Security in layers, also known as defense-in-depth, is built on a simple idea: no single security tool is ever enough. Instead of trusting one magic bullet to protect a network, you build multiple, varied defenses. This forces an attacker to break through several independent controls to get anywhere.
It's the difference between a single deadbolt on the front door and a full security system with fences, cameras, motion sensors, and guards.
Your One-Tool Security Strategy Is Failing
If you’re still telling clients their firewall or next-gen antivirus is "good enough," you’re setting them up for a breach. The old "castle and moat" approach is dead.
Attackers aren’t just knocking at the front door anymore. They're finding unlocked windows, tunneling underground, and tricking the guards into letting them in. Relying on just one point of defense is a massive gamble, and your clients are the ones who pay the price when it fails.

This single-layer mindset is exactly what sophisticated threat actors hope to find. They know how to bypass one specific control. But forcing them to beat a firewall, then an endpoint detection solution, then application controls, and finally data encryption becomes exponentially harder. It creates friction, noise, and multiple opportunities for you to catch them in the act.
The Rise of Zero-Day Attacks
Modern threats are specifically designed to sidestep singular defenses. Look no further than the explosion of zero-day malware attacks to see why security in layers is non-negotiable. These attacks exploit unknown vulnerabilities, making traditional signature-based tools completely useless.
Zero-day exploits surged from just 28 in 2011 to 83 in 2021. By 2019, they were responsible for a staggering 80% of successful data breaches.
A layered security model isn't about making a network impenetrable. It's about making it so costly and difficult to breach that attackers give up and move on to an easier target.
For an MSP or vCISO, shifting to a defense-in-depth strategy is mission-critical. It’s the foundation of any real cyber resilience and a core requirement for compliance frameworks like SOC 2 and HIPAA.
Effective threat and vulnerability management requires understanding how these different layers work together. Validating those layers with services like manual pentesting moves your clients from assumed security to proven security. This isn’t just a best practice; it’s the only reliable way to protect client assets today.
Deconstructing a Modern Layered Security Stack
Theory is boring. Let’s think about security in layers like you’re protecting a high-value building. You wouldn't just install a heavy-duty front door and call it a day, right? Of course not. You’d have a perimeter fence, security guards roaming the halls, motion sensors inside, and a steel vault for the most critical assets.
Each layer has one job: slow down, trip up, and expose an intruder.
Your clients' security stack needs that exact same logic. The goal isn’t to make any single layer completely unbreakable. It’s to accept that one layer will eventually fail—and to make sure another one is already in place to catch the threat when it does. That’s the real secret to a resilient defense-in-depth strategy.
