Security awareness training isn't just another box to check for compliance. It's about flipping the script on how your clients handle cybersecurity—turning their people from the weakest link into their strongest defense.
It’s the process of arming every employee with the knowledge to spot and stop cyber threats before they wreck the business.
Why Security Awareness Training is a Must-Have
As an MSP or vCISO, you can stack your client's defenses with the best firewalls and endpoint protection money can buy. But one employee clicking one bad link can make that entire tech stack worthless.
Attackers know this. It’s way easier to trick a person than to break through hardened tech. That human element is the real front door, and it’s usually wide open.
This is where security awareness training comes in. This isn’t about those boring annual videos everyone skips through. Effective training is an ongoing defense strategy that builds a real security-first culture.
Turning Employees from Targets into Defenders
The goal here is simple: build a human firewall. You want to turn employees from potential targets into defenders who can spot and report threats before they become incidents.
A good program doesn't just say, "Don't click that." It explains why. It breaks down the psychology behind social engineering attacks and shows people what a sophisticated phishing attempt looks like in the wild. That context is what makes the lesson stick.
Security awareness training reframes the entire conversation from "Don't be a liability" to "You are our first line of defense." It gives employees the confidence to question that weird email from the "CEO" and a clear path to report it.
This isn't just a "nice-to-have." With cybercrime costs projected to hit $10.5 trillion by 2025 and a massive 82% of data breaches involving a human element, you can't afford to ignore it. The market gets it, too—spending on security awareness training is set to hit $2.73 billion by 2033.
What Effective Security Awareness Training Covers
A solid program is a mix of different educational and testing components. Here are the core pillars that make it work.
These elements work together to create a defense that covers the most common ways attackers get in.
The Massive Opportunity for MSPs and vCISOs
For a reseller, this is a huge opportunity. You’re no longer just the "IT guy"—you're a strategic security partner. By offering a solid security awareness program, you deliver real value that plugs your client's single biggest security hole.
It's a natural add-on to your stack, especially when you're already providing services like pentesting. Plus, it helps clients meet compliance requirements for frameworks like SOC 2 and HIPAA, making it an easy upsell.
This shows you understand the entire threat landscape—not just the tech, but the people, too. By adding training, you can stand out from other MSPs, build stickier client relationships, and address the human factor that your other threat and vulnerability management services can't cover.
Key Elements of a Training Program That Actually Works
Once-a-year training video isn't cutting it. Employees just click through to get it over with, and nothing changes. A security awareness program that gets results isn't a single event, it's an ongoing process that builds a real security-first mindset.
If you're an MSP or vCISO, knowing these components is key to building (or reselling) a service that works, instead of just checking a compliance box. A program that moves the needle is all about practical, engaging, and continuous reinforcement. It’s less about memorizing rules and more about building reflexes.
Realistic Phishing Simulations
The cornerstone of any modern security awareness program is the phishing simulation. This is where you stop talking and start doing. These aren't generic spam emails, but controlled, realistic attacks designed to look exactly like the threats your clients' employees face daily.
The goal isn't to trick or shame people. It's to give them a safe place to fail without real-world consequences. When an employee clicks a simulated phishing link, it becomes a powerful teaching moment. They get instant feedback explaining the red flags they missed, which sticks with them far better than any slideshow.
For a reseller, this is gold. You get clear metrics to show real progress. You can track click-rates over time and show your client's leadership a tangible reduction in their risk.
Training Beyond the Inbox
Phishing is the number one attack vector, but a solid program can't stop there. It has to cover the whole spectrum of social engineering tactics attackers use.
This means training on:
- Vishing (Voice Phishing): Teaching employees how to handle suspicious phone calls from attackers pretending to be IT support, a bank, or even the CEO.
- Smishing (SMS Phishing): Showing them how to recognize malicious text messages that try to get them to click sketchy links or give up info.
- Physical Security: Reinforcing simple but critical habits, like not holding doors for strangers (tailgating) and properly shredding sensitive documents.
These pieces ensure the "human firewall" is ready for anything, no matter how the attack comes. This is especially important for organizations chasing SOC 2 or HIPAA compliance, which demand comprehensive security controls.
A program that only focuses on email is leaving the side doors wide open. Attackers will use any channel they can, and your training needs to reflect that reality.
