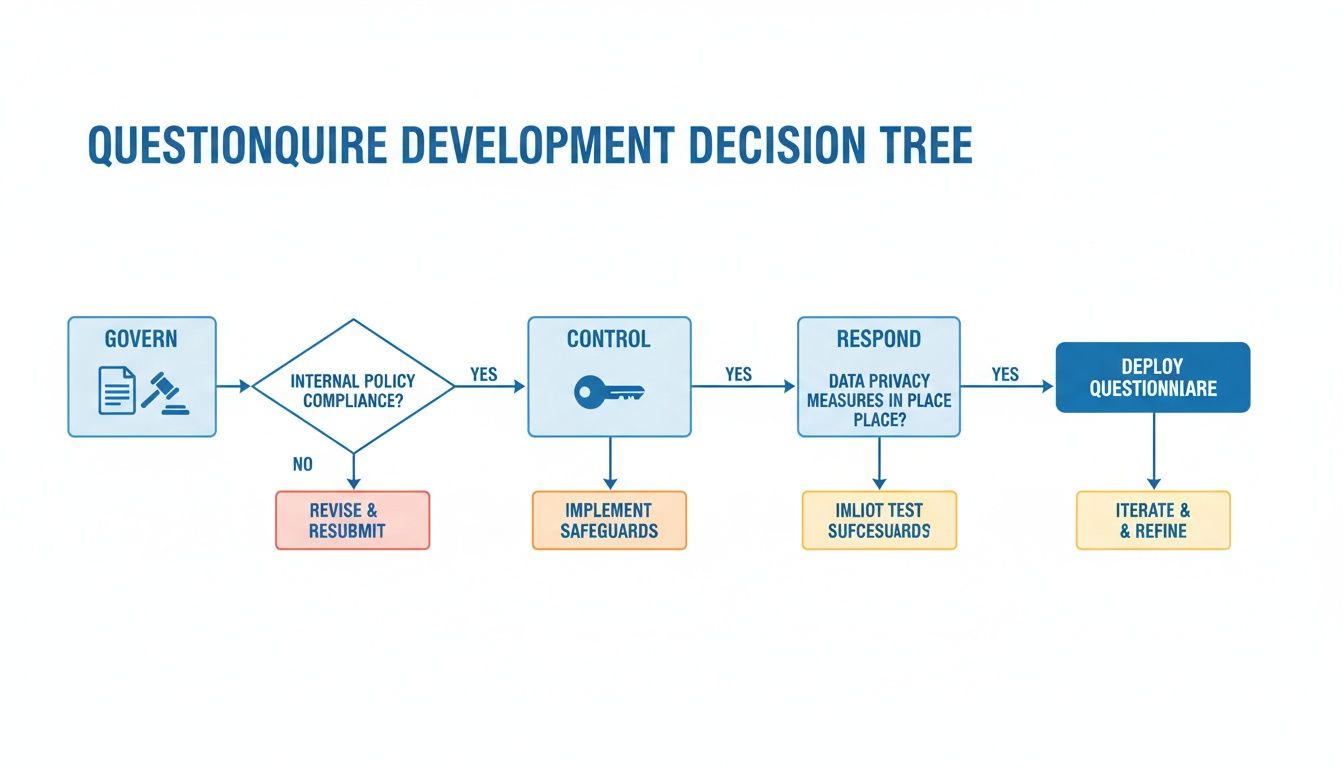
This model shows that a good security program starts with solid policies (Govern), is supported by technical safeguards (Control), and is prepared for an incident (Respond).
Creating a Weighted Security Scoring Model
Not all security controls have the same importance. A lack of multi-factor authentication is a much bigger deal than an outdated policy document. A weighted scoring model helps you prioritize by giving more significance to the controls that actually prevent breaches.
Assign a weight to each question based on how critical it is. For example, questions about incident response and data encryption should be weighted more heavily than those about employee training schedules.
A simple point system works well:
- High-Impact Controls (3x weight): Encryption, access control, and incident response.
- Medium-Impact Controls (2x weight): Vulnerability management and business continuity plans.
- Low-Impact Controls (1x weight): Security policies and physical security.
By weighting the scores, you get a final number that reflects the vendor's ability to protect data. This is the whole point of a good risk assessment.
How To Tier Vendors By Their Risk Level
After scoring each vendor, you can group them into risk tiers. This helps you decide where to focus your attention. A simple High, Medium, and Low system works for most MSPs and vCISOs.
High-Risk Vendors: These vendors handle your client's most sensitive data or are critical to their operations. They require a deep dive into their questionnaire responses, and you should ask to see their latest penetration testing report.
Medium-Risk Vendors: These partners might have access to less sensitive information. You still need to see a solid security posture, but the review can be less intense.
Low-Risk Vendors: These vendors have no access to sensitive data. A basic questionnaire is usually enough.
This tiering system allows you to concentrate on the high-risk vendors that pose the greatest threat. For more on this, see our guide on the cybersecurity risk assessment framework.
Spotting Common Security Red Flags Quickly
Sometimes, what a vendor doesn't say is more telling than what they do. As you review their vendor security assessment questionnaire, watch for classic red flags that indicate a weak security program.
