Assessing vendor risk is more than just sending out a questionnaire. It’s about finding, checking, and managing the real threats your suppliers pose to a client's data. To do it right, you need a modern plan that includes scoping, deciding what risks are okay, and getting real proof—like a manual penetration test.
This isn't just extra work; it's a key defense against supply chain attacks and a must-do for meeting compliance goals.
Why Your Clients Need a Modern Vendor Risk Plan
Your client’s security is only as strong as their weakest vendor. One hacked supplier can cause a huge data breach, costing your client a lot of money and ruining their reputation. For MSPs and vCISOs, having a solid plan to assess vendor risk isn't optional anymore. It's a core service clients expect.
Old-school checklists just don't work. The modern way is all about getting proof. You have to move past simply trusting what a vendor says about their security and start asking them to show you. This is super important for meeting compliance rules like SOC 2, HIPAA, PCI DSS, and ISO 27001, where you have to prove you did your homework.
Understand the Growing Threat of Vendor Breaches
The market for managing vendor risk is growing fast for a good reason. Supply chain attacks are a huge problem, and companies are realizing they need to get a handle on it. A shocking 98% of companies have had at least one security breach caused by a vendor.
This simple process flow breaks down the modern approach to vendor risk assessment into its core components.
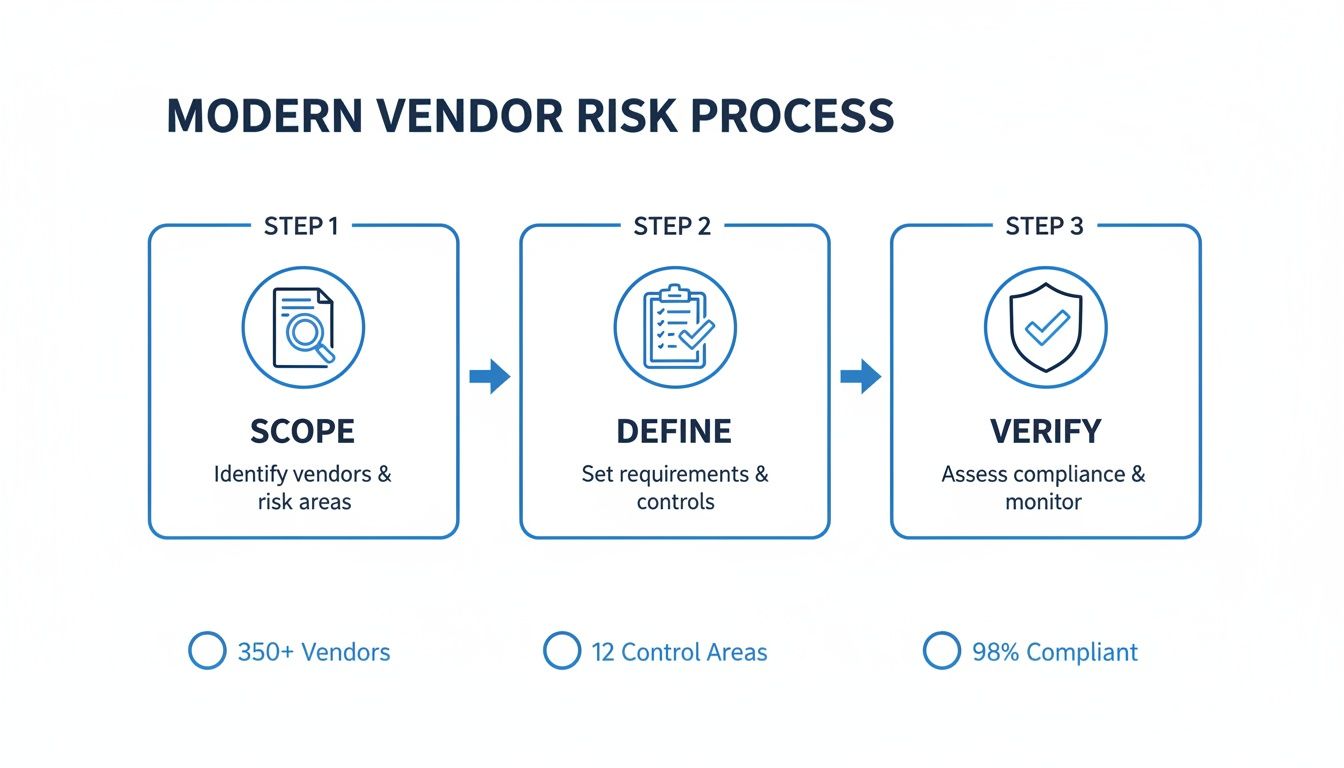
This Scope, Define, and Verify model makes sure your efforts are focused and actually work. It’s how you move from guessing to having real evidence about security. To give you a clearer picture, this table outlines the main parts of a strong vendor risk assessment program, which we'll break down in this guide.