Reinforcing Policy and Procedure
Training works best when it's tied to clear company policies. It’s not enough to tell people what to do; you need documented procedures that back it up and make secure behavior the easy choice.
This part of the program is all about consistently reinforcing those critical internal rules.
Key areas include:
- Secure Password Policies: Going beyond simple complexity rules to teach the importance of using password managers and enabling multi-factor authentication (MFA) everywhere possible.
- Data Handling Procedures: Clearly defining how employees should manage, store, and send sensitive client or company data to stop accidental leaks.
- Incident Reporting: Creating a simple, blame-free process for employees to immediately report anything suspicious. The faster a potential incident gets reported, the better the outcome.
When you pair our white label pentesting with this kind of training, you create a powerful one-two punch. Our manual pentesting can find a technical vulnerability, while your training program fixes the human behaviors that could have let an attacker exploit it. This positions you as the complete security partner your clients need.
Pairing Training with Pentesting for a Full Security Picture
Security awareness training and manual pentesting are two sides of the same coin. They have to work together.
Think of it like this: a pentesting engagement is a physical exam. It gives you a clear snapshot of your client's technical health, finding every crack and vulnerability in their network and apps. But what happens when that exam reveals the problem isn't a technical glitch, but a human one?
That's where training steps in. Our manual pentesting report might show a perfectly configured firewall, but our social engineering test could prove that employees are still willingly handing over credentials. Training is the direct fix for that human-layer risk.

Why One Without the Other is a Fail
Relying only on pentesting is like getting a health diagnosis with no follow-up treatment. You know what’s wrong, but you aren’t fixing the root cause. A pentest report highlighting a high click-rate on a phishing simulation is just a data point until you use it to implement training.
On the flip side, running a training program without real-world testing is like training for a marathon without ever running a single practice race. You have no baseline. No way to measure if your efforts are making a difference.
The two services feed each other in a powerful loop:
- Pentesting identifies the human risk: Our social engineering tests provide hard evidence of where employees are vulnerable.
- Training remediates that risk: You use those findings to sell and implement a targeted training program.
- Ongoing testing validates the training: Future tests show a lower click-rate, proving the ROI of your program.
Meeting Compliance Demands Head-On
For your clients in regulated industries, this combination isn't just a good idea—it's often a requirement. Major compliance frameworks demand a multi-layered approach to security that addresses both technical vulnerabilities and human behavior.
Offering both pentesting and training moves you from being a simple IT provider to a strategic security advisor. You're not just finding problems; you're delivering the complete solution that helps clients achieve and maintain compliance.
Frameworks like SOC 2 and HIPAA have specific controls that mandate security training and risk assessments. For instance, SOC 2's Common Criteria (CC) sections hammer on the need for organizations to communicate security roles and responsibilities. Training is the main way to get that done.
By offering a formal training program alongside a pentest, you give your clients exactly what auditors are looking for: a documented process for identifying, assessing, and mitigating risk. This makes training an easy and necessary upsell for any client facing a compliance audit.
A Powerful Reseller Strategy
As an MSP or vCISO, this integrated approach is your key to unlocking more value. We’re a channel-only partner. We provide the white label pentesting so you can own the client relationship. You use our unbranded, affordable manual pentesting report as the perfect sales tool.
Show the client the hard data: "Our testing found that 30% of your employees were susceptible to this specific phishing attack." Then, you present the solution—your branded security awareness training service. This creates a natural, value-driven sales cycle.
This model ensures we never compete with you, our reseller partners. You get the expert, fast testing you need to open the door, and you keep the profitable, recurring revenue from the ongoing training services. If you want to dive deeper, you can explore our approach to effective social engineering engagements.
Human error is still a massive factor in breaches, and consistent training is the best way to fight it. A report covering over 4,200 organizations found that companies with solid training programs see huge improvements in employee behavior. Regular training on threats like phishing and malware lowers risk scores and boosts compliance.
Building the Business Case for Security Awareness Training
Selling security awareness training shouldn't be a hard conversation. It’s a high-margin, recurring revenue service for you and a high-return investment for your clients. You just need the right talking points to connect a small monthly spend to avoiding a business-ending breach.