Keep an eye out for these warning signs:
- Vague Answers: If a vendor gives a fluffy answer about their encryption standards, it's likely because they don't have one.
- No Incident Response Plan: A vendor without a documented, tested plan is a major risk.
- Lack of Certifications: A vendor handling sensitive data without a SOC 2 or ISO 27001 certification is a concern.
- Refusal to Provide Evidence: A vendor that won't share their latest pentesting report may have something to hide.
Catching these red flags early helps you avoid partnerships that could damage your client's business and your reputation.
Integrating Questionnaires Into Your Onboarding Process
A completed vendor security assessment questionnaire is only useful if you act on it. The real value comes when you make the assessment a required step in your vendor onboarding process. This makes security a foundational requirement, not an afterthought.
For MSPs and vCISOs, this is how you demonstrate due diligence and protect your clients from the start. The right timing is key. The best time to send the questionnaire is after you've shortlisted a vendor but before finalizing the contract. At this point, the vendor is motivated to provide complete answers.
Using The Assessment to Strengthen Contracts
The answers you receive can be used to strengthen your legal agreements. This turns their security promises into legally binding commitments. You can work their responses directly into the contract language.
For example:
- Breach Notification: If they claim a 24-hour notification policy, write that into the contract.
- Right to Audit: Add a clause giving you the right to audit their security or request evidence, like a penetration testing report.
- Specific Controls: If they say they use AES-256 encryption, make that a contractual requirement.
This is a crucial step for GRC and proving compliance for frameworks like SOC 2 and HIPAA.
Communicating Expectations and Handling Pushback
Be upfront with vendors. Let them know the security assessment is a standard part of your process. Position it as a mutual effort to build a secure partnership. Even with clear communication, you may face challenges. A 2021 IT compliance benchmark survey from Hyperproof found that many companies struggle to get complete risk information from their vendors.
If a vendor refuses to complete the questionnaire, it's a massive red flag. It usually signals a weak security program. While there might be a legitimate reason, a hard "no" often means you should walk away. Building the vendor security assessment questionnaire into your workflow creates a defensible, repeatable process that protects your clients.
Why Manual Vendor Assessments Don't Scale

Managing a vendor security assessment questionnaire on a spreadsheet is tough for one client. For dozens, it’s a recipe for burnout and overlooked risks. As an MSP or vCISO, manual processes limit your growth and tie up your team with administrative tasks.
To scale, you need to work smarter. Governance, Risk, and Compliance (GRC) platforms can automate the process, freeing you up to focus on making smart risk decisions. These tools handle sending questionnaires, tracking responses, and flagging high-risk answers automatically.
This efficiency is a huge advantage for any reseller. It allows you to offer more affordable and faster third-party risk management services. These platforms can also map vendor answers to multiple compliance frameworks like SOC 2, HIPAA, and ISO 27001, saving you time and ensuring consistency.
Sticking with manual processes is slow and expensive. Automation turns a costly task into a scalable, profitable service. Remember, these tools manage the workflow but don't replace the need for technical validation like security vulnerability scanning for critical vendors.
Answering Your Top Vendor Assessment Questions
As an MSP or vCISO, you need quick, clear answers about vendor risk. Here are the most common questions we hear about using a vendor security assessment questionnaire.
How Often Should We Re-Assess Our Vendors?
It depends on the risk level. High-risk vendors handling sensitive client data should be reviewed annually. For medium-risk vendors, every 18-24 months is a good benchmark. Low-risk partners can be assessed every two to three years. However, any significant event, like a data breach, should trigger an immediate re-assessment.
What Is The Difference Between A Questionnaire And A Pentest?
Think of it as "trust but verify." The vendor security assessment questionnaire is the "trust" part, where the vendor self-reports their security controls. A penetration test is the "verify" part. Our certified ethical hackers actively try to bypass their defenses to provide objective proof of their security. The questionnaire identifies high-risk vendors, and a pentest confirms if their claims are true.
What If A Vendor Refuses To Complete The Questionnaire?
A refusal is a major red flag. It often indicates a weak security program or a lack of transparency. You can try to understand their concerns and offer to sign an NDA, but if they still won't cooperate without a good reason, you have to decide if the business need outweighs the unknown risk. It rarely does.
Can We Use One Standard Template For All Vendors?
A one-size-fits-all approach isn't ideal. The questions for a payment processor should be more detailed than for a marketing tool. It's better to create a core set of questions for all vendors and then add modules for specific risks, such as HIPAA or PCI DSS compliance. This keeps the process efficient for low-risk vendors while ensuring you get the details you need from high-risk ones.
How Can We Verify A Vendor’s Pentest Report?
Receiving a penetration testing report is a good start, but you need to review it carefully. Check the date, scope, and the firm that conducted the test. As a channel-only partner, we help MSPs and vCISOs with this. If a report seems questionable, our team of OSCP, CEH, and CREST certified experts can perform an affordable, manual pentesting engagement to provide the independent, white-labeled validation you need.
At MSP Pentesting, we are a channel-only partner dedicated to helping MSPs and vCISOs build stronger supply chains. Our fast, affordable pentesting services provide the evidence you need to make smart vendor decisions.
Contact us today to see how our white label pentesting can strengthen your vendor risk program.



.avif)
.png)
.png)
.png)