The Core Layers of Security
A modern security stack can be broken down into a few essential layers, each one tackling a different part of the attack surface. As an MSP or vCISO, walking clients through this framework is the best way to explain why you’re recommending more than just a basic firewall. It shows you have a real strategy.
This is how all the pieces, including network defense, fit together.
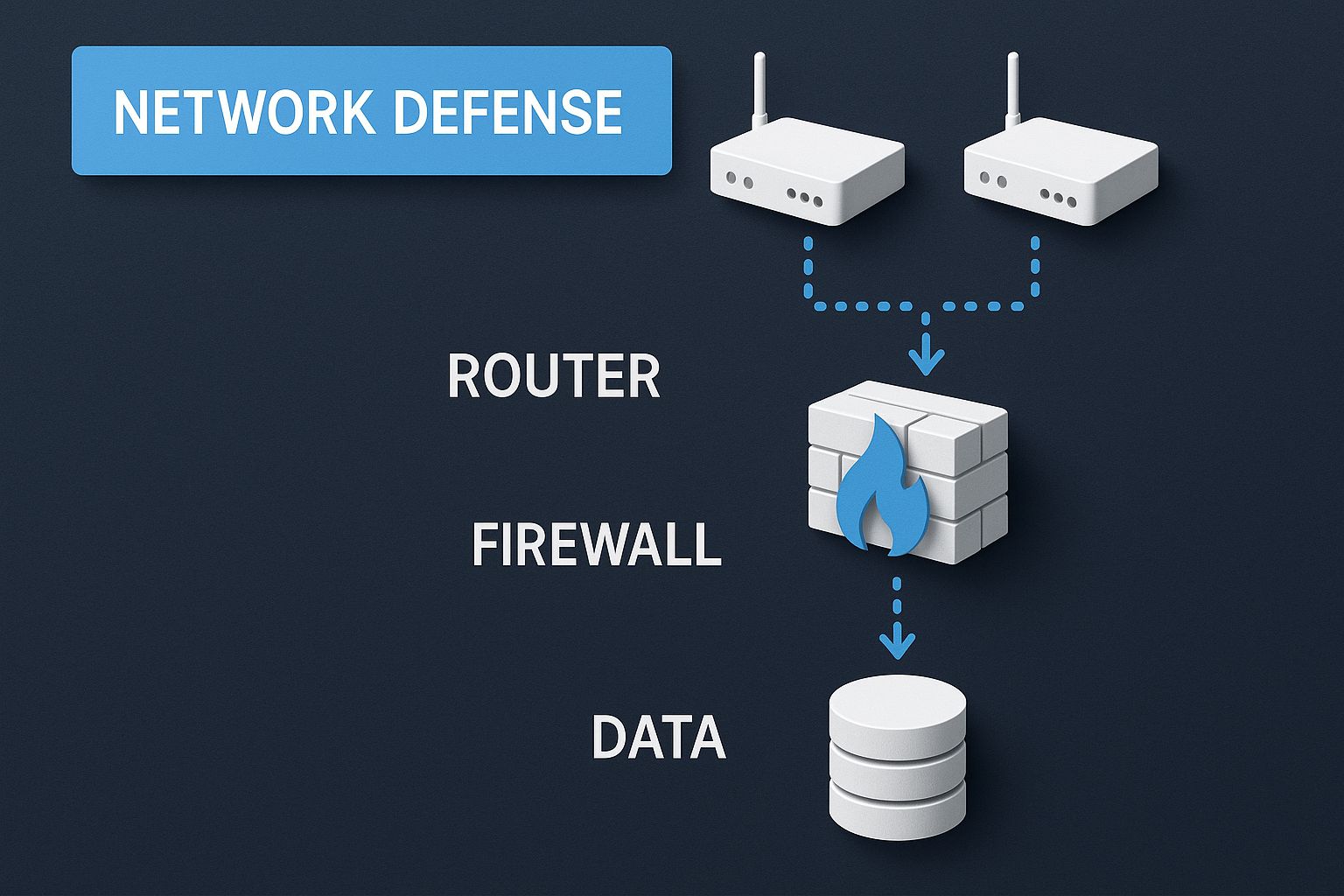
As you can see, things like firewalls and routers are just the foundational outer perimeter. True security goes much deeper.
Here are the key layers that form a comprehensive defense-in-depth strategy. Each one plays a unique role, and understanding how they work together is crucial for building a security offering that actually protects your clients.
By layering these technologies and practices, you create a security posture where a single failure doesn't lead to a total compromise. An attacker has to beat not just one control, but a whole series of them, which is a much taller order.
Why This Layered Approach Is Non-Negotiable
The final layers, Data and Human are arguably the most critical because they protect the ultimate targets. No security stack is truly complete if it ignores them. It’s this holistic thinking that explains why the global multi-layer security market, valued at $37.47 billion in 2022, is projected to rocket to $77.25 billion by 2032. You can learn more about what's driving this market growth and see for yourself.
Regular manual pentesting is absolutely crucial for the Application Layer, as it's the only way to find complex business logic flaws that automated scanners are blind to.
And for the Data Layer, technologies like encryption and Data Loss Prevention (DLP) are non-negotiable for anyone serious about compliance with frameworks like HIPAA or SOC 2.
Think of it this way: a layered defense creates a "hostile" environment for attackers. Every wrong move they make generates an alert, forces them to bypass another control, and dramatically increases their chances of getting caught.
For a reseller, this is your blueprint. Building a service offering around these distinct layers—and then validating their effectiveness with white label pentesting is how you graduate from being a simple IT provider to a genuine security partner. You’re no longer just selling a product; you’re delivering a strategy.
How Manual Pentesting Validates Your Security Layers
So, you’ve built your fortress. You’ve got a firewall, EDR, application controls, and maybe even a SOC keeping an eye on things. On paper, your security in layers looks solid. But how do you really know if it all works together?
Theory is one thing; reality is another. An automated vulnerability scanner is a decent start, but it's only checking for known, documented flaws. It can't think on its feet, get creative, or chain a few low-risk findings together to create a critical breach.