The conversation starts when you stop talking about abstract threats and start talking about business outcomes. Clients get dollars and cents. When you show them how training directly protects their bottom line, it becomes a no-brainer. This isn't a cost center; it's a critical investment.
Showing Clear ROI from Proactive Training
The core of your pitch is simple: risk vs. reward. The cost of a solid training program is a drop in the bucket compared to the fallout from a single successful phishing attack. You just have to help your clients see the obvious return on investment.
It’s not just about stopping a breach. Building a more security-conscious team has direct financial benefits. Recent data shows organizations with formal training programs reported 218% higher revenue per employee compared to those without. When people are more aware, they make smarter, faster decisions, which impacts performance.
The numbers don't lie. Consistent training makes a measurable difference in what your employees click on and report.
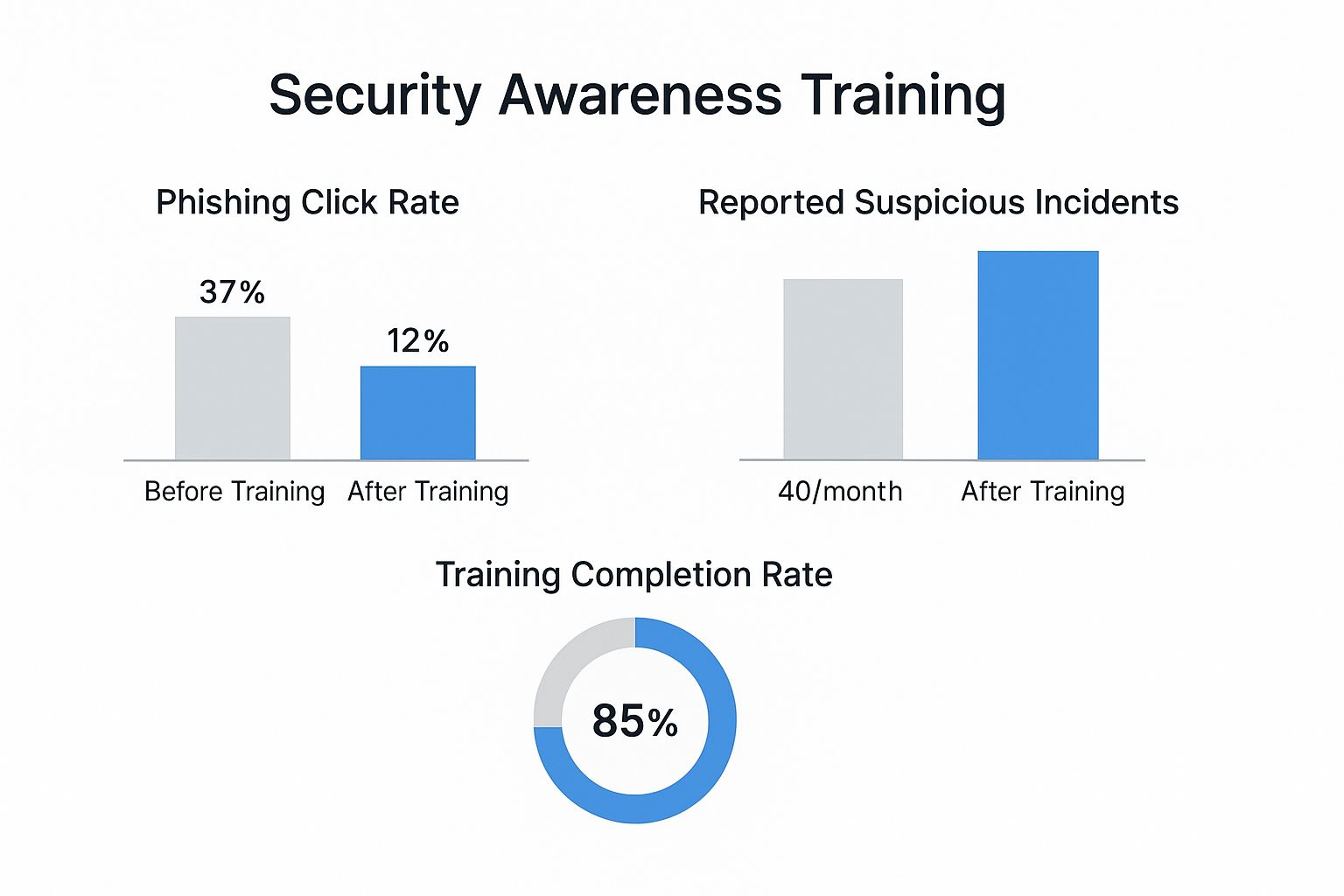
The data here is crystal clear. Training drastically cuts down on risky clicks and encourages employees to report suspicious emails. They become your first line of defense instead of your biggest liability.