.tbl-scroll{contain:inline-size;overflow-x:auto;-webkit-overflow-scrolling:touch}.tbl-scroll table{min-width:600px;width:100%;border-collapse:collapse;margin-bottom:20px}.tbl-scroll th{border:1px solid #ddd;padding:8px;text-align:left;background-color:#f2f2f2;white-space:nowrap}.tbl-scroll td{border:1px solid #ddd;padding:8px;text-align:left}Assessment PillarKey ObjectivePrimary Tool/MethodScopingIdentify all third-party vendors and categorize them based on data access.Vendor Inventory, Data Flow MappingRisk CriteriaDefine what "risk" means to your client and set acceptable thresholds.Risk Matrix, Inherent Risk ScoringEvidence CollectionGather security documentation and proof of controls from vendors.Security Questionnaires, SOC 2 ReportsTechnical ValidationVerify a vendor's security claims through hands-on testing.Penetration Testing, Vulnerability ScansRemediationTrack and manage identified risks to ensure they are addressed.Action Plans, Ticketing SystemsContractual ControlsEmbed security requirements directly into vendor agreements.Master Service Agreements (MSAs)Continuous MonitoringKeep an eye on vendor risk posture over time, not just at onboarding.Security Ratings, Annual Reviews
Each of these parts works together to build a strong defense. This ensures you're not just checking boxes but are actively making your client safer.
We Are Your Channel-Only Pentesting Partner
We know the problems you face. The compliance and managed service industry has inflated prices, bad testing methods, and long wait times. We started our company to fix that problem.
As a channel-only partner, we provide affordable, fast, and manual pentesting services that you can resell as your own. We never compete with you. We empower you—the MSP, vCISO, and GRC professional—with our expert pentesters who hold top certifications like OSCP, CEH, and CREST. You can deliver top-notch security validation under your own brand.
For a broader look at the vendor lifecycle, check out these Vendor Management Best Practices which cover selection, contracts, and risk mitigation. This guide will walk you through a practical plan to build out your vendor risk assessment program. You can also learn more about the third-party risk management process in our article.
How to Define Risk and Scope Your Assessments

Before you can assess vendor risk, you need a game plan. Sending a generic security questionnaire to every company your client works with is a huge waste of time. It won't give your clients the real protection they are paying you for.
The real first step is to figure out what "risk" means for each client. You need to be smart and focus your energy where it matters most. A good scoping process makes your job easier and gets better results for compliance frameworks like ISO 27001.
Think of your client's vendors like a pyramid. At the top are a few critical vendors, and at the bottom are many low-impact ones. Creating a simple tiering system is the fastest way to prioritize your work. Start by sorting vendors based on one question: What kind of data and systems do they access? This creates a logical framework for the whole risk assessment process.
- Tier 1 (High-Risk): These are the most important vendors. They have direct access to sensitive data (like customer or financial info) or are part of critical business operations. A breach here would be a disaster.
- Tier 2 (Medium-Risk): These vendors might handle some company data or support important but not critical functions. A breach would be bad, but it wouldn't shut down the business.
- Tier 3 (Low-Risk): These vendors have no access to sensitive data and provide non-essential services. Think of the office coffee supplier. A quick check is usually enough here.
This tiered approach stops you from wasting weeks investigating the coffee company while a critical payment vendor goes unchecked.
Set Clear Criteria to Assess Vendor Risk
Once your tiers are set, you need to define what you're looking for. What specific risks are you trying to stop? This means setting clear rules across a few key areas. For any MSP or vCISO, this is where you show your value. It proves to your client that you have a structured method, not just a gut feeling.