This is where you separate the pros from the amateurs. Manual pentesting is the ultimate stress test for any defense-in-depth strategy. It’s not about checking boxes on a list—it's about unleashing a real, determined human attacker to see how well your defenses hold up under pressure.

Beyond Automated Scans
Automated tools are predictable. They follow a script, search for specific signatures, and spit out a report. They're great for baseline checks and hitting basic compliance requirements, but they have massive blind spots.
A human pentester, on the other hand, thinks outside the box. They don't just ask, "Is this port open?" They ask questions that lead to real-world breaches:
- Can I bypass the firewall by exploiting a trusted application?
- If I manage to compromise this one user account, where can I pivot from there?
- Does the EDR solution actually pick up on the custom malware I just wrote?
- How do these different security layers react when they're hit simultaneously?
This is the only way to test the connections between your layers. An automated scan might see a locked door, but a manual pentest will check if the window right next to it was left wide open.
For an MSP or vCISO, a manual pentest report is more than just a list of vulnerabilities. It’s hard proof that your security stack is a cohesive, battle-tested system—not just a random collection of expensive tools.
Demonstrating Real Security Value
When you hand a white label pentesting report to a client, you're not just pointing out problems. You're demonstrating your value as their security partner and proving that you are actively validating the very defenses you built for them.
This process is absolutely critical for any organization serious about security, especially those navigating frameworks like SOC 2 or HIPAA. Auditors want to see evidence of due diligence, and a thorough manual pentest is the gold standard.
Our take on manual pentesting is built from the ground up for the channel. We provide affordable, fast, and deep-dive testing that gives you the insights needed to actually harden your clients' defenses. We’re the partner that helps you prove your security strategy works when it matters most.
To see how we can help you validate your clients' defenses, check out the details on our manual, white-labeled pentesting services. This is how you move from simply managing IT to delivering real, measurable security outcomes. Don't just build layers; prove they can withstand an attack.
Mapping Layered Security to Compliance Frameworks
If your clients operate in regulated industries, compliance isn't just a good idea—it's the price of admission. All too often, MSPs and their clients treat frameworks like SOC 2 or HIPAA as a painful checklist to just get through. It's a reactive, box-ticking exercise that misses the entire point.
But a security in layers approach completely flips that script.
It gives you a logical, structured foundation that maps directly to the core requirements of major compliance frameworks. Instead of scrambling to find evidence for an audit, you build a resilient defense where each layer already satisfies specific controls.
An auditor doesn't just want to see that you bought a firewall. They want proof of a coherent, well-thought-out security program.
From Checklist to Strategy
Put yourself in an auditor's shoes. When they ask how you protect sensitive data (HIPAA) or ensure operational integrity (SOC 2), a layered security model is the clearest, most compelling answer you can give.
- Network Security Layer: This directly addresses controls for access management, perimeter defense, and filtering network traffic.
- Endpoint Security Layer: This handles requirements for malware protection, device management, and threat detection on user machines.
- Data Security Layer: This maps straight to controls for encryption, data loss prevention (DLP), and safeguarding sensitive information at rest and in transit.
This structure transforms your security posture from a random collection of tools into a cohesive system. It proves you've done your due diligence and built your defenses with intent—which is exactly what auditors and regulators want to see. For a deeper dive, our guide on cybersecurity for MSPs breaks down how to build these essential offerings.
The real power of a layered defense is that it provides a narrative. You can walk an auditor through your entire stack, from the perimeter to the data itself, showing how each control builds upon the last to create a strong, defensible posture.
Validating Your Compliance with Manual Pentesting
Look, having the layers in place is a great start, but it's not enough. You have to prove they actually work under pressure.
This is where a manual pentesting report becomes your ace in the hole during an audit. It’s the independent, third-party validation that shows your controls aren't just present—they're effective against a real-world attacker.
This kind of proactive validation is quickly becoming a global standard. The Global Cybersecurity Index notes that 177 countries now have data protection laws on the books, all built on layered legal and technical controls. This worldwide push for resilience shows just how important it is to prove your defenses are solid.
For any reseller, offering white label pentesting is the final piece of the puzzle. It gives your clients a way to meet their compliance obligations while demonstrating the real-world value of the security stack you meticulously built for them.
It’s the ultimate proof that your layered strategy is working as intended, turning a security investment into a verifiable business advantage.