The math is simple. A small, predictable investment in training is infinitely better than the unpredictable and catastrophic cost of a breach.
ROI of Security Awareness Training vs Cost of a Breach
FactorSecurity Awareness Training (Investment)Data Breach (Cost)Financial OutlayPredictable, low monthly/annual feeUnpredictable, often $1M+ for SMBsOperational ImpactMinimal disruption, enhances productivityMassive downtime, lost revenue, recovery costsReputationStrengthens brand trust and client confidenceSevere damage to brand and customer loyaltyInsuranceCan help lower cyber insurance premiumsSkyrocketing premiums, potential for denied claimsComplianceHelps meet regulatory requirements (HIPAA, etc.)Fines, penalties, and legal fees
Proactive training is an investment in stability and growth, while a breach is a direct hit to the company's survival.
Talking Points That Hit Home
When you sit down with a client, forget the technical jargon. Lead with the outcomes they care about.
Here are the key benefits to hammer home:
- Reduced Breach Likelihood: This is the big one. An employee who can spot and report a phishing attempt is your best defense against ransomware.
- Minimized Operational Downtime: A breach isn't a data problem; it's a productivity killer. Training keeps the business running.
- Brand and Reputation Protection: A public breach can destroy years of customer trust. Training is brand insurance.
- Lower Cyber Insurance Premiums: Insurers are getting tough. A formal training program is a huge plus that leads to better rates.
Position security awareness training as a strategic necessity. It's the seatbelt for their business, an affordable, non-negotiable measure you hope you never need, but know will save you if you do.
Connecting Training to Your Other Services
For any MSP or vCISO, security awareness training is the perfect add-on to your existing services, especially manual pentesting. When our white label pentesting report shows that their employees are falling for social engineering attacks, you have the perfect opening.
You can slide our unbranded report across the table and say, "We found this vulnerability, and here's the service that fixes it."
This makes you the hero who not only finds the problem but also delivers the solution. It's a natural upsell that makes you their indispensable security partner. All of this is supported by our affordable, channel-only model that helps you grow without ever competing for your clients.
How to Integrate Training into Your Service Stack
This is where our channel-only model gives you a massive advantage. We've created a simple workflow for MSPs and vCISOs to pair security awareness training with our white label pentesting services. The goal isn't just to add another line item, it's to build a powerful sales cycle that feeds itself.
You bring us in to find the real-world risks, and then you step in to deliver the exact solution your client needs. It’s a process designed to make you the hero.

The Find and Fix Workflow
This isn't theory; it's a practical, repeatable sales motion. We find the vulnerabilities, you provide the fix.
Here’s the breakdown:
- We Find the Human Risk: You bring us in for an affordable manual pentesting engagement that includes a social engineering component. Our certified team runs realistic phishing simulations to get a hard baseline on how employees react.
- You Present the Evidence: We give you a completely unbranded, white-labeled report. You walk into the client meeting, slide that report across the table, and show them the data: "Our testing found that 35% of your team is susceptible to this type of attack."
- You Sell the Solution: Now that the problem is crystal clear and backed by data, you introduce the solution: your branded security awareness training service. It’s the logical next step, directly addressing the vulnerability we just proved exists.
This completely changes the sales conversation. You're no longer guessing about risk. You're presenting cold, hard facts from a third-party expert, which makes the upsell feel less like a pitch and more like a necessary prescription.
Why Our Channel-Only Model Works for You
Our entire business is built on one promise: we never compete with our reseller partners. We’re here to make you look good and grow your business. You’ll never see our name on a report or find our team trying to sell services directly to your clients.
We provide the expert, behind-the-scenes firepower so you can own the client relationship and the profitable, ongoing remediation services. You get the evidence you need from our fast, affordable pentesting, and you keep all the recurring revenue from the training.