Here are the key areas to build your risk criteria around:
- Cybersecurity Posture: Does the vendor have the basics covered, like MFA and encryption? For Tier 1 vendors, you need proof, which is where penetration testing becomes a must-have.
- Compliance Obligations: Does the vendor need to follow regulations that affect your client, like HIPAA or PCI DSS? You must verify their certifications.
- Operational Resilience: What happens if this vendor has an outage? You need to check their business continuity and disaster recovery plans to make sure they won't bring your client's business to a halt.
Let’s use a real-world example. Imagine your client, an accounting firm, hires two new vendors. One is a payment processing platform (Tier 1), and the other is a social media tool (Tier 2). You would assess them differently.
For the payment processor, your risk assessment needs to be intense. You'll demand their PCI DSS compliance report and strongly recommend a white label pentesting engagement to prove their security. For the social media tool, a standard questionnaire is likely enough. This targeted approach saves time and money.
Gather Intelligence with Questionnaires and Evidence
Now it's time to start digging for information. This is where security questionnaires and evidence collection come in. A good questionnaire is your first look into a vendor's security, from their point of view. But the goal isn't just to get a form filled out.
Your questions should be tailored to the vendor's risk tier. A well-designed questionnaire feels more like a structured conversation. Ask questions that make vendors explain their processes, not just check "yes" or "no." This helps you spot issues and know where to look deeper.
For MSPs and vCISOs, building a library of question sets for different vendor tiers and compliance needs like HIPAA or PCI DSS is a huge time-saver. We have a helpful guide on building a great vendor security assessment questionnaire you can use.
A vendor’s answers are a good start, but they aren't proof. The next critical step is to collect hard evidence of their security controls. This is how you verify their claims and see their security program in action.
- For High-Risk Vendors (Tier 1): Ask for their latest SOC 2 report, ISO 27001 certification, and the summary from their most recent penetration testing report.
- For Medium-Risk Vendors (Tier 2): You can be more focused. A SOC 2 report is great, but their security policy and incident response plan also work.
- For Low-Risk Vendors (Tier 3): Keep it simple. Their standard security policy is often enough.
Getting the documents is only half the battle; you have to know how to read them. A SOC 2 report isn't just a pass/fail certificate. You need to read the auditor's opinion and look for any exceptions, which are red flags. The same goes for a pentest report. Look at the severity of the findings and, more importantly, check if the vendor fixed them. Regulatory pressure is mounting, so this level of detail is important. You can dig into more of these vendor risk management trends to see where the industry is heading.
Validate Security Controls with Manual Pentesting

Questionnaires and SOC 2 reports are a good start, but they only show what a vendor says they’re doing. To truly assess risk for your most critical suppliers, you have to verify their defenses. This is where technical validation, especially manual pentesting, becomes essential.
Think of it like this. An automated scan is like a security guard checking if doors are locked. A manual penetration test is an expert trying to pick those locks or find an unlocked window someone forgot about. Automated tools are fast, but they can't think like a real attacker. Our testers, with certifications like OSCP, CEH, and CREST, are trained to do just that.
That human element is critical for Tier 1 vendors. It’s the only way to find complex flaws that automated scanners miss. For a deeper look, check out our guide on the methodology for penetration testing.
An automated scan tells you if the front door is unlocked. A manual pentest tells you if the door frame can be kicked in. For your most critical vendors, you need the latter. You can also explore a comparison of different approaches, like Audityour.app vs. Manual Pentest.
As an MSP or vCISO, you can offer this high-value validation as part of your GRC services. We are a channel-only partner, so you provide this service under your own brand. We make it easy for you. We provide the affordable, fast, and deep technical expertise so you can deliver great insights to your clients. A pentest report isn't just a list of problems; it’s a roadmap for improvement. Your job as the reseller is to translate these technical findings into business risk for your client and drive action.
How to Score Risk and Prioritize Remediation
You have all this data from questionnaires, evidence, and technical tests. Now you need to turn it into a simple risk score. A good scoring system creates a repeatable process that turns a messy pile of findings into an actionable plan. For any MSP or vCISO, this is where you show your expertise in GRC.