The Channel Advantage: Building a Scalable Security Offering
You’re an MSP or a vCISO, and you know the old vendor model is broken. You’re sick of getting inflated quotes for cookie-cutter tests, waiting weeks for a simple report, and then watching vendors who call themselves "partners" turn around and try to poach your clients.
It's a frustrating cycle, and it’s why we built our business from the ground up to be different.
We are a channel-only partner. That means we never sell directly to your clients. Period. We exist to make you look like the hero, arm you with a high-margin validation service, and help you scale your security offerings without all the usual headaches. Our services include manual pentesting, AI pentesting, and social engineering.
Building a Better Security Business
Partnering with a dedicated channel provider gives you an immediate, tangible edge. You're not just reselling another service; you're weaving a critical validation component directly into your layered security stack. This isn't about adding another line item to an invoice. It's about delivering a security program that's more complete, more effective, and—frankly—more profitable.
Here’s our solution to the industry's biggest problems:
- Affordable, High-Margin Services: Our manual pentesting is priced specifically for the channel. This lets you build a healthy margin while still delivering incredible value to your clients.
- Fast Turnaround Times: Forget waiting a month (or more) for a report. We deliver high-quality, actionable reports quickly, so you can help your clients fix vulnerabilities and prove compliance without missing a beat.
- 100% White Label Reports: Our reports become your reports. They carry your brand and your messaging, cementing your role as the trusted security advisor.
This whole model is designed to remove friction, not create it. When you work with us, you aren't dealing with a sales team that sees your client as its next lead. You're working with a team that sees you as the client.
Your success is our business model. By providing affordable, expert white label pentesting, we give you the tools to validate your client's security in layers and deepen your relationship as their strategic partner.
Scalable Security You Can Trust
For any reseller, scalability is the name of the game. You need processes that are repeatable, profitable, and don't force you to build an entire pentesting division from scratch. We provide that seamless back-end engine for you.
Whether you're helping a small business get ready for its first SOC 2 audit or managing the complex security needs of a healthcare provider under HIPAA, our services plug right into your existing workflow. Our team acts as an extension of yours, delivering the deep-dive technical validation needed to prove your security strategies are actually working.
Stop fighting with vendors who don’t have your back. It’s time to partner with a team that’s 100% invested in the channel. Contact us today to learn how our affordable manual pentesting can help you build a more profitable and effective security offering.
Your Questions About Layered Security, Answered
Once you start building a defense-in-depth strategy, a few practical questions always pop up. We hear these all the time from our MSP and vCISO partners as they work to implement and prove their security layers are actually working.
Here are the straight answers.
How Often Should We Pentest Our Layered Security Controls?
The industry baseline is to get a manual pentesting engagement done at least once a year. That’s the bare minimum.
You also need to pull the trigger on a new test anytime there’s a major shift in your client's environment. Think about things like a migration to the cloud, rolling out a new web app, or redesigning the network architecture. Any big change is a reason to test.
And if your clients have to meet compliance standards like SOC 2 or HIPAA, an annual pentest is usually non-negotiable. It's the only real way to know if your defenses can stand up to the new tricks attackers are using every day.
Can Automated Scanners Replace Manual Pentesting For Validating Layers?
Nope. Not even close.
Automated scanners are great for one specific job: finding the low-hanging fruit and known vulnerabilities. They’re a necessary part of a security program, but they absolutely cannot replace the brain of a human attacker.
A real manual pentesting expert brings creativity and persistence to the table. They think like an actual adversary, testing how your different security layers hold up when faced with a coordinated, multi-stage attack. An automated tool just can't do that. They’re two different tools for two different jobs—you need both.
The biggest mistake is the 'set it and forget it' mentality. Building the layers is just the first step. The real work is in ongoing monitoring, maintenance, and validation.
What Is The Biggest Mistake MSPs Make With Layered Security?
The most dangerous thing you can do is assume you're finished once the layers are in place. Security isn’t a project with an end date; it’s a constant process. Those layers need to be monitored, tweaked, and—most importantly—tested.
Without independent validation from a service like manual pentesting, you're just hoping your controls work. That’s a massive gamble with your business and your clients' data. Real security is built on proof, not assumptions. As a reseller, delivering that proof with white label pentesting is how you give your clients actual peace of mind.
Ready to validate your clients' security layers with a partner who has your back? MSP Pentesting offers fast, affordable, and 100% channel-only manual pentesting designed to help you build a more profitable and effective security offering.
Contact us today to learn more.


.avif)
.png)
.png)
.png)