This model empowers you. We handle the specialized, time-consuming work of manual pentesting, and you focus on what you do best—managing the client relationship and building out your managed security offerings.
Building a Stronger Security Offering
Integrating training this way does more than just add a new revenue stream. It cements your position as a strategic security advisor. Clients need partners who see the whole picture, from technical flaws to human behavior.
This integrated approach is also a game-changer for clients dealing with compliance frameworks like SOC 2 or HIPAA. An auditor wants to see that an organization not only identifies risks (through pentesting) but also actively works to fix them (through training). By offering both, you deliver a complete, audit-ready solution that your competitors can't easily match.
Ultimately, this partnership helps you deliver a much stronger security posture for your clients. We find the holes, and you sell the service that patches them. It creates a sticky, high-value relationship that's tough to replace. For more strategies, check out our guide on cybersecurity for MSPs.
Your Top Questions About Security Training Answered
You've seen the value, but let's talk brass tacks. As an MSP or vCISO, you need straight answers to the questions your team and your clients will ask. Here are direct answers for building a security awareness program that actually works.
How Often Should Clients Conduct Security Awareness Training?
Forget the old "once-a-year" compliance checkbox. That approach is dead. Threats don't take a year off, and neither can your clients' defenses.
Effective security training isn't a one-time event; it's a continuous cycle. It should kick off with a baseline test—like a social engineering assessment—to see where the team stands. From there, it's all about consistent reinforcement. That means monthly or quarterly phishing simulations and short, relevant training modules that don't bog down the workday.
The goal is to build a real security culture. You want secure habits to become second nature, not just something employees cram for before an annual audit.
What Metrics Prove the Training Is Actually Working?
You can't manage what you don't measure. To prove the ROI of your training service, you need to focus on metrics that show a real change in behavior. Vanity metrics won't cut it.
Here are the numbers that matter:
- Phishing Simulation Click-Rates: This is your headline metric. Track the percentage of users who click simulated phishing links over time. A steady drop is hard proof that the training is sinking in.
- Suspicious Email Reporting Rates: This is a huge win. When you see more employees reporting suspicious emails, it means they're shifting from passive targets to active defenders.
- Training Completion Rates: Are people actually doing the training? High completion rates show the content is engaging and that management is backing the program.
- Knowledge Assessment Scores: Short quizzes after training modules help you gauge who's getting it and what topics you might need to hit again.
These data points give you the proof you need to show clients that their investment is measurably reducing their human risk.
Tracking the right metrics is about telling a clear story of progress—showing a client how you’re turning their biggest vulnerability into their most vigilant line of defense.
Can I White Label a Security Awareness Training Platform?
Absolutely. In fact, you should. The channel is full of platforms built specifically for MSPs that allow for full white labeling. This is a critical piece for building out your managed security package.
When you use a white label platform, you give clients a seamless, branded experience. The training emails, the portal, the reports—they all have your logo. This reinforces your brand and positions you as the single source for all their security needs.
It also keeps billing under your roof, strengthens the client relationship, and stops them from getting poached. You control the entire service.
How Does This Fit with Manual Pentesting Services?
They're a perfect match. This is where our channel-only partnership shines. A manual pentesting engagement, especially one with a social engineering component, is the ultimate sales tool for your training service.
Our test delivers the undeniable proof of risk. We find the real human vulnerabilities in a controlled scenario. That unbranded pentesting report we give you becomes your conversation starter.
You can sit down with a client and show them the hard data: "Our third-party test confirmed that your team is vulnerable to this exact phishing attack." Security awareness training is then the logical, necessary solution you provide to fix that problem.
It’s a natural upsell that feels like a strategic recommendation, not a sales pitch. We provide the affordable, fast, and expert testing to find the risk, and you provide the profitable, recurring service that solves it. It’s a powerful combo that helps you hit compliance goals for frameworks like SOC 2 and HIPAA while building a stickier client relationship.
Ready to build a more complete security offering for your clients? At MSP Pentesting, we provide the channel-only, white label pentesting services you need to identify human risk and create the perfect upsell opportunity for your training services.


.avif)
.png)
.png)
.png)