You don't need a complicated algorithm. A simple model based on impact and likelihood works best. For each finding, ask two questions. First, what's the impact if this gets exploited? Give it a 1-5 score (low to critical). Second, what's the likelihood of this happening? A 1-5 score here helps you focus on probable threats.
Once you score individual findings, you can roll them up into an overall risk category for each vendor. This is what your clients pay you for. A simple traffic-light system works great:
- High (Red): These vendors have serious, urgent issues. Remediation is non-negotiable.
- Medium (Yellow): These vendors have weaknesses that need to be addressed, but it's not an emergency.
- Low (Green): These vendors meet your client’s security standards.
This simple system gives your client a clear view of their vendor landscape. You have a prioritized list. Instead of saying, "We found 50 problems," you can say, "We have three high-risk vendors to deal with now." This makes you a strategic advisor, not just a problem-finder.
Focus on the high-risk vendors first. Work with them to create a remediation plan with deadlines. This could mean requiring them to fix critical vulnerabilities found during a white label pentesting engagement. For any reseller offering vCISO services, this ongoing management shows continuous value and builds strong client relationships.
Build a Continuous Vendor Monitoring Strategy

A one-time check during vendor onboarding is not enough. You can't assess vendor risk once and forget about it. A vendor's security can change overnight. Vendor risk is a continuous part of your client's security program. This is where you, as an MSP or vCISO, become a long-term, trusted security partner.
Once you've identified risks, the real work starts. You need a solid process for tracking fixes and verifying they work. This is especially important for vulnerabilities found during a penetration testing engagement. A vendor might say a vulnerability is patched, but only a re-test can give you peace of mind. As an MSP acting as a reseller, offering this verification is a huge value-add.
Your biggest tool is often the contract. Including security requirements in your client's agreements holds vendors accountable from the start. One of the most powerful moves is to include a "right-to-audit" clause. This gives your client the contractual power to run their own security assessments, including a white label pentesting engagement. It's the ultimate 'trust but verify' tool.
Here are a few must-haves for any vendor contract:
- Security Standards: Mandate adherence to frameworks like ISO 27001 or controls for SOC 2.
- Breach Notification: Set a strict timeline for incident notification (e.g., within 24 hours).
- Data Handling: Clearly define how client data can be stored and processed.
- Right to Audit: This clause is your trump card for independent security tests.
The threat landscape is always changing, so schedule regular reviews. For high-risk vendors, do this annually. For lower-risk ones, every 18-24 months might be fine. These reviews are a chance to re-evaluate everything. You can send an updated questionnaire, ask for their latest SOC 2 report, and schedule a fresh manual pentesting engagement for critical vendors. This proactive cycle protects your client from security drift.
Your Top Vendor Risk Questions, Answered
When MSPs and vCISOs start building a vendor risk program, a few questions always come up. Here are the straightforward answers you need.
How Often Should We Assess Our Vendors?
It all comes down to risk. For your most critical, high-risk vendors, you should do a full risk assessment every year. For medium-risk vendors, every 18 to 24 months is a good balance. For low-risk vendors, you can check in on an as-needed basis.
What’s the Most Overlooked Part of Vendor Assessment?
Technical validation is by far the most overlooked part. Too many organizations stop after a questionnaire or a quick look at a SOC 2 report. But that’s just taking the vendor's word for it. The best security programs verify a vendor's claims with a manual penetration test. It’s the only way to know if their defenses can stop a real-world attacker.
Can We Actually Require Vendors to Get a Pentest?
Yes, you can, and for high-risk vendors, you should. This isn't just a suggestion; build the right to audit directly into your contracts. Make it a non-negotiable part of doing business. As a channel-only partner, we make this easy. We offer affordable, fast white label pentesting designed for MSPs. Our certified OSCP, CEH, and CREST experts handle the technical work, and you deliver the report under your brand.
Ready to prove your clients' vendors are secure with real, manual validation? MSP Pentesting delivers the affordable, expert penetration testing services you need to close security gaps and build trust.
Contact us today and see how our channel-only partnership can help you grow your business.



.avif)
.png)
.png)
.png)

